A new ransomware was released yesterday that was based on the open-source EDA2 ransomware. This ransomware encrypts your data using AES encryption, appends the Locked extension, and then demand .5 bitcoins to get the decryption key. There have been quite a few EDA2 ransomware variants, but what makes this story different is how this ransomware developer is such a pompous ass and that we were able to get the victim's keys back.
The ransom note for this infection was first tweeted by Malekal Morte and then a victim posted about the ransomware at BleepingComputer a few hours later. Normally, ransomware developers are very businesslike when giving instructions to their victims.
Instead, this developer acts like a pompous jackass by bragging about how the police will never find them, what the victim did wrong, and basically going on a power trip. Some particularly asinine statements include:
* You'll never be able to find me. Police will never be able to find me. Go ahead and try them if you like, but don't expect your data back. They will be concerned about helping the community, not with helping you meet your deadline. If they say they need to keep your desktop for a few days, well lol, you probably won't be seeing your machine again soon, let alone your data. I've been doing this for five years now and haven't been caught yet.
* Best Buy will have no ability to undo the encryption. Hell, even the NSA probably couldn't undo it. Well maybe they could, but I suspect you won't be a high priority for their computation clusters for at least a couple of years.
* In 72 hours, you will never be able to get these files open. I don't much like people struggling against the powerful and there is no way for you to argue for an extension. Just make it happen.
So just be thankful that it wasn't worse. I could have asked for more money. I could have been working for ISIS and saving that money to behead children. I could have been a mean SOB and just destroyed your data outright. Am I those things? No. I just need the money to live off of (true story) and don't care at all about the hacker "community". So there isn't anyone you will be protecting by sacrificing yourself. I'll just encrypt more people's data to make up for the loss.
You can read the full ransom note by clicking on the image below.
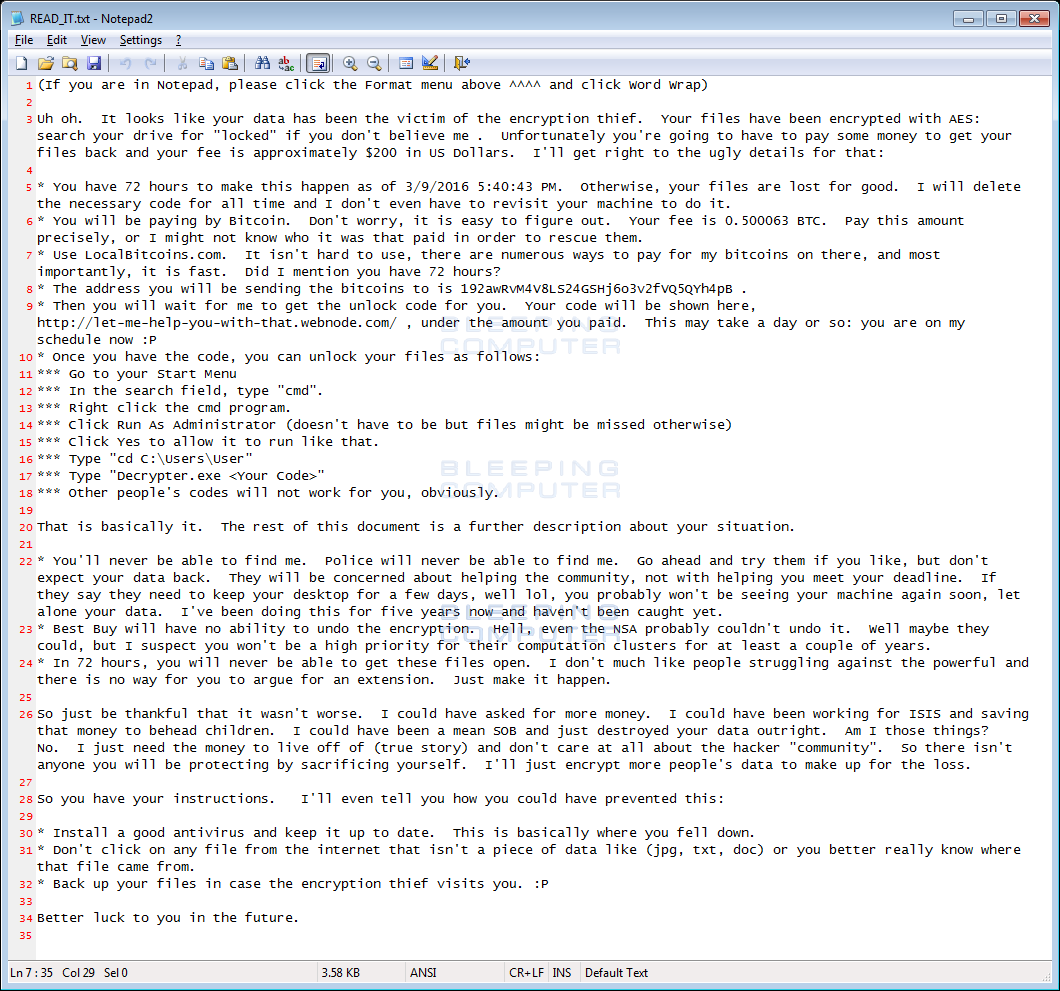
Read_it.txt Ransom Note
Unfortunately, this ransomware was fairly successful as it was able to encrypt approximately 700 victims over the course of one day. It did this by pretending to be a crack for a new FarCry game. Furthermore, at least 3 people paid for their decryption keys.
At this time, the ransomware is no longer working as their Command & Control server appears to have been shut down.
Backdoor to the rescue...
The good news is that the EDA2 ransomware has a backdoor in it that allows us to retrieve all of the decryption keys. Using this backdoor, the EDA2 developer Utku Sen and one of our helpers demonslay335 was able to retrieve all the keys and convert them into the proper decryption keys. Demonslay335 then posted a link to the list of retrieved decryption keys along with a decryptor.
For those who were infected with this variant, you can click here to view a list of decryption keys. When viewing the list, search for your computer name and then copy down the associated key. You can then download the Hidden Tear Decryptor and use that key to decrypt your encrypted files.
A big thanks to everyone who assisted in tracking down the samples and getting the decryption keys:@malekal_morte, @utku1337, @demonslay335, @malwrhunterteam, @Techhelplistcom,@DanielRufde, and @DanielGallagher
The ransom note for this infection was first tweeted by Malekal Morte and then a victim posted about the ransomware at BleepingComputer a few hours later. Normally, ransomware developers are very businesslike when giving instructions to their victims.
Instead, this developer acts like a pompous jackass by bragging about how the police will never find them, what the victim did wrong, and basically going on a power trip. Some particularly asinine statements include:
* You'll never be able to find me. Police will never be able to find me. Go ahead and try them if you like, but don't expect your data back. They will be concerned about helping the community, not with helping you meet your deadline. If they say they need to keep your desktop for a few days, well lol, you probably won't be seeing your machine again soon, let alone your data. I've been doing this for five years now and haven't been caught yet.
* Best Buy will have no ability to undo the encryption. Hell, even the NSA probably couldn't undo it. Well maybe they could, but I suspect you won't be a high priority for their computation clusters for at least a couple of years.
* In 72 hours, you will never be able to get these files open. I don't much like people struggling against the powerful and there is no way for you to argue for an extension. Just make it happen.
So just be thankful that it wasn't worse. I could have asked for more money. I could have been working for ISIS and saving that money to behead children. I could have been a mean SOB and just destroyed your data outright. Am I those things? No. I just need the money to live off of (true story) and don't care at all about the hacker "community". So there isn't anyone you will be protecting by sacrificing yourself. I'll just encrypt more people's data to make up for the loss.
You can read the full ransom note by clicking on the image below.

Read_it.txt Ransom Note
Unfortunately, this ransomware was fairly successful as it was able to encrypt approximately 700 victims over the course of one day. It did this by pretending to be a crack for a new FarCry game. Furthermore, at least 3 people paid for their decryption keys.

At this time, the ransomware is no longer working as their Command & Control server appears to have been shut down.
Backdoor to the rescue...
The good news is that the EDA2 ransomware has a backdoor in it that allows us to retrieve all of the decryption keys. Using this backdoor, the EDA2 developer Utku Sen and one of our helpers demonslay335 was able to retrieve all the keys and convert them into the proper decryption keys. Demonslay335 then posted a link to the list of retrieved decryption keys along with a decryptor.
For those who were infected with this variant, you can click here to view a list of decryption keys. When viewing the list, search for your computer name and then copy down the associated key. You can then download the Hidden Tear Decryptor and use that key to decrypt your encrypted files.
A big thanks to everyone who assisted in tracking down the samples and getting the decryption keys:@malekal_morte, @utku1337, @demonslay335, @malwrhunterteam, @Techhelplistcom,@DanielRufde, and @DanielGallagher