silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,731
- 123,854
- 8,399
A new backdoor was observed using the Github Gist service and the Slack messaging system as communication channels with its masters, as well as targeting a very specific type of victim using a watering hole attack.
The backdoor dubbed SLUB by the Trend Micro Cyber Safety Solutions Team who detected it in the wild is part of a multi-stage infection process designed by capable threat actors who programmed it in C++.
SLUB uses statically-linked curl, boost, and JsonCpp libraries for performing HTTP request, "extracting commands from gist snippets," and "parsing Slack channel communication."
The campaign recently observed by the Trend Micro security researchers abusing the Github and Slack uses a multi-stage infection process.
Windows exploits used to compromise targets in watering hole attacks
SLUB's masters added an exploit for the CVE-2018-8174 remote code execution vulnerability present the Windows VBScript engine and patched in May 2018 to a compromised website, allowing them to drop and launch the first stage in the form of a downloader camouflaged as a DLL file using PowerShell.
In addition, as detailed by Trend Micro in their analysis, "the watering hole chosen by the attackers can be considered interesting for those who follow political activities, which might give a glimpse into the nature of the groups and individuals that the attackers are targeting."
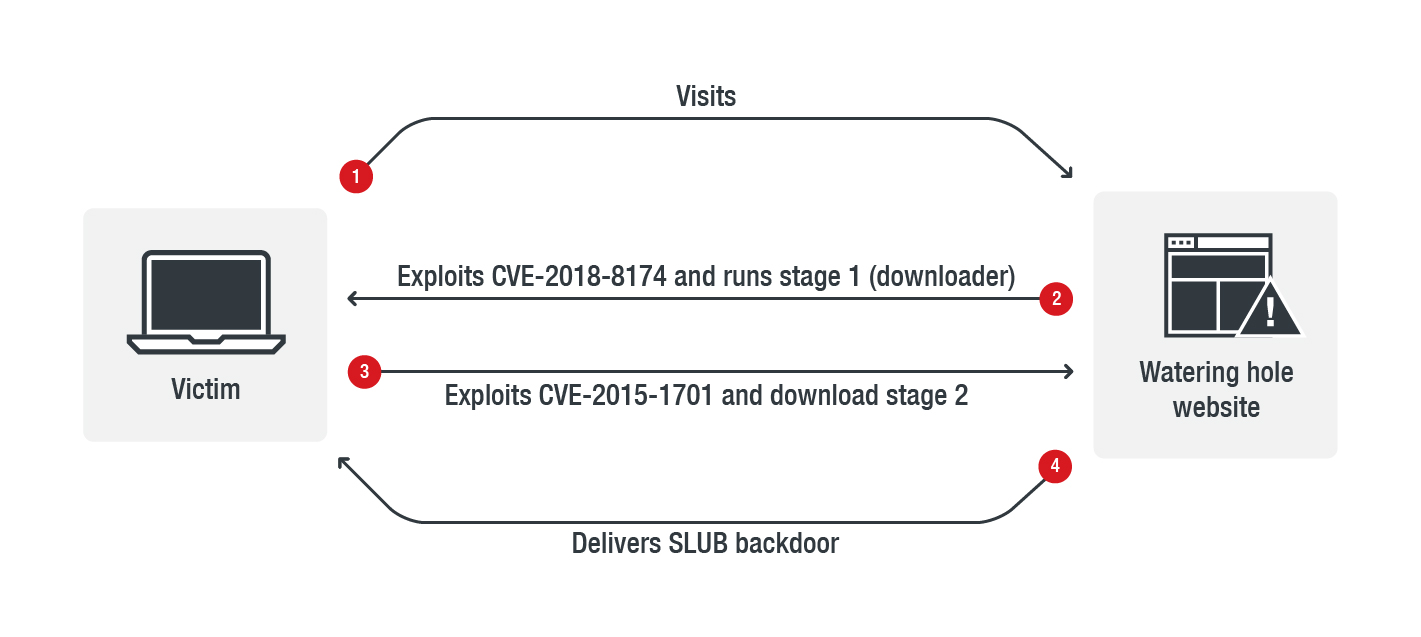
Once launched, the first stage downloader will check for anti-malware solutions on the compromised machine and will automatically exit if it detects any. This is most likely a precautionary measure implemented by the threat actors for future SLUB campaigns seeing that, as noted by Trend Micro, the malware was not detected by anti-malware products.
It will also download and immediately execute the second stage of the infection, the SLUB malware, and it also exploits the CVE-2015-1701 vulnerability in the Windows kernel-mode drivers to gain elevated privileges –uses a modified version of a publicly available exploit for the Win32k LPE vulnerability.