@upnorth shared a sample here that was the basis for this article. Enjoy 
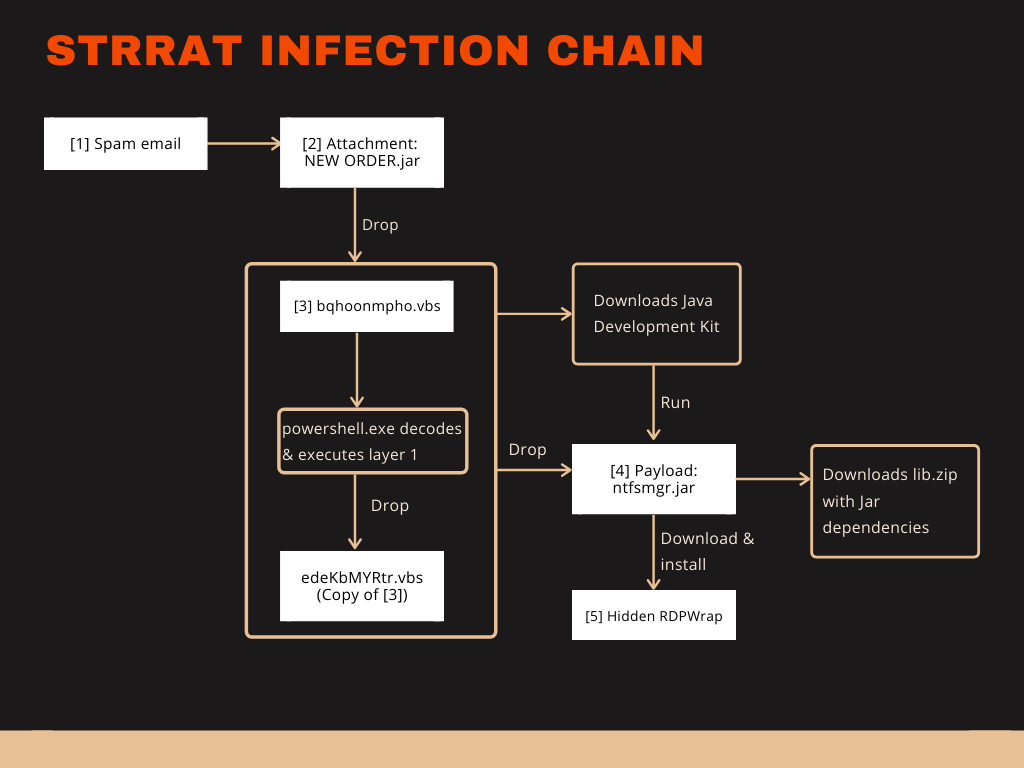
This Java based malware installs RDPWrap, steals credentials, logs keystrokes and remote controls Windows systems. It may soon be capable to infect without Java installed.
Java is not commonly used for malware anymore and its runtime environment is not installed on as many systems as it was in the past. The more it seems surprising when new Java based malware families arise.
I am an active member of the forum malwaretips.com. A member of this forum, upnorth, shared a sample[2] to be used for testing Antivirus products. This sample[2] caught my attention. It was a Java archive but described as WSHRat. I expected to see either a dropper for a known WSH based RAT or another Adwind variant. I was wrong. This sample[2] is a new breed of Java RAT. One that is prepared to not rely on a preinstalled Java Runtime Environment (JRE).


