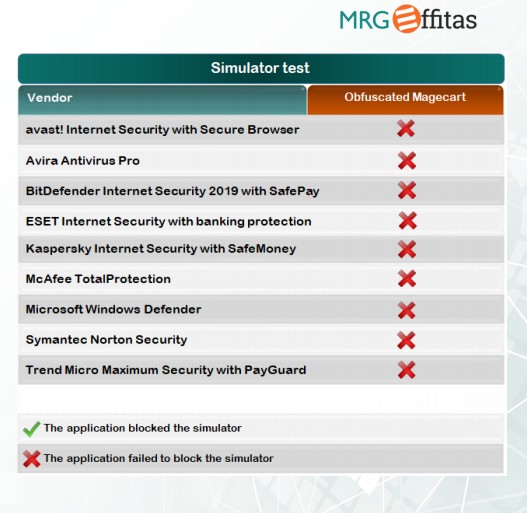
Online Banking / Browser SecurityCertification 2019 MRG-Effitas
- Thread starter Nestor
- Start date
You may also like...
-
-
Analysis of modules for protection of online banking and payments – 2026 edition
- Started by Adrian Ścibor
- Replies: 31
-
-
SOpera One R3 arrives with new AI, Google integrations, and more
- Started by Santiago Benavides García
- Replies: 0
-