Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Just trying to overcome the time difference between New Zealand and the Netherlands (it is 03 at night in NL and can't sleep  )
)
Chrome
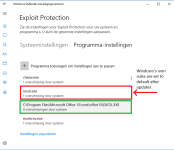
Added Chrome.exe to W10 Windows Defender exploit protection and enabled:
Edge
I split this into the broker (Edge) and content processor (EdgeCP).
Added MicrosoftEdge.exe to W10 Windows Defender exploit protection and enabled:
 )
)
Chrome
Added Chrome.exe to W10 Windows Defender exploit protection and enabled:
- Arbitrary code guard (ACG)
- Blow low integrity images - ENABLED
- Block remote images - ENABLED
- Block untrusted fonts
- Code integrity guard
- Control flow guard (CFG) - ENABLED (on 64 bits Chrome you can also enable strict option)
- Data Execution Prevention (DEP) - ENABLED
- Disable extension points - ENABLED
- Disable Win32 system calls (Chrome enables this flag itself for its rendering processes)
- Do not allow child processes
- Export address filtering (EAF)
- Force randomization for images (Mandatory ASLR) - ENABLED (enable no stripped images)
- Randomize memory allocations (Bottom-Up ASLR)
- Import address filtering (IAF)
- Simulate execution (SimExec)
- Validate API invocation (CallerCheck)
- Validate exception chains (SEHOP) - ENABLED
- Validate handle usage - ENABLED
- Validate heap integrity - ENABLED
- Validate image dependency integration - ENABLED
- Validate stack integrity (StackPivot)
Edge
I split this into the broker (Edge) and content processor (EdgeCP).
Added MicrosoftEdge.exe to W10 Windows Defender exploit protection and enabled:
- Arbitrary code guard (ACG) - ENABLED
- Blow low integrity images - ENABLED
- Block remote images - ENABLED
- Block untrusted fonts
- Code integrity guard - ENABLED (also Microsoft Store)
- Control flow guard (CFG) - ENABLED (enforce strict)
- Data Execution Prevention (DEP) - ENABLED
- Disable extension points - ENABLED
- Disable Win32 system calls
- Do not allow child processes
- Export address filtering (EAF)
- Force randomization for images (Mandatory ASLR) - ENABLED (enable no stripped images)
- Randomize memory allocations (Bottom-Up ASLR) - ENABLED (enable no high entrophy)
- Import address filtering (IAF)
- Simulate execution (SimExec)
- Validate API invocation (CallerCheck)
- Validate exception chains (SEHOP) - ENABLED
- Validate handle usage - ENABLED
- Validate heap integrity - ENABLED
- Validate image dependency integration - ENABLED
- Validate stack integrity (StackPivot)
- Arbitrary code guard (ACG) - ENABLED (important: allow Thread Opt-Out)
- Blow low integrity images - ENABLED
- Block remote images - ENABLED
- Block untrusted fonts
- Code integrity guard - ENABLED (also Microsoft Store)
- Control flow guard (CFG) - ENABLED (important: don't enforce strict)
- Data Execution Prevention (DEP) - ENABLED
- Disable extension points - ENABLED
- Disable Win32 system calls
- Do not allow child processes - ENABLED
- Export address filtering (EAF)
- Force randomization for images (Mandatory ASLR) - ENABLED (enable no stripped images)
- Randomize memory allocations (Bottom-Up ASLR) - ENABLED (enable no high entrophy)
- Import address filtering (IAF)
- Simulate execution (SimExec)
- Validate API invocation (CallerCheck)
- Validate exception chains (SEHOP) - ENABLED
- Validate handle usage - ENABLED
- Validate heap integrity - ENABLED
- Validate image dependency integration - ENABLED
- Validate stack integrity (StackPivot)
Last edited: