omni-defender.com
It's been 7 months now since we released our demo product and have received a lot of valuable feedback from experts to further enhance our cybersecurity solution and now it's officially released after countless hours of arduous development and testing!
OmniDefender offers a complete security solution against malware, aiming to compete with other top contenders. OmniDefender has WHQL Certification.
Features:
- Real Time Protection: Leverages the kernel to proactively monitor and block potentially malicious files before they have the chance to inflict any damage on the system.
- Custom Scan: Want to analyze a suspicious file and receive a detailed report on what the file is and what it can do? Custom Scan explains whether the file you're unsure of is potentially dangerous or not instead of just the generic malware/benign verdict.
- Smart Scan: Efficiently analyzes the entire system for potentially malicious files
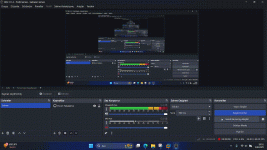
- Intrusion Detection: Analyzes all network activity in real time, which processes on your system are connected to the internet and their total download and uploads, allowing you to monitor and spot suspicious processes effectively.
- Performance: Monitors CPU Usage, Temperature, GPU Usage and Temperature, RAM Usage and Network usage in Real Time. Analyzes the PC for duplicates, large files, cleans up cache, temp folders and trash to gain disk space and
- Password Manager: Storing passwords in the browser is generally unsafe and prone to theft, that's why OmniDefender Password Manager allows you to import and encrypt your passwords with a Master Password so only you have access to them!
Here's a demo of OmniDefender against Malware:
Thanks for all your support during the beta, looking forward to your thoughts!
Hi, this sounds good/interesting my new Lenovo 1 has been totally disabled by a retaliatory system32 srttext block, after MS Copilot