@NoVirusThanks
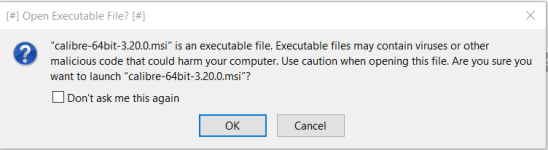
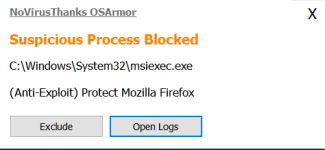
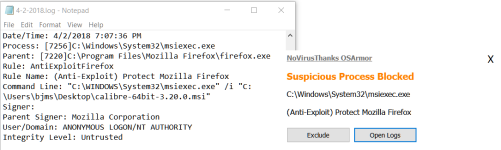
Thanks, the previous FPs have been fixed but now I have this:
Date/Time: 04/04/2018 11:39:55 a.m.
Process: [3704]C:\Windows\System32\dllhost.exe
Parent: [764]C:\Windows\System32\svchost.exe
Rule: BlockUnknownProcessesOnWindowsFolder
Rule Name: Block unknown processes on Windows folder
Command Line: C:\Windows\system32\DllHost.exe /Processid:{F9717507-6651-4EDB-BFF7-AE615179BCCF}
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Date/Time: 04/04/2018 11:55:39 a.m.
Process: [2340]C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe
Parent: [2652]C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe
Rule: BlockProcessesExecutedFromCSC
Rule Name: Block processes executed from C Sharp compiler (csc.exe)
Command Line: C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\PC\AppData\Local\Temp\RES3C2F.tmp" "c:\Users\PC\AppData\Local\Temp\CSC3C2E.tmp"
Signer: Microsoft Corporation
Parent Signer: Microsoft Corporation
User/Domain: PC/PC
Integrity Level: Medium
Date/Time: 04/04/2018 11:50:20 a.m.
Process: [3944]C:\Windows\System32\control.exe
Parent: [1596]C:\Windows\explorer.exe
Rule: BlockSuspiciousCmdlines
Rule Name: Block execution of suspicious command-line strings
Command Line: "C:\Windows\System32\control.exe" "C:\Windows\system32\timedate.cpl",
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium