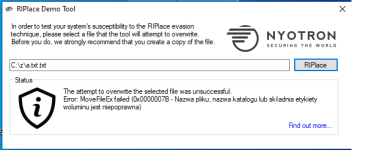
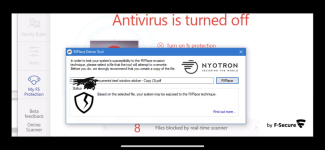
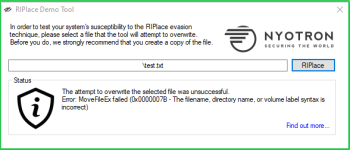
A new ransomware bypass technique called RIPlace requires only a few lines of code to bypass ransomware protection features built into many security products and Windows 10.
With ransomware being such an epidemic for consumers and businesses, security software and Windows have built ransomware protections features into their software.
A new technique called RIPlace was disclosed today by security researchers Daniel Prizmant, Guy Meoded, Freddy Ouzan, and Hanan Natan at endpoint protection firm
Nyotron that encrypts files in a way that these ransomware protection solutions miss and thus the files become encrypted.
Discovered in 2018, Nyotron responsibly disclosed the RIPlace bypass technique to security software vendors and Microsoft, but the researchers were told that since no ransomware was using, it was seen as a non-issue.