The author of the Petya-Mischa ransomware combo has returned with a new version that uses the name GoldenEye Ransomware, continuing the malware's James Bond theme.
Brought to our attention today by a Bleeping Computer user named gizmo21, this new "GoldenEye" ransomware is almost identical to past Petya and Mischa variants.
GoldenEye Petya variant spreading via spam emails
The ransomware is currently distributed via spam campaigns that at the moment seem to be targeting German-speaking users.
The spam emails use the classic resume theme and come with two files attachments and have a subject starting with the word Bewerbung as shown below.
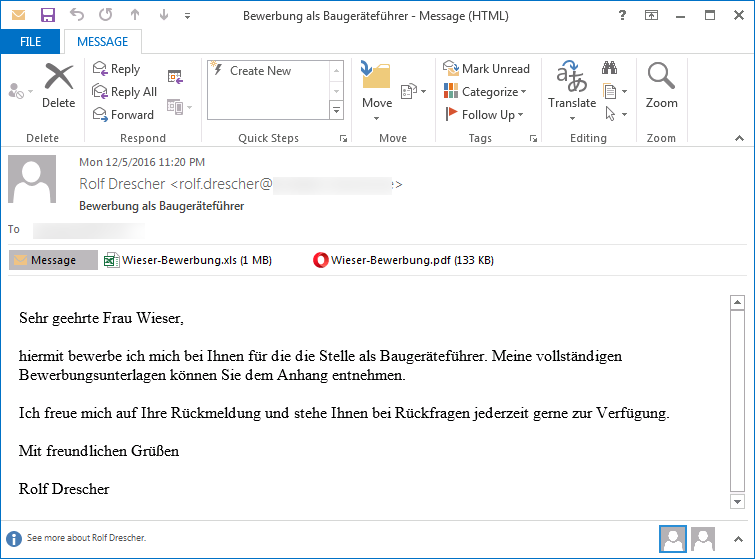
GoldenEye spam email
The first attachment is a fake resume that is being used to convince the human resources department that the email is legitimate. You can see one of the pages of this PDF below.

Fake PDF resume file included in GoldenEye spam campaign
The Excel spreadsheet, as shown below, is the main installer for the GoldenEye ransomware as it contains a malicious macro that installs the GoldenEye ransomware.
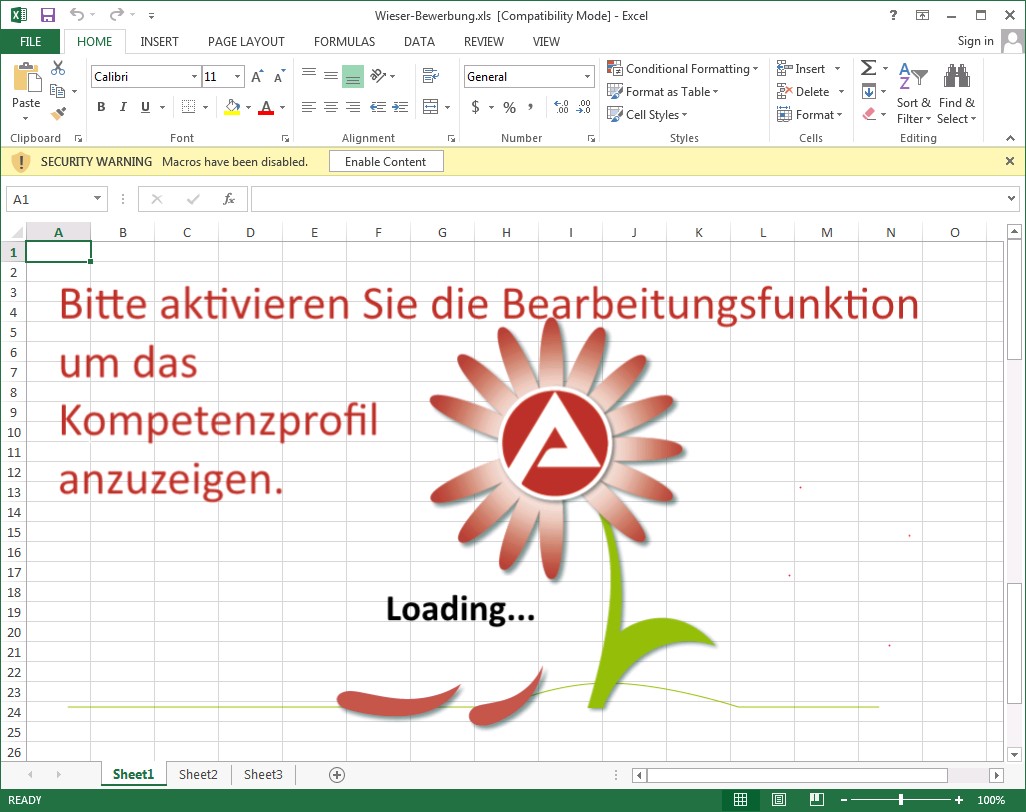
Excel file included in GoldenEye spam campaign
In the spam campaign observed in the past days, the Excel files have the following names:
Wiebold-Bewerbung.xls
Meinel-Bewerbung.xls
Seidel-Bewerbung.xls
Wüst-Bewerbung.xls
Born-Bewerbung.xls
Schlosser-Bewerbung.xls
When a user clicks on the Enable Content button, the macro will launch and save embedded base64 strings into an executable file in the temp folder. When the file has finished being created, the VBA script will automatically launch the program, which begins the encryption process on the computer.
You can see a small portion of the deobfuscated VBA macro that generates the installer below. I have posted the full VBA script here.
Read more: Petya Ransomware Returns with GoldenEye Version, Continuing James Bond Theme
Brought to our attention today by a Bleeping Computer user named gizmo21, this new "GoldenEye" ransomware is almost identical to past Petya and Mischa variants.
GoldenEye Petya variant spreading via spam emails
The ransomware is currently distributed via spam campaigns that at the moment seem to be targeting German-speaking users.
The spam emails use the classic resume theme and come with two files attachments and have a subject starting with the word Bewerbung as shown below.

GoldenEye spam email
The first attachment is a fake resume that is being used to convince the human resources department that the email is legitimate. You can see one of the pages of this PDF below.

Fake PDF resume file included in GoldenEye spam campaign
The Excel spreadsheet, as shown below, is the main installer for the GoldenEye ransomware as it contains a malicious macro that installs the GoldenEye ransomware.

Excel file included in GoldenEye spam campaign
In the spam campaign observed in the past days, the Excel files have the following names:
Wiebold-Bewerbung.xls
Meinel-Bewerbung.xls
Seidel-Bewerbung.xls
Wüst-Bewerbung.xls
Born-Bewerbung.xls
Schlosser-Bewerbung.xls
When a user clicks on the Enable Content button, the macro will launch and save embedded base64 strings into an executable file in the temp folder. When the file has finished being created, the VBA script will automatically launch the program, which begins the encryption process on the computer.
You can see a small portion of the deobfuscated VBA macro that generates the installer below. I have posted the full VBA script here.
Read more: Petya Ransomware Returns with GoldenEye Version, Continuing James Bond Theme