Code:
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\div_child.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting Begin path C:\Program Files (x86)\html\div\Application\1.0.0.0\div_elf.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\d3dcompiler_43.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\d3dcompiler_46.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\default_apps
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\delegate_execute.exe
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\Extensions
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\ffmpegsumo.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\icudtl.dat
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\libegl.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\libexif.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\libglesv2.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\libpeerconnection.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\Locales
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\metro_driver.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\mksnapshot.ia32.exe.assert.manifest
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\nacl64.exe
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\nacl_irt_x86_32.nexe
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\nacl_irt_x86_64.nexe
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\pdf.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\PepperFlash
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\pphtmlnaclplugindiv.dll
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\resources.pak
[0607/195454:WARNING:uninstall_class.cpp(568)] Deleting install path C:\Program Files (x86)\html\div\Application\1.0.0.0\widevinecdmadapter.dll
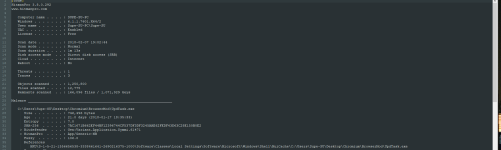
If it's any consolation, I do recognise some of the file-names in the above log. For example: d3dcompiler_43.dll, d3dcompiler_46.dll, icudtl.dat, libegl.dll, libglesv2.dll, resources.pak. It doesn't mean any of the file-names I recognise are actually the same components I am thinking of, people can lie on file-names.
d3dcompiler_43.dll and d3dcompiler_46 file-names ->
Direct3D API.
libegl.dll and libglesv2.dll is either Direct3D or Angle.
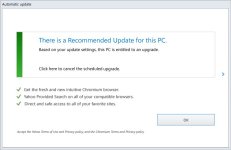
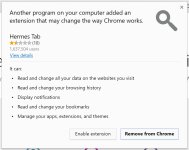
There's links between the log report you shared and other Adware from the past, see here:
BingAdwareHelpMe - Pastebin.com
resources.pak likely stores content packed inside of it, I only know of *.pak usage since I've had to do it before when dealing with web-based UI frameworks like the Chrome Embedded Framework. It is indeed possible that this rogue Chrome updater is relying on a web-based UI, but without further investigation you won't know.
I don't think any of us here can download samples directly from VirusTotal so providing us the VirusTotal link and not the actual sample won't get you anywhere asking for help on analysis.
However, as others have already said, the VirusTotal results speak for themselves. It's quite clear most vendors believe it to be adware - you also mentioned it is from a software bundler. There's likely not much point progressing further, I doubt all of those detection's are FPs and given the initial screenshots you attached, the likelihood of the detection's being FPs are like 0.0000001%/100000000000000000000000000000000000000.
In regards to SetWindowsHookExA/W imported by user32.dll, it doesn't necessarily mean the sample has a keylogger component embedded within it. The routine is used by Windows itself for functionality such as the shake effect when you drag a window's Win32 title-bar quickly and other windows automatically become minimised. The same applies to other Win32 API routines from User32.dll and other modules. The imports of a binary can provide insight sometimes but it won't be accurate alone most of the time. You'll need to check the actual binary statically/dynamically. Try checking the references to the routine in a disassembler like IDA and you'll be given more information regarding how it is used and if it is actually used for malicious intent for activity like a keylogger; it's very well possible it is, but you'll need to dig a tad deeper say on case it isn't.