- Jan 28, 2018
- 2,464
“A browser extension that blocks bad websites without compromising your privacy?”
What sounds like an attempt to square the circle, actually can be done. Almost all browser extensions that aim to block harmful websites send each visited website to cloud servers that match the exact URL/address with a large database of known bad sites. That comes with the advantage of being able to filter sites very thoroughly on the URL level (different from DNS- or host-based filtering such as available in Emsisoft’s Surf Protection feature), but the big downside of that approach is that the creators of such extensions can basically see all the websites you’re visiting and track you throughout all your online activities.
Our development team proves that things can be done in a better, more privacy-conscious way. Emsisoft Browser Security is a brand new extension, currently available for Chrome and Firefox, that not only blocks access to websites that distribute malware, but also prevents phishing attacks that try to steal your passwords.
How it works:
Instead of sending each full website URL to a cloud server for matching, it only sends a calculated hash value of the domain name of each newly visited site to our servers once and then receives a list of matching patterns that are applied locally on your computer. Those patterns are then kept for successive visits of pages on the same host/domain, which not only speeds up the matching significantly, but also means that Emsisoft doesn’t know any of the details of your browsing activity.
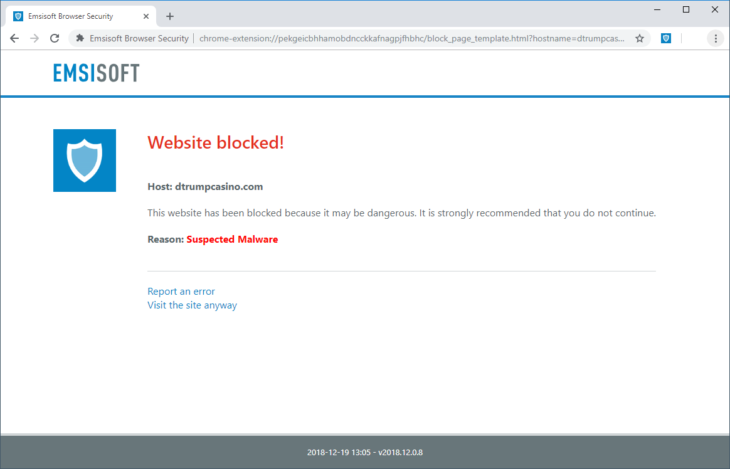
Emsisoft Browser Security for Chrome blocked a malware site.
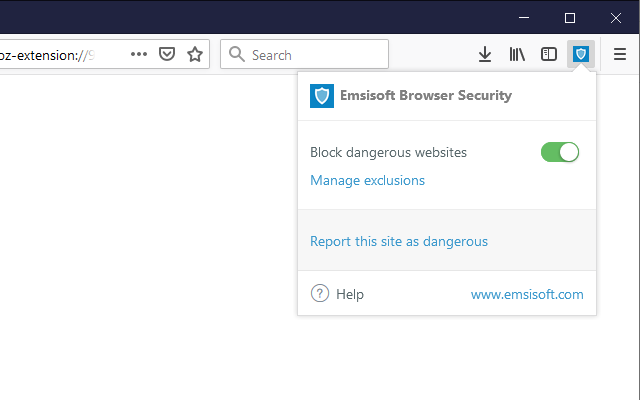
Emsisoft Browser Security for Chrome toolbar popup.
Installation of Emsisoft Browser Security
Emsisoft Browser Security works independently of Emsisoft Anti-Malware and can be obtained free of charge from the extension stores:
Get Emsisoft Browser Security for Chrome
Get Emsisoft Browser Security for Firefox
We’re working on making the extension available for Edge users too.
Emsisoft Anti-Malware asks you to install the extension if it’s missing.
All 2018.12 improvements in a nutshell
Emsisoft Anti-Malware
As always, so long as you have auto-updates enabled in the software, you will receive the latest version automatically during your regularly scheduled updates, which are hourly by default. New users, please download the full installer from our product pages.
Note to Enterprise users: If you have chosen to receive “Delayed” updates in the Update settings for your clients, they will receive the new software version no earlier than 30 days after the regular “Stable” availability. This gives you time to perform internal compatibility tests before a new version gets rolled out to your clients automatically.
Have a great and well-protected day!
What sounds like an attempt to square the circle, actually can be done. Almost all browser extensions that aim to block harmful websites send each visited website to cloud servers that match the exact URL/address with a large database of known bad sites. That comes with the advantage of being able to filter sites very thoroughly on the URL level (different from DNS- or host-based filtering such as available in Emsisoft’s Surf Protection feature), but the big downside of that approach is that the creators of such extensions can basically see all the websites you’re visiting and track you throughout all your online activities.
Our development team proves that things can be done in a better, more privacy-conscious way. Emsisoft Browser Security is a brand new extension, currently available for Chrome and Firefox, that not only blocks access to websites that distribute malware, but also prevents phishing attacks that try to steal your passwords.
How it works:
Instead of sending each full website URL to a cloud server for matching, it only sends a calculated hash value of the domain name of each newly visited site to our servers once and then receives a list of matching patterns that are applied locally on your computer. Those patterns are then kept for successive visits of pages on the same host/domain, which not only speeds up the matching significantly, but also means that Emsisoft doesn’t know any of the details of your browsing activity.

Emsisoft Browser Security for Chrome blocked a malware site.

Emsisoft Browser Security for Chrome toolbar popup.
Installation of Emsisoft Browser Security
Emsisoft Browser Security works independently of Emsisoft Anti-Malware and can be obtained free of charge from the extension stores:
Get Emsisoft Browser Security for Chrome
Get Emsisoft Browser Security for Firefox
We’re working on making the extension available for Edge users too.
Emsisoft Anti-Malware asks you to install the extension if it’s missing.
All 2018.12 improvements in a nutshell
Emsisoft Anti-Malware
- New Emsisoft Browser Security extension.
- Improved stability and compatibility.
- Improved vulnerability resilience.
- Improved product activation.
- Several minor tweaks and fixes.
As always, so long as you have auto-updates enabled in the software, you will receive the latest version automatically during your regularly scheduled updates, which are hourly by default. New users, please download the full installer from our product pages.
Note to Enterprise users: If you have chosen to receive “Delayed” updates in the Update settings for your clients, they will receive the new software version no earlier than 30 days after the regular “Stable” availability. This gives you time to perform internal compatibility tests before a new version gets rolled out to your clients automatically.
Have a great and well-protected day!