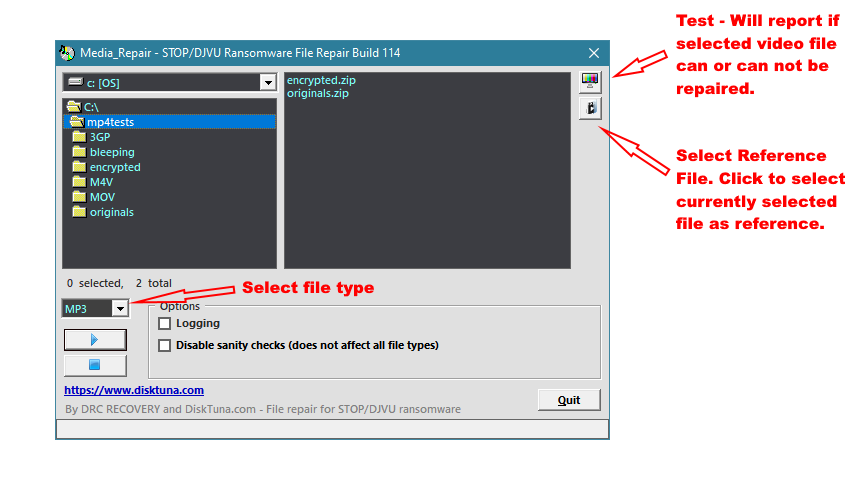
My PC got infected by STOP/DJVU Ransomware the day before yesterday. All of my files have been encrypted and have gotten .ogdo extension.
After ##### tons of hours of Googling, I cannot say that I got a definite solution for removing the malware and decrypting the files. After uploading the infected files in website, www.nomoreransom.org, the result was that the files can't be decrypted. The website, MalwareTips Community, showed the similar conclusion. The malware can be removed but the encrypted files can't be decrypted. Also, there is potential risk of double encryption from using fake Ransomware.
I had just installed Windows 10 as I was stuck in 'Fix Automatic Repair' loop and even resetting the PC was not possible. To activate the Windows and Office, I downloaded "KMSpico", turned off the Defender and that's where it got infected. The Virus-Protection cannot be turned on right now.Talk about the series of bad luck.
I have started the following processes from
Remove OGDO ransomware (Virus Removal Guide)
STEP 1: Use Malwarebytes Free to remove OGDO ransomware
STEP 2: Use HitmanPro to scan for Trojans and other malware
STEP 3: Double-check for malicious programs with Emsisoft Emergency Kit
STEP 4: Restore the files encrypted by the OGDO ransomware
I have scanned twice by all three softwares, restarting after each scan. As I was using Chrome, the software were finding malware in Chrome's files. So, I stopped using Chrome and in the third time, all three softwares did not file any malware. I am currently reinstalling Windows.
I am not sure if I couldn't post here due to me being new user or I just didn't know how. I hope I have not done any mistakes. I have not used any Decryption too yet. I want to make sure that the malware has 100% gone from PC and if possible I want to decrypt the files as there are files about 600 GB and IDK where to put it if I have to wipe the drive later.
After ##### tons of hours of Googling, I cannot say that I got a definite solution for removing the malware and decrypting the files. After uploading the infected files in website, www.nomoreransom.org, the result was that the files can't be decrypted. The website, MalwareTips Community, showed the similar conclusion. The malware can be removed but the encrypted files can't be decrypted. Also, there is potential risk of double encryption from using fake Ransomware.
I had just installed Windows 10 as I was stuck in 'Fix Automatic Repair' loop and even resetting the PC was not possible. To activate the Windows and Office, I downloaded "KMSpico", turned off the Defender and that's where it got infected. The Virus-Protection cannot be turned on right now.Talk about the series of bad luck.
I have started the following processes from
Remove OGDO ransomware (Virus Removal Guide)
STEP 1: Use Malwarebytes Free to remove OGDO ransomware
STEP 2: Use HitmanPro to scan for Trojans and other malware
STEP 3: Double-check for malicious programs with Emsisoft Emergency Kit
STEP 4: Restore the files encrypted by the OGDO ransomware
I have scanned twice by all three softwares, restarting after each scan. As I was using Chrome, the software were finding malware in Chrome's files. So, I stopped using Chrome and in the third time, all three softwares did not file any malware. I am currently reinstalling Windows.
I am not sure if I couldn't post here due to me being new user or I just didn't know how. I hope I have not done any mistakes. I have not used any Decryption too yet. I want to make sure that the malware has 100% gone from PC and if possible I want to decrypt the files as there are files about 600 GB and IDK where to put it if I have to wipe the drive later.