I'm an employee of Invincea and posting this message on behalf of the Sandboxie Team...
Thank you, IcYSeptember, for bringing this to our attention! We at Sandboxie/Invincea take these matters seriously and investigate all feedback to provide a safe computing environment for our users.
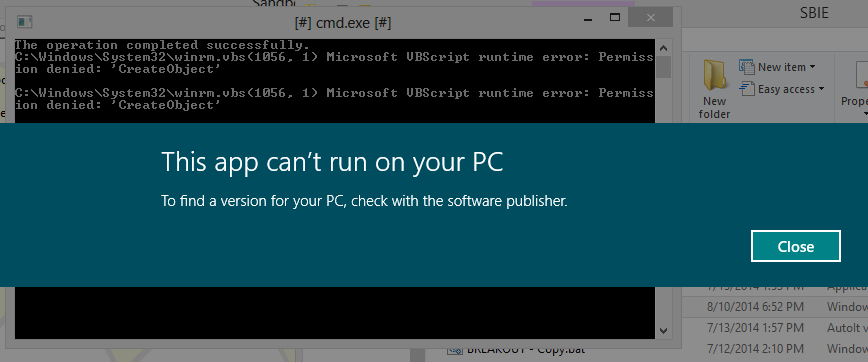
In our analysis of the provided information, the user takes advantage of the default configuration of an existing Microsoft-provided Windows Remote Management service (WS-Management) running on the Windows host. He is using an administrator-privileged client (winrs) running in the sandbox to connect to the host itself over TCP to the management service (winrm) running on the host, thereby creating a sandbox to host communication. (Windows Remote Management service is a Microsoft-provided service that allows for remote access to another host to perform management functions.) As you can imagine, any remote management service can be used to perform both positive and negative actions on the host itself.
This access does not take advantage of a vulnerability (0-day or other) or a defect in Sandboxie in how it isolates the file system, registry, or running processes from the host.
In fact, there are many legitimate use cases for sandboxed processes to communicate with a network service on the same host. Additionally as a point of concern, this type of remote management access can be performed completely outside of Sandboxie whereby one host on a network can connect to the Windows Remote Management service running on a second host on the same network, for example, at a public WiFi hotspot.
We recommend safe configurations of your PC’s operating system and running applications working in conjunction with the isolation protection offered by Sandboxie. Any of these configurations would block the access that was demonstrated:
- Disable default services on your PC that you do not use or which presents a security risk.
- If remote management is needed, configure the service to request a user-provided strong password.
- Install and configure a third-party firewall to block localhost-initiated network communications to local services (on loopback and the active network adapter)
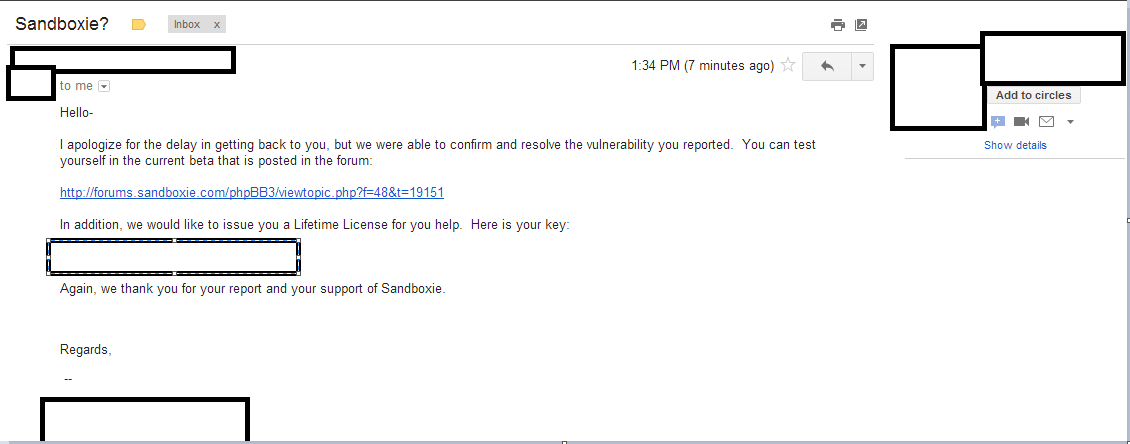
We did implement a control in the just-released Sandboxie 4.13 beta version that specifically blocks running the winrs client in the sandbox altogether, among other edge cases we found in our analysis to provide even more protection. We are continuously evaluating where we can have Sandboxie implement security control over the risk created by default Windows services to better protect our users.
Thank you for bringing this to our attention and safe browsing!
Sandboxie Team