- Dec 27, 2016
- 1,480
Despite the reach and disruptiveness of the ransomware, which seemed to indicate it was made by sophisticated attackers, the hackers didn't set it up in a way that it'd be easy for victims to pay.
In an unexpected twist on Tuesday, the hackers gave their first sign of life since the attack. At 10:10 PM UTC, the hackers emptied the bitcoin wallet they were using to receive ransom payments, moving more than $10,000 to a different wallet. A few minutes earlier, the hackers also sent twosmall payments to the bitcoin wallets of Pastebin and DeepPaste, two websites that let people post text online and are sometimes used by hackers to make announcements.
At 9:23 PM UTC, and 9:20 PM UTC, around 11 minutes and 12 minutes before the hackers made the two donations, someone claiming to be behind NotPetya posted an announcement on DeepPaste and Pastebin.
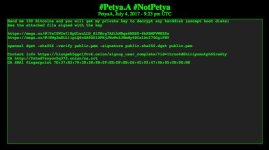
The authors of the announcement asked for 100 bitcoin (roughly $256,000 at the time of writing) in exchange for the private key that supposedly decrypts any file encrypted with NotPetya. Curiously, the authors didn't provide a bitcoin address where to send the payment, but did publish a link to a dark web chatroom where people could contact them.
In an interview in the chatroom, someone purporting to be one of the hackers told Motherboard that the price was so high because it's for the key "to decrypt all computers."
Are you interested in my offer?" they asked, offering to decrypt a file for free as a test.
Motherboard could not confirm that the people who posted the announcement, as well as the people in the chatroom, were the hackers behind NotPetya. With the help of a security researcher, Motherboard provided the alleged hackers with an encrypted file, and the corresponding readme.txt file created with NotPetya, but the alleged hackers did not immediately provide the decrypted file.
Matt Suiche, a security researcher who has analyzed NotPetya, was skeptical about the alleged hackers' motives, saying they are just "trolling journalists."
"This is a fear, uncertainty and doubt case," Suiche, who's the founder of Comae Technologies, told Motherboard in an online chat. "This is the attackers' clear attempt to further confuse the audience, by changing the wiper narrative into a ransomware one again."
In an unexpected twist on Tuesday, the hackers gave their first sign of life since the attack. At 10:10 PM UTC, the hackers emptied the bitcoin wallet they were using to receive ransom payments, moving more than $10,000 to a different wallet. A few minutes earlier, the hackers also sent twosmall payments to the bitcoin wallets of Pastebin and DeepPaste, two websites that let people post text online and are sometimes used by hackers to make announcements.
At 9:23 PM UTC, and 9:20 PM UTC, around 11 minutes and 12 minutes before the hackers made the two donations, someone claiming to be behind NotPetya posted an announcement on DeepPaste and Pastebin.

The authors of the announcement asked for 100 bitcoin (roughly $256,000 at the time of writing) in exchange for the private key that supposedly decrypts any file encrypted with NotPetya. Curiously, the authors didn't provide a bitcoin address where to send the payment, but did publish a link to a dark web chatroom where people could contact them.
In an interview in the chatroom, someone purporting to be one of the hackers told Motherboard that the price was so high because it's for the key "to decrypt all computers."
Are you interested in my offer?" they asked, offering to decrypt a file for free as a test.
Motherboard could not confirm that the people who posted the announcement, as well as the people in the chatroom, were the hackers behind NotPetya. With the help of a security researcher, Motherboard provided the alleged hackers with an encrypted file, and the corresponding readme.txt file created with NotPetya, but the alleged hackers did not immediately provide the decrypted file.
Matt Suiche, a security researcher who has analyzed NotPetya, was skeptical about the alleged hackers' motives, saying they are just "trolling journalists."
"This is a fear, uncertainty and doubt case," Suiche, who's the founder of Comae Technologies, told Motherboard in an online chat. "This is the attackers' clear attempt to further confuse the audience, by changing the wiper narrative into a ransomware one again."

