- May 13, 2017
- 76
Security researchers have finally got their hands on samples of two new strains of Mac malware that have been offered through Malware-as-a-Service (MaaS) portals on the Dark Web for almost two weeks now.
Both portals were launched on May 25 and were discovered by your reporter during a routine scan of the Dark Web. The first site is named MacSpy and peddles Mac spyware, while the second is named MacRansom, and is renting ransomware in a classic RaaS scheme.
The pair is the work of the same malware developer, and the websites are almost identical if you're not paying close attention.
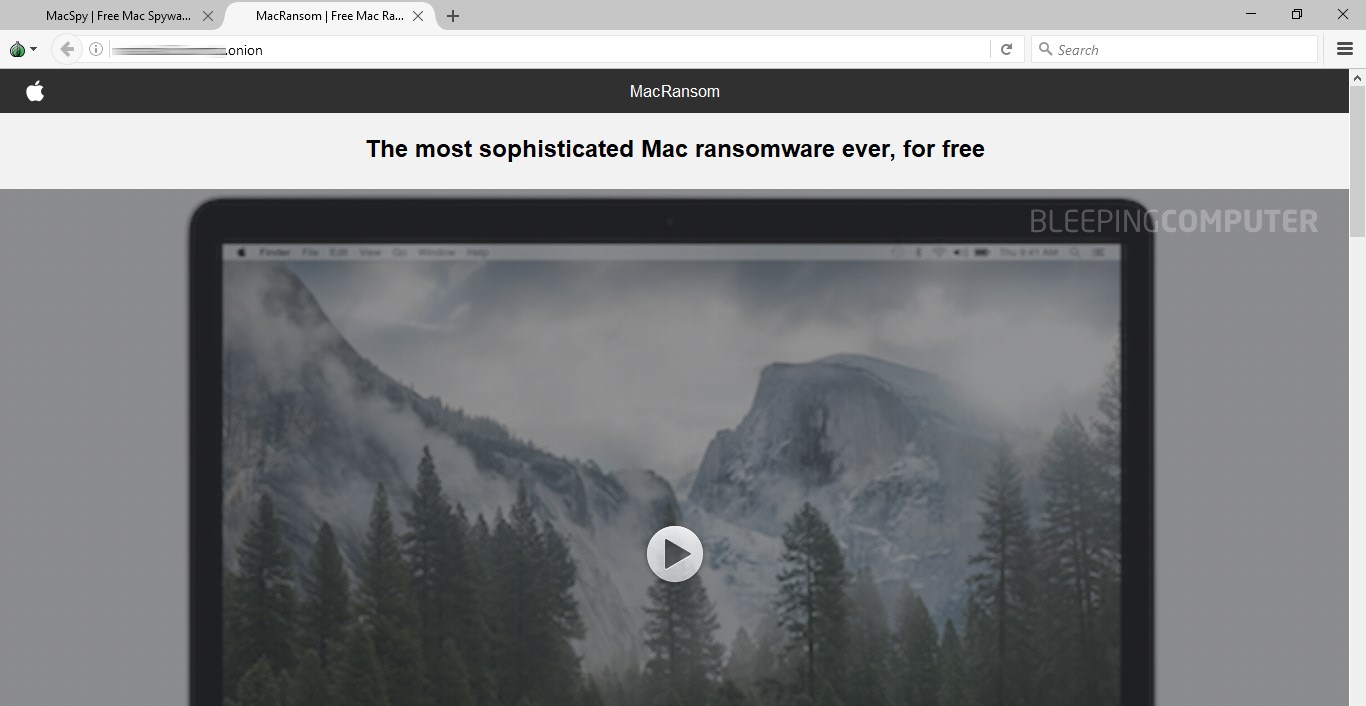
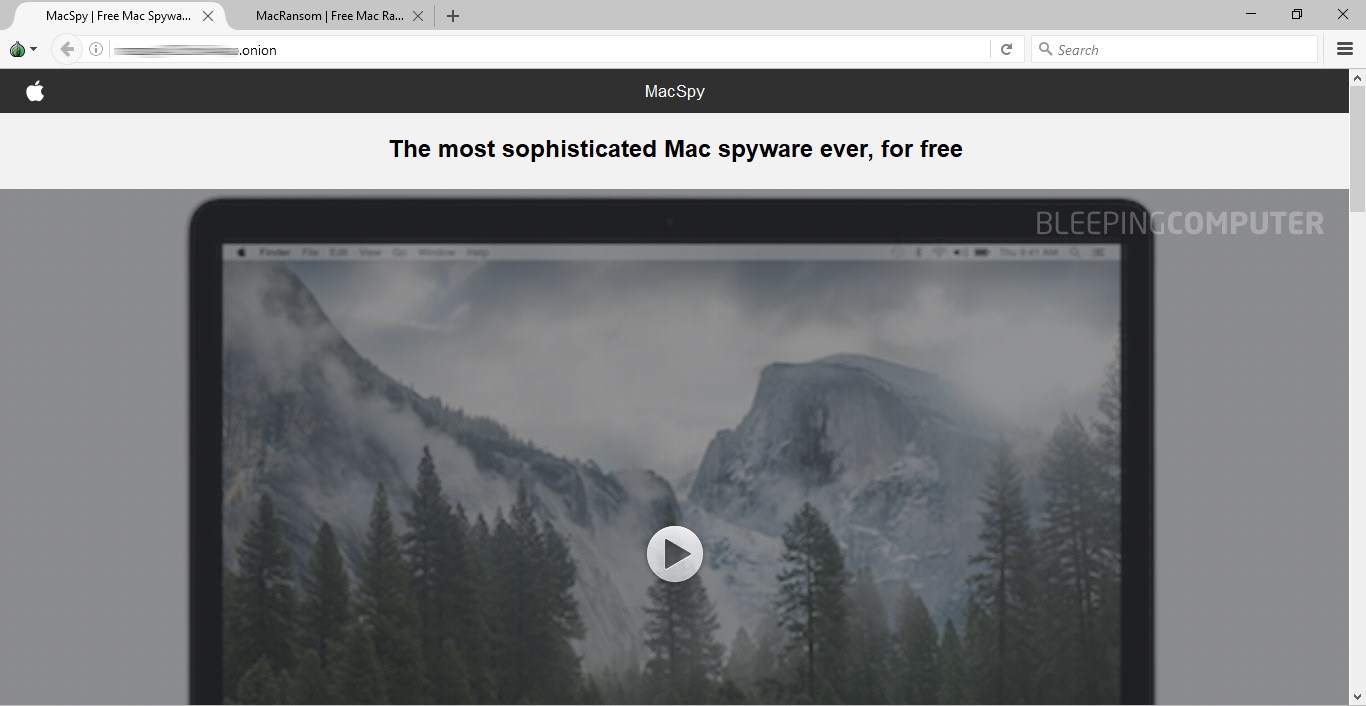
Both websites are run in a "closed" manner, meaning crooks have to contact the malware author to receive demo packages and negotiate going rates.
While Bleeping tried numerous times from numerous emails, it was our friends from Fortinet and AlienVault that got their hands on fully-working samples of MacRansom and MacSpy, respectively.
MacSpy, MacRansom need some more work
Both companies have published research breaking down the two malware strains they received, and both reached the same conclusion, which is that MacRansom and MacSpy are the work of an inexperienced coder, who despite creating two MaaS portals, has not focused enough on improving the quality of his code.
Below are some issues spotted by researchers:
MacRansom
⟡ MacRansom author needs to approve each client, negotiate fees, and manually build each ransomware sample, defeating the purpose of running a RaaS in the first place.
⟡ Ransomware uses symmetric encryption, with the encryption keys included in the ransomware's source code.
⟡ One of these encryption keys is permutated with a random number and dropped from memory after the encryption ends. This means the ransomware loses one of the two encryption keys.
⟡ The ransomware doesn't communicate with a C&C server, meaning there's no way for the ransomware author to decrypt locked files.
⟡ Ransomware doesn't use a Tor-based payment panel but requires users to get in contact with the renter via email.
⟡ The ransomware file is not digitally signed, meaning it will trigger security alerts when executed on a standard macOS installation.
[MacRansom report here]
MacSpy
⟡ MacSpy author appears to have copy-pasted code from Stack Overflow
⟡ Spyware payload is not digitally signed, meaning it will trigger security alerts when executed on a standard macOS installation.
[MacSpy report here]
Overall, MacSpy seems to be a better-coded tool, but Mac users should be scared more of MacRansom as the ransomware has the potential to permanently wreck user files if ever deployed in live campaigns.
Currently, none of these two appear to be part of any active distribution campaigns, most likely due to the grueling process, someone has to go through to get their hands on one of the payloads.
The Mac malware market is slowly expanding
Security reporter Ruben Dodge, who also took a look at Fortinet's MacRansom report, also shares the company's opinion.
"Personally from what I see [...] it doesn't look that complex," Dodge told Bleeping Computer on Twitter. "Its got very basic checks for virtual machines."
"It may not take off," the researcher said about the MacRansom RaaS becoming popular. "However, I do believe its only a matter of time [until another RaaS does]. There is a market for it. Mac consumer use is growing."
"There's an ideological shift for Mac and iPhone as being seen as the more friendly OS for older people. [...] It is a market that will be targeted. There are too many less technical people using it not to make it a 'ripe' target for threat actors," Dodge added.
And the researcher is right. In the past year, we've seen Mac malware, and especially Mac ransomware growing from a simple demo (Mabouia) to an active threat (KeRanger and Patcher). There's also this malware author working on a brand new cross-OS ransomware, which he said he plans to offer through a RaaS portal hosted on the Dark Web over the summer.
The number of Macs has grown, and so has the number of Mac-targeting malware. The launch of MaaS portals, even if hard to use and engage with as MacSpy and MacRansom, will drive more crooks towards the Mac userbase, and will lower the entry bar for some individuals and groups that had no previous experience with creating Mac malware.
Both portals were launched on May 25 and were discovered by your reporter during a routine scan of the Dark Web. The first site is named MacSpy and peddles Mac spyware, while the second is named MacRansom, and is renting ransomware in a classic RaaS scheme.
The pair is the work of the same malware developer, and the websites are almost identical if you're not paying close attention.


Both websites are run in a "closed" manner, meaning crooks have to contact the malware author to receive demo packages and negotiate going rates.
While Bleeping tried numerous times from numerous emails, it was our friends from Fortinet and AlienVault that got their hands on fully-working samples of MacRansom and MacSpy, respectively.
MacSpy, MacRansom need some more work
Both companies have published research breaking down the two malware strains they received, and both reached the same conclusion, which is that MacRansom and MacSpy are the work of an inexperienced coder, who despite creating two MaaS portals, has not focused enough on improving the quality of his code.
Below are some issues spotted by researchers:
MacRansom
⟡ MacRansom author needs to approve each client, negotiate fees, and manually build each ransomware sample, defeating the purpose of running a RaaS in the first place.
⟡ Ransomware uses symmetric encryption, with the encryption keys included in the ransomware's source code.
⟡ One of these encryption keys is permutated with a random number and dropped from memory after the encryption ends. This means the ransomware loses one of the two encryption keys.
⟡ The ransomware doesn't communicate with a C&C server, meaning there's no way for the ransomware author to decrypt locked files.
⟡ Ransomware doesn't use a Tor-based payment panel but requires users to get in contact with the renter via email.
⟡ The ransomware file is not digitally signed, meaning it will trigger security alerts when executed on a standard macOS installation.
[MacRansom report here]
MacSpy
⟡ MacSpy author appears to have copy-pasted code from Stack Overflow
⟡ Spyware payload is not digitally signed, meaning it will trigger security alerts when executed on a standard macOS installation.
[MacSpy report here]
Overall, MacSpy seems to be a better-coded tool, but Mac users should be scared more of MacRansom as the ransomware has the potential to permanently wreck user files if ever deployed in live campaigns.
Currently, none of these two appear to be part of any active distribution campaigns, most likely due to the grueling process, someone has to go through to get their hands on one of the payloads.
The Mac malware market is slowly expanding
Security reporter Ruben Dodge, who also took a look at Fortinet's MacRansom report, also shares the company's opinion.
"Personally from what I see [...] it doesn't look that complex," Dodge told Bleeping Computer on Twitter. "Its got very basic checks for virtual machines."
"It may not take off," the researcher said about the MacRansom RaaS becoming popular. "However, I do believe its only a matter of time [until another RaaS does]. There is a market for it. Mac consumer use is growing."
"There's an ideological shift for Mac and iPhone as being seen as the more friendly OS for older people. [...] It is a market that will be targeted. There are too many less technical people using it not to make it a 'ripe' target for threat actors," Dodge added.
And the researcher is right. In the past year, we've seen Mac malware, and especially Mac ransomware growing from a simple demo (Mabouia) to an active threat (KeRanger and Patcher). There's also this malware author working on a brand new cross-OS ransomware, which he said he plans to offer through a RaaS portal hosted on the Dark Web over the summer.
The number of Macs has grown, and so has the number of Mac-targeting malware. The launch of MaaS portals, even if hard to use and engage with as MacSpy and MacRansom, will drive more crooks towards the Mac userbase, and will lower the entry bar for some individuals and groups that had no previous experience with creating Mac malware.