- Apr 18, 2016
- 3,676
- 28,872
- 4,599
after watching several videos CS has posted, I know CF is one of the best, if not the best security tool to lockdown the system. I'm no longer impressed anymore because CF does what it can do
however, I think should be used in a different way other than executing a malware inside the sandbox, as Sunshine-boy said, we don't notice any malicious activity inside the sandbox, unless the malwares are cryptominers, crash or spawn so many processes that can be noticed. Because of CS's settings, even safe apps with an UI can crash and show nothing
I think CF should be used as following:
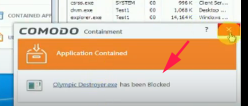
1/ exploit shield, when malwares try to download their payloads, CF will block them => something is clearly malicious and deserves user's intervention
2/ When an user executes a random file
- if CF allows the file to run because it is whitelisted by cloud or TVL => let the file runs
- if the file is sandboxed and crashes due to CS's configuration (untrusted or highly restricted), the file can either be safe or malicious. The user has to do several steps to determine the safety of that file (VM, VT, hybrid-analysis, sandboxie without no restriction,...) or pray and run the file outside the sandbox
for now, I'm using CF's sandbox as an exploit shield to block malware payloads
CF is extremely prone to FPs, especially for non-english, french or spanish applications (non-commonly speaking languages). In fact, I had to whitelist at least 10 times per day when I was installing or updating my applications
the 2/ is clearly not for average users and it's not security, it's troublemaker
however, I think should be used in a different way other than executing a malware inside the sandbox, as Sunshine-boy said, we don't notice any malicious activity inside the sandbox, unless the malwares are cryptominers, crash or spawn so many processes that can be noticed. Because of CS's settings, even safe apps with an UI can crash and show nothing
I think CF should be used as following:
1/ exploit shield, when malwares try to download their payloads, CF will block them => something is clearly malicious and deserves user's intervention
2/ When an user executes a random file
- if CF allows the file to run because it is whitelisted by cloud or TVL => let the file runs
- if the file is sandboxed and crashes due to CS's configuration (untrusted or highly restricted), the file can either be safe or malicious. The user has to do several steps to determine the safety of that file (VM, VT, hybrid-analysis, sandboxie without no restriction,...) or pray and run the file outside the sandbox
for now, I'm using CF's sandbox as an exploit shield to block malware payloads
CF is extremely prone to FPs, especially for non-english, french or spanish applications (non-commonly speaking languages). In fact, I had to whitelist at least 10 times per day when I was installing or updating my applications
the 2/ is clearly not for average users and it's not security, it's troublemaker
Last edited: