- Jul 3, 2015
- 8,153
I have done everything according to your settings but unfortunately one malware can be written to disk.No malware is active but still managed to enroll.Can you advise me what settings do in novirustnx that this malware can not be written to disk thanks.Alternatively I could send a sample pm:
It is in fact my only defense.
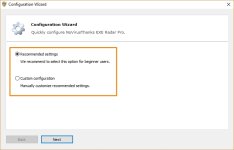
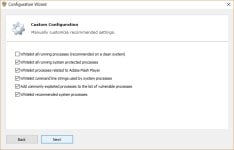
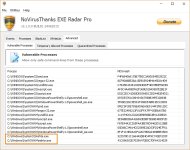
vulnerable process standart
novirustnx
https://www.hybrid-analysis.com/sam...9b1f72e815e05337ba6c35ac298?environmentId=100
Hi, I can't analyse this in-depth, maybe @Umbra can handle it?
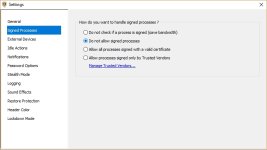
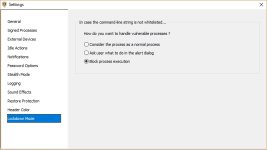
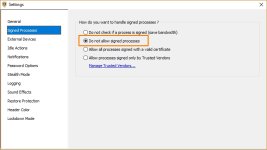
But I can tell you in a general way that NVT ERP does not block all types of executable files. It primarily blocks exe files, and in addition, the default vulnerable processes list will produce prompts whenever a script interpreter is invoked, unless you specifically whitelisted that particular command-line. So you are covered for the scripts, too.
But it will not block the rarer executable file types by default. For instance, HTA files are not blocked or prompted.
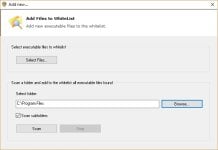
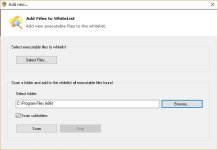
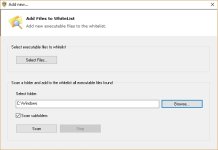
The tweak for this is to add the corresponding process to the vulnerable processes list.
For instance, in order to get a prompt everytime a HTA wants to execute, you would add MSHTA.exe to the VPL. You need to add it both in system32 and in syswow64.
I hope someone else can analyse what went wrong here.