Boringly quiet here. No detection logs since April 9. Nice. I keep checking the tray to see if I've disabled OSA  All non-orange/red options selected.
All non-orange/red options selected.
NoVirusThanks OSArmor
- Thread starter Evjl's Rain
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I've been using for close to 2 months now, not one detection yet. However, this due mainly to my computer habits and not a fault of the actual program.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
No, the powershell commands were blocked, see: NoVirusThanks OSArmorIt wasn't?
OS Armor is a strong layer of defense. Andreas is constantly adding recognition strings to commands used to bypass PC defenses (antivirus solutions).
Most fileless malware and ransomware use remote access and build-in shells like Windows Management Instrumentation, powershell and dotNet which can't be turned of like old command shells as wscript and cmd.
The changes of running into these type of malware is not that big when you apply safe HEX and have decent security in place. But the price (free) and low performance impact make OS Armor something to consider for any setup.
Now with latest option to allow only signed processes in user space, one only needs to add addtional partitions/drives to your custom block rules, it is as easy as this, where X is the drive letter: [%PROCESSFILEPATH%: X:\*]
So when you split your harddisk into C for programs and D for files it would look like: [%PROCESSFILEPATH%: D:\*]
Great job Andreas @NoVirusThanks thanks
Most fileless malware and ransomware use remote access and build-in shells like Windows Management Instrumentation, powershell and dotNet which can't be turned of like old command shells as wscript and cmd.
The changes of running into these type of malware is not that big when you apply safe HEX and have decent security in place. But the price (free) and low performance impact make OS Armor something to consider for any setup.
Now with latest option to allow only signed processes in user space, one only needs to add addtional partitions/drives to your custom block rules, it is as easy as this, where X is the drive letter: [%PROCESSFILEPATH%: X:\*]
So when you split your harddisk into C for programs and D for files it would look like: [%PROCESSFILEPATH%: D:\*]
Great job Andreas @NoVirusThanks thanks
I want to block writing to "G" partition by all except Signer: Microsoft.Now with latest option to allow only signed processes in user space, one only needs to add addtional partitions/drives to your custom block rules, it is as easy as this, where X is the drive letter: [%PROCESSFILEPATH%: X:\*]
So when you split your harddisk into C for programs and D for files it would look like: [%PROCESSFILEPATH%: D:\*]
So I entered a block... simply....
[%PROCESSFILEPATH%: G:\*]
and ran a program that normally writes to "G" and there was no interception. What am I doing wrong?
Here is a new v1.4 (pre-release) test57:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test57.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved Block download of remote URLs via command-lines
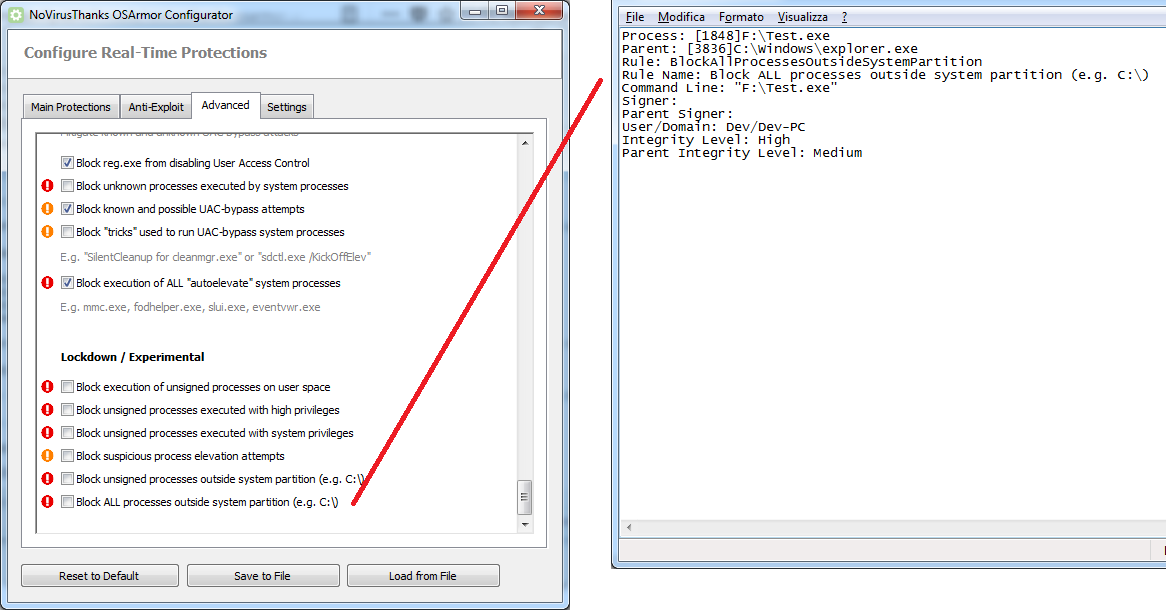
+ Block unsigned processes outside system partition (e.g. C:\)
+ Block ALL processes outside system partition (e.g. C:\)
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
With the new rules you can now block any (or only unsigned) processes executed outside system partition (e.g. C:\).
So a process executed, e.g., from F:\ or G:\ will be blocked, see this screenshot:
@128BPM
That FP shoud be fixed now, please confirm.
@Windows_Security
Yes.
Yes.
The option to block any process from wscript.exe was specifically asked by a company and to be separate from the anti-exploit tab.
You may find these new options useful:
+ Block unsigned processes outside system partition (e.g. C:\)
+ Block ALL processes outside system partition (e.g. C:\)

@Telos
With the block-rule:
[%PROCESSFILEPATH%: G:\*]
OSA would block any process located on G:\
It doesn't block a process from writing to that path (OSA doesn't monitor writing of files).
To exclude Microsoft-signed processes just add this to Exclusion rules:
[%PROCESSFILEPATH%: G:\*] [%FILESIGNER%: Microsoft Windows]
[%PROCESSFILEPATH%: G:\*] [%FILESIGNER%: Microsoft Corporation]
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test57.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved Block download of remote URLs via command-lines
+ Block unsigned processes outside system partition (e.g. C:\)
+ Block ALL processes outside system partition (e.g. C:\)
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
With the new rules you can now block any (or only unsigned) processes executed outside system partition (e.g. C:\).
So a process executed, e.g., from F:\ or G:\ will be blocked, see this screenshot:
@128BPM
That FP shoud be fixed now, please confirm.
@Windows_Security
1. Is starting other programs covered by the anti-exploit option of Word?
Yes.
2. Do you have made allow exceptions for print spool and touch keyboard?
Yes.
I am asking because for wscript.exe you have:
The option to block any process from wscript.exe was specifically asked by a company and to be separate from the anti-exploit tab.
So when you split your harddisk into C for programs and D for files it would look like: [%PROCESSFILEPATH%: D:\*]
You may find these new options useful:
+ Block unsigned processes outside system partition (e.g. C:\)
+ Block ALL processes outside system partition (e.g. C:\)
@Telos
With the block-rule:
[%PROCESSFILEPATH%: G:\*]
OSA would block any process located on G:\
It doesn't block a process from writing to that path (OSA doesn't monitor writing of files).
To exclude Microsoft-signed processes just add this to Exclusion rules:
[%PROCESSFILEPATH%: G:\*] [%FILESIGNER%: Microsoft Windows]
[%PROCESSFILEPATH%: G:\*] [%FILESIGNER%: Microsoft Corporation]
Ok, I'm going to verify now.
Question:
Could OSA protect against BadUSB if it alert/block of installing a new keyboard?
You may find these new options useful:
+ Block unsigned processes outside system partition (e.g. C:\)
+ Block ALL processes outside system partition (e.g. C:\)

Andreas,
Does the rule BLOCK ALL PROCESSES OUTSIDE also includes USB and RAM disk (other options)?
I would prefer it to apply the rule "block all" on harddisks only, so user has granular control on others (USB, CD Rom, Ram etc) with other options.
D
Deleted member 178
You can just make exclusions then, it is what i do.Andreas,
Does the rule BLOCK ALL PROCESSES OUTSIDE also includes USB and RAM disk (other options)?
I would prefer it to apply the rule "block all" on harddisks only, so user has granular control on others (USB, CD Rom, Ram etc) with other options.
@NoVirusThanks
When entering in option "change calendar settings", the previous FP (Block execution of suspicious command-line strings) was corrected. But now this appears:
Date/Time: 12/04/2018 08:18:38 p.m.
Process: [3208]C:\Windows\System32\control.exe
Process MD5 Hash: FD3F34830C39F4B554106ADA19924F4E
Parent: [3132]C:\Windows\System32\rundll32.exe
Rule: BlockSuspiciousProcessesFromRundll32
Rule Name: Block suspicious processes executed from Rundll32
Command Line: "C:\Windows\System32\control.exe" "C:\Windows\system32\intl.cpl",,/p:"date"
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
When entering in option "change calendar settings", the previous FP (Block execution of suspicious command-line strings) was corrected. But now this appears:
Date/Time: 12/04/2018 08:18:38 p.m.
Process: [3208]C:\Windows\System32\control.exe
Process MD5 Hash: FD3F34830C39F4B554106ADA19924F4E
Parent: [3132]C:\Windows\System32\rundll32.exe
Rule: BlockSuspiciousProcessesFromRundll32
Rule Name: Block suspicious processes executed from Rundll32
Command Line: "C:\Windows\System32\control.exe" "C:\Windows\system32\intl.cpl",,/p:"date"
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
Tried to reboot to Safe Mode (Shift-Restart) and got this...
Date/Time: 4/13/2018 1:35:37 PM
Process: [8608]C:\WINDOWS\System32\shutdown.exe
Process MD5 Hash: 0AA80010E37F8F8546CDD6D725D79A28
Parent: [3088]C:\WINDOWS\explorer.exe
Rule: BlockShutdownExeExecution
Rule Name: Block execution of shutdown.exe
Command Line: shutdown.exe /r /o /t 0
Signer:
Parent Signer: Microsoft Windows
User/Domain: Telos/Domain
Integrity Level: Medium
Parent Integrity Level: Medium
Still I was able to Restart without the Shift-key ... so I'm a bit perlexed.
That all said, I must have scanned the rules list 3 times before I could locate this one. I'm guessing it would be too much to ask for a rule search feature.
Date/Time: 4/13/2018 1:35:37 PM
Process: [8608]C:\WINDOWS\System32\shutdown.exe
Process MD5 Hash: 0AA80010E37F8F8546CDD6D725D79A28
Parent: [3088]C:\WINDOWS\explorer.exe
Rule: BlockShutdownExeExecution
Rule Name: Block execution of shutdown.exe
Command Line: shutdown.exe /r /o /t 0
Signer:
Parent Signer: Microsoft Windows
User/Domain: Telos/Domain
Integrity Level: Medium
Parent Integrity Level: Medium
Still I was able to Restart without the Shift-key ... so I'm a bit perlexed.
That all said, I must have scanned the rules list 3 times before I could locate this one. I'm guessing it would be too much to ask for a rule search feature.
Last edited:
Here is a new v1.4 (pre-release) test58:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test58.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Show System File: True\False on log file
+ Show Parent System File: True\False on log file
+ Improved detection of parent processes
+ Improved detection of UAC-bypass attempts
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test58.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Show System File: True\False on log file
+ Show Parent System File: True\False on log file
+ Improved detection of parent processes
+ Improved detection of UAC-bypass attempts
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
Here is a new v1.4 (pre-release) test59:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test59.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Added "Windows Live Mail" on Anti-Exploit tab
+ Added "PotPlayer" on Anti-Exploit tab
+ Added an Help\FAQs file (tray-icon -> Help\FAQs, Main menu -> Help -> Help\FAQs, GUI "?" top-right border icon)
+ Renamed Block system processes from cleaning Windows Eventlog
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test59.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Added "Windows Live Mail" on Anti-Exploit tab
+ Added "PotPlayer" on Anti-Exploit tab
+ Added an Help\FAQs file (tray-icon -> Help\FAQs, Main menu -> Help -> Help\FAQs, GUI "?" top-right border icon)
+ Renamed Block system processes from cleaning Windows Eventlog
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
@NoVirusThanks
Confirmed, the previous FPs were fixed
Note: Any comment regarding my question about BadUSB? Is it feasible or not?
Thanks.
Confirmed, the previous FPs were fixed
Note: Any comment regarding my question about BadUSB? Is it feasible or not?
Thanks.
@NoVirusThanks
Note: Any comment regarding my question about BadUSB? Is it feasible or not?
On the Heimdal Security blog there are some tips to mitigate this problem, could they be applied with OSA?
How to Fix the Critical BadUSB Security Flaw in Less than 10 Minutes
The 1.4 release is marked as Malware : Win32.Malware.Bucaspys.VSRSE4
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
False positive by GData and MAX:The 1.4 release is marked as Malware : Win32.Malware.Bucaspys.VSRSE4
VirusTotal
@NoVirusThanks
In System Properties/Hardware/Device Installation Settings. I have this log:
Date/Time: 17/04/2018 03:15:45 p.m.
Process: [1188]C:\Windows\System32\rundll32.exe
Process MD5 Hash: C36BB659F08F046B139C8D1B980BF1AC
Parent: [4756]C:\Windows\System32\SystemPropertiesComputerName.exe
Rule: BlockKnownUACBypassAttempts
Rule Name: Block known and possible UAC-bypass attempts
Command Line: "C:\Windows\System32\rundll32.exe" newdev.dll,DeviceInternetSettingUi 3
Signer:
Parent Signer:
User/Domain: PC/PC
System File: True
Parent System File: False
Integrity Level: High
Parent Integrity Level: High
In System Properties/Hardware/Device Installation Settings. I have this log:
Date/Time: 17/04/2018 03:15:45 p.m.
Process: [1188]C:\Windows\System32\rundll32.exe
Process MD5 Hash: C36BB659F08F046B139C8D1B980BF1AC
Parent: [4756]C:\Windows\System32\SystemPropertiesComputerName.exe
Rule: BlockKnownUACBypassAttempts
Rule Name: Block known and possible UAC-bypass attempts
Command Line: "C:\Windows\System32\rundll32.exe" newdev.dll,DeviceInternetSettingUi 3
Signer:
Parent Signer:
User/Domain: PC/PC
System File: True
Parent System File: False
Integrity Level: High
Parent Integrity Level: High
@NoVirusThanks
OS_Armor (and other NVT products as well probably) still does not recognize CATALOG signatures. Therefor most Windows executables look unsigned to OS_Armor, see for info : Catalog Files and Digital Signatures
Any progress .. . ...?
ADVICE TO USERS WITH NO IMAGE BACKUP/RECOVERY IN PLACE: DON'T USE SETTINGS OF OS_ARMOR WHICH RELATE TO PROGRAM SIGNING UNTIL THIS ISSUE IS SOLVED.
OS_Armor (and other NVT products as well probably) still does not recognize CATALOG signatures. Therefor most Windows executables look unsigned to OS_Armor, see for info : Catalog Files and Digital Signatures
Any progress .. . ...?
ADVICE TO USERS WITH NO IMAGE BACKUP/RECOVERY IN PLACE: DON'T USE SETTINGS OF OS_ARMOR WHICH RELATE TO PROGRAM SIGNING UNTIL THIS ISSUE IS SOLVED.
Last edited:
You may also like...
-
On Sale! Avast Premium Security 1 Device 1 Year 9.99€
- Started by Brownie2019
- Replies: 0
-
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Privacy News Windows 11 24H2/25H2 Flaw Keeps Task Manager Running After You Close It
- Started by Brownie2019
- Replies: 5