The number of cloud-based Microsoft user-accounts that came under cyberattack in the first quarter of this year was four times what it had been during the same period last year, the Redmond, Washington-based tech giant revealed in its latest security statistics.
In the publication, the company also warns about the increasing “weaponization” of cloud services by cybercrime groups and other hackers.
The latest volume of Microsoft Security Intelligence Report presents incident data from January to March this year across the company’s billion-plus device ecosystem. For the first time, the data is broken out into endpoint and cloud segments.
“Today, most enterprises now have hybrid environments and it’s important to provide more holistic visibility,” the company’s security team states in a blog post.
The post also says the company will now share data quarterly, as opposed to every six months “as we shift our focus to delivering improved and more frequent updates in the future.”
No one from Microsoft’s press team responded to emails requesting comment.
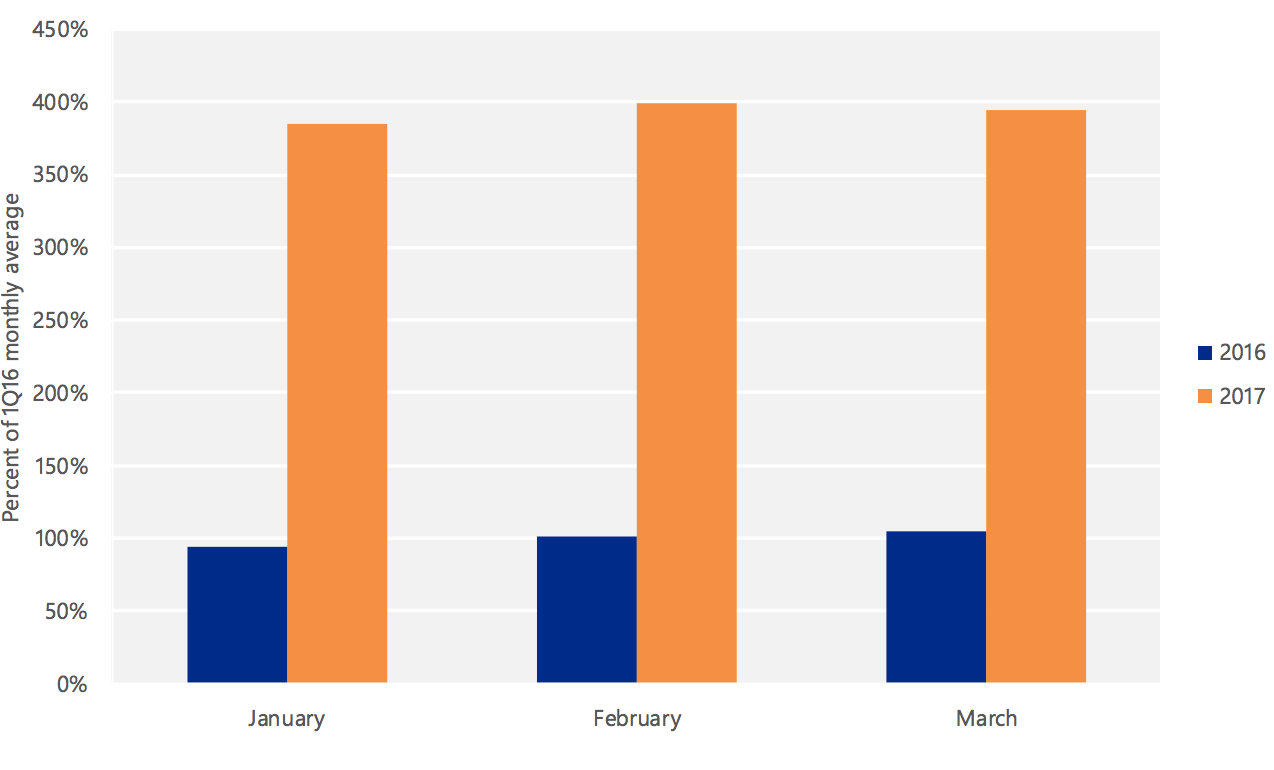
A chart comparing the amount of attacks Microsoft-based logins between the first quarter of 2016 and first quarter of 2017. (Microsoft)
The report also says that “the number of Microsoft account sign-ins attempted from malicious IP addresses has increased by 44 percent” since the same time last year.
Many of these efforts attempt to to use passwords and/or usernames stolen in other major breaches in the hopes that users have reused the same password.
“Microsoft automated systems detect and block millions of password attacks each day,” states the report. “When an attacker is observed using a valid credential, the request is challenged and the user is required to provide additional validation in order to sign in. Attackers, for their part, can be sophisticated and skilled at mimicking real users, making the task of safeguarding accounts a constantly evolving challenge.”
The company recommends various identity security measures to combat such efforts — including multi-factor authentication.
The report also warns about what it calls “cloud weaponization.” In such a scenario, “an attacker establishes a foothold within a cloud infrastructure by compromising and taking control of one or more virtual machines. The attacker can then use these virtual machines to launch attacks, including brute force attacks against other virtual machines, spam campaigns that can be used for email phishing attacks, reconnaissance such as port scanning to identify new attack targets, and other malicious activities.”
Cloud security vendors have previously warned about these so-called “cloud-on-cloud” attacks, which can be very stealthy and hard to detect.
The report analyses outbound malicious traffic from the Microsoft Azure cloud, and concludes that almost a quarter of it is connected with brute force attempts, almost 20 percent with spam email sending and more than half is communication with malware command and control servers — likely indicating an infection on a virtual machine, which is the first step in the attack.
As for inbound attacks, during the first quarter, more than two-thirds came from IP addresses in China and the United States, at 35.1 percent and 32.5 percent, respectively. Korea was a distant third origin at 3.1 percent, followed by 116 other countries and regions.
Newest Microsoft report warns on the 'weaponization' of cloud - CyberScoop
In the publication, the company also warns about the increasing “weaponization” of cloud services by cybercrime groups and other hackers.
The latest volume of Microsoft Security Intelligence Report presents incident data from January to March this year across the company’s billion-plus device ecosystem. For the first time, the data is broken out into endpoint and cloud segments.
“Today, most enterprises now have hybrid environments and it’s important to provide more holistic visibility,” the company’s security team states in a blog post.
The post also says the company will now share data quarterly, as opposed to every six months “as we shift our focus to delivering improved and more frequent updates in the future.”
No one from Microsoft’s press team responded to emails requesting comment.

A chart comparing the amount of attacks Microsoft-based logins between the first quarter of 2016 and first quarter of 2017. (Microsoft)
The report also says that “the number of Microsoft account sign-ins attempted from malicious IP addresses has increased by 44 percent” since the same time last year.
Many of these efforts attempt to to use passwords and/or usernames stolen in other major breaches in the hopes that users have reused the same password.
“Microsoft automated systems detect and block millions of password attacks each day,” states the report. “When an attacker is observed using a valid credential, the request is challenged and the user is required to provide additional validation in order to sign in. Attackers, for their part, can be sophisticated and skilled at mimicking real users, making the task of safeguarding accounts a constantly evolving challenge.”
The company recommends various identity security measures to combat such efforts — including multi-factor authentication.
The report also warns about what it calls “cloud weaponization.” In such a scenario, “an attacker establishes a foothold within a cloud infrastructure by compromising and taking control of one or more virtual machines. The attacker can then use these virtual machines to launch attacks, including brute force attacks against other virtual machines, spam campaigns that can be used for email phishing attacks, reconnaissance such as port scanning to identify new attack targets, and other malicious activities.”
Cloud security vendors have previously warned about these so-called “cloud-on-cloud” attacks, which can be very stealthy and hard to detect.
The report analyses outbound malicious traffic from the Microsoft Azure cloud, and concludes that almost a quarter of it is connected with brute force attempts, almost 20 percent with spam email sending and more than half is communication with malware command and control servers — likely indicating an infection on a virtual machine, which is the first step in the attack.
As for inbound attacks, during the first quarter, more than two-thirds came from IP addresses in China and the United States, at 35.1 percent and 32.5 percent, respectively. Korea was a distant third origin at 3.1 percent, followed by 116 other countries and regions.
Newest Microsoft report warns on the 'weaponization' of cloud - CyberScoop