- Aug 17, 2017
- 1,610
Fortinet’s FortiGuard Labs recently uncovered a new cybersecurity threat: a malware known dubbed “Vcurms.” The attackers behind Vcurms malware have employed sophisticated tactics, using email as their command and control center and leveraging public services such as AWS and GitHub to store the malicious software. Additionally, they have employed a commercial protector to evade detection, indicating a concerted effort to maximize the malware’s impact.
This campaign primarily targets platforms with Java installed, posing a risk to any organization utilizing such systems. The severity of the threat cannot be understated, as successful infiltration grants attackers full control over compromised systems.
The modus operandi of the attackers involves luring users to download a malicious Java downloader, which serves as a vector for spreading Vcurms and STRRAT, a trojan previously found to be posing as fake ransomware infection to steal data. Vcurms also exhibits notable similarities with the Rude Stealer malware but distinguishes itself through its unique transmission methods and targeted data acquisition. It prioritizes stealing sensitive information from popular browsers like Chrome, Brave, Edge, Vialdi, Opera, OperaGX, Firefox, etc. and applications, including Discord and Steam.
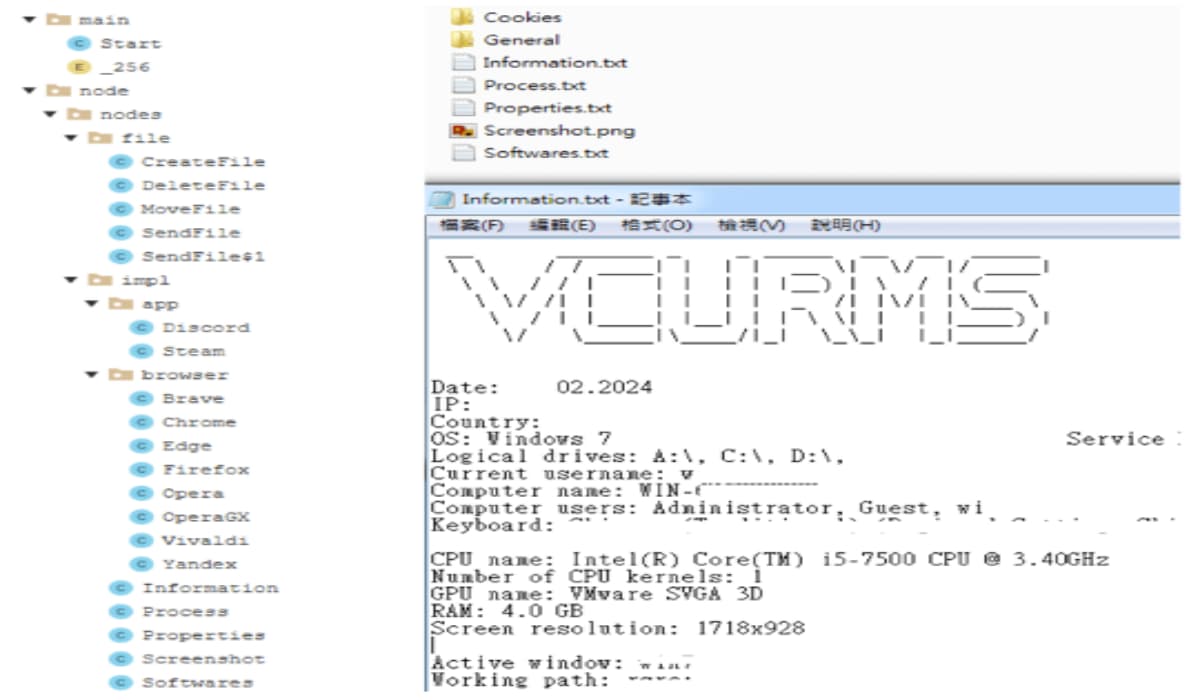
New Vcurms Malware Targets Popular Browsers for Data Theft
Follow us on Twitter (X) @Hackread - Facebook @ /Hackread
 www.hackread.com
www.hackread.com
