- Dec 27, 2016
- 1,480
A Chinese infosec researcher has discovered a new "almost impossible to detect" phishing attack that can be used to trick even the most careful users on the Internet.
He warned, Hackers can use a known vulnerability in the Chrome, Firefox and Opera web browsers to display their fake domain names as the websites of legitimate services, like Apple, Google, or Amazon to steal login or financial credentials and other sensitive information from users.
“It becomes impossible to identify the site as fraudulent without carefully inspecting the site's URL or SSL certificate” Xudong Zheng says.
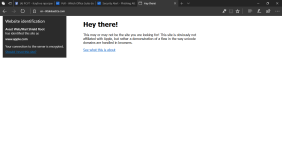
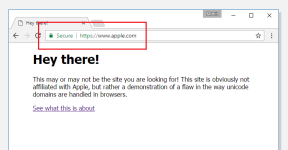
If your web browser is displaying "apple.com" in the address bar secured with SSL, but the content on the page is coming from another server (as shown in the above picture), then your browser is vulnerable to the 'Homograph attack'.
While Mozilla is currently still discussing a fix, Google has already patched the vulnerability in its experimental Chrome Canary 59 and will come up with a permanent fix with the release of Chrome Stable 58, set to be launched later this month.
Meanwhile, millions of Internet users who are at risk of this sophisticated hard-to-detect phishing attack are recommended to disable Punycode support in their web browsers in order to temporarily mitigate this attack.
While Chrome users have to wait for the said release, Firefox users can follow below-mentioned steps to manually apply temporarily mitigation:
He warned, Hackers can use a known vulnerability in the Chrome, Firefox and Opera web browsers to display their fake domain names as the websites of legitimate services, like Apple, Google, or Amazon to steal login or financial credentials and other sensitive information from users.

“It becomes impossible to identify the site as fraudulent without carefully inspecting the site's URL or SSL certificate” Xudong Zheng says.
If your web browser is displaying "apple.com" in the address bar secured with SSL, but the content on the page is coming from another server (as shown in the above picture), then your browser is vulnerable to the 'Homograph attack'.
The quoted loophole based on Punycode in browsers allowed the researcher to register a domain name xn--80ak6aa92e.com which appears as “apple.com” by all vulnerable web browsers, including Chrome, Firefox, and Opera, though Internet Explorer, Microsoft Edge, Apple Safari, Brave, and Vivaldi are not vulnerable.Homograph attack has been known since 2001, but browser vendors have struggled to fix the problem. It’s a kind of spoofing attack where a website address looks legitimate but is not because a character or characters have been replaced deceptively with Unicode characters.
Punycode Phishing Attacks
By default, many web browsers use ‘Punycode’ encoding to represent Unicode characters in the URL to defend against such phishing attacks. Punycode is a special encoding used by the web browser to convert Unicode characters to the limited character set of ASCII (A-Z, 0-9), supported by International Domain Names (IDNs) system.
For example, the Chinese domain "短.co" is represented in Punycode as "xn--s7y.co".
According to Zheng, the vulnerability relies on the fact that web browsers render only Punycode URLs in one language as Unicode (like only Chinese or only Japanese), but they fail if a domain name contains characters from multiple languages.
While Mozilla is currently still discussing a fix, Google has already patched the vulnerability in its experimental Chrome Canary 59 and will come up with a permanent fix with the release of Chrome Stable 58, set to be launched later this month.
Meanwhile, millions of Internet users who are at risk of this sophisticated hard-to-detect phishing attack are recommended to disable Punycode support in their web browsers in order to temporarily mitigate this attack.
While Chrome users have to wait for the said release, Firefox users can follow below-mentioned steps to manually apply temporarily mitigation:
- Type about:config in address bar and press enter.
- Type Punycode in the search bar.
- Browser settings will show parameter titled: network.IDN_show_punycode, double-click or right-click and select Toggle to change the value from false to true.
Last edited: