silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,178
A new information-stealing malware has set its sights on Apple's macOS operating system to siphon sensitive information from compromised devices.
Dubbed MacStealer, it's the latest example of a threat that uses Telegram as a command-and-control (C2) platform to exfiltrate data. It primarily affects devices running macOS versions Catalina and later running on M1 and M2 CPUs.
"MacStealer has the ability to steal documents, cookies from the victim's browser, and login information," Uptycs researchers Shilpesh Trivedi and Pratik Jeware said in a new report.
First advertised on online hacking forums at the start of the month, it is still a work in progress, with the malware authors planning to add features to capture data from Apple's Safari browser and the Notes app.
In its current form, MacStealer is designed to extract iCloud Keychain data, passwords and credit card information from browsers like Google Chrome, Mozilla Firefox, and Brave. It also features support for harvesting Microsoft Office files, images, archives, and Python scripts.
The exact method used to deliver the malware is not known, but it is propagated as a DMG file (weed.dmg) that, when executed, opens a fake password prompt to harvest the passwords under the guise of seeking access to the System Settings app.
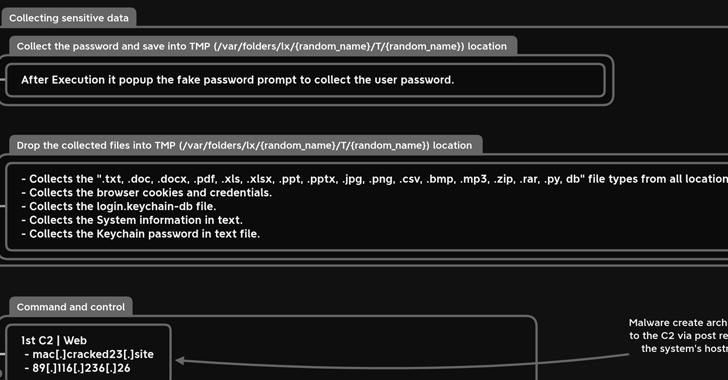
New MacStealer macOS Malware Steals iCloud Keychain Data and Passwords
New MacStealer malware targets Apple devices running macOS Catalina & later, M1/M2 CPUs and uses Telegram for C&C, stealing documents, browser cookies

