Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
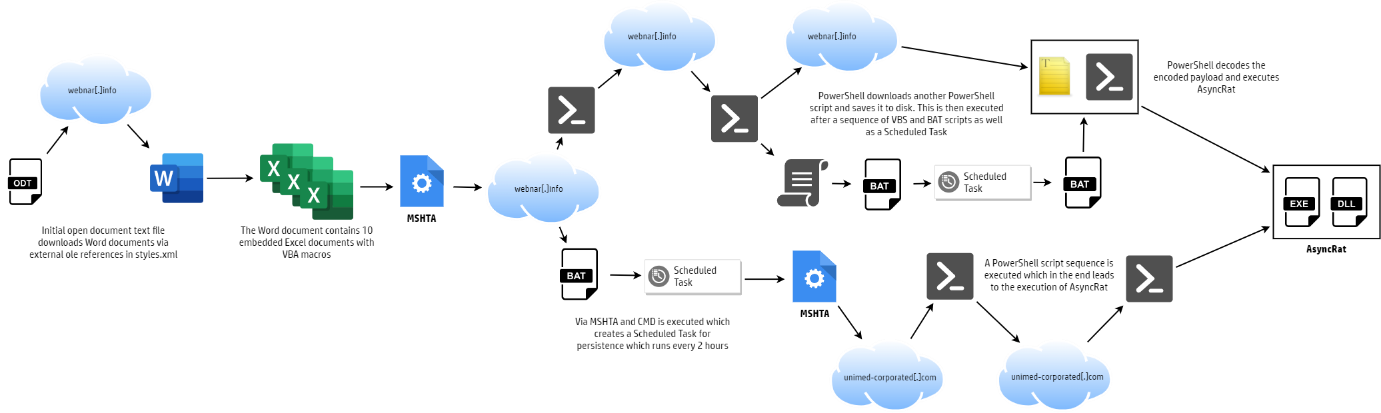
Security researchers at HP Wolf Security managed to isolate a malware campaign that used OpenDocument text files for distribution. This particular campaign was part of a larger one that was targeting the hotel industry in several South American countries that included Brazil, Argentina, Chile, Peru, Columbia and Costa Rica.
What makes this particular malware campaign interesting is the use of OpenDocument text files in the attack. All major office applications, including Microsoft Office, LibreOffice and Apache OpenOffice, support the format, which makes it an ideal format to carry out attacks.
Since it is less commonly used in malware attacks, it is a file format that computer users may be less suspicious about. Emails with Office document attachments, PDF documents or even executable files are commonly used and users may be more aware of the potential danger of these documents.
The threat actors referenced remotely hosted objects in the document but did not include any macros; this was done to evade detection, as antivirus engines may flag documents that make use of macros.
The researchers discovered the malware campaign in late June and noticed that the malicious OpenDocument documents were not picked up by any of VirusTotal's antivirus engines in the first week of July.
OpenDocument text files (.odt) malware campaign discovered - gHacks Tech News
Security researchers at HP Wolf Security managed to isolate a malware campaign that used OpenDocument text files for distribution.
www.ghacks.net