silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,743
- 123,908
- 8,399
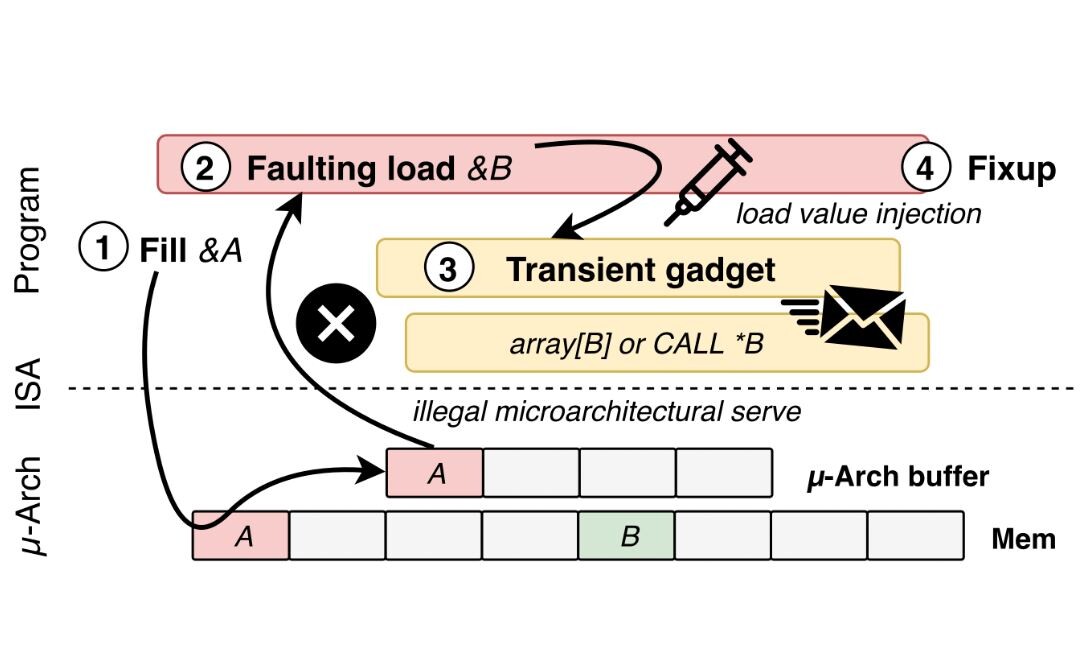
A novel class of attack techniques against modern Intel processors can allow threat actors to inject malicious data into applications via transient-execution attacks and steal sensitive data according to researchers.
The vulnerability dubbed LVI (short for Load Value Injection) and tracked as CVE-2020-0551 was discovered and reported to Intel on April 4, 2019, by researchers at the Worcester Polytechnic Institute, imec-DistriNet/KU Leuven, Graz University of Technology, University of Michigan, University of Adelaide and Data61, in no particular order.
Bitdefender researchers also independently discovered one variant of attack in the LVI class (LVI-LFB) and reported it to Intel in February 2020.
LVI attacks let attackers change the normal execution of programs to steal data that is normally meant to be kept private within SGX enclaves. Sensitive information that can be stolen this way includes passwords, private keys of certificates, and more.
Even though the Intel Software Guard eXtensions (SGX) feature in modern Intel processors that enables apps to run within secure and isolated enclaves is not necessary to launch an LVI attack, its presence makes the attack a lot easier.
"While LVI attacks in non-SGX environments are generally much harder to mount, we consider none of the adversarial conditions for LVI to be unique to Intel SGX," the researchers explain.