Malwarebytes. It's somehow the most popular AV yet the least tested on any AV test platform. Why? 
AVLab.pl Product Enquiry - Which products should we test in your opinion?
- Thread starter Adrian Ścibor
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Disclaimer
This test shows how an antivirus behaves with certain threats, in a specific environment and under certain conditions.
We encourage you to compare these results with others and take informed decisions on what security products to use.
Before buying an antivirus you should consider factors such as price, ease of use, compatibility, and support. Installing a free trial version allows an antivirus to be tested in everyday use before purchase.
It is 100% sales tool.Fair enough. It can then just be a false sense of security, a bit of a sales tool, of the "protection" it provides.
They rely on careless users that switch off their security software, download dodgy “stuff” or as our favourite @bazang likes to say “users want to use stuff” or not running any security software whatsoever. Some of them create exclusions for the aforementioned dodgy stuff.The fact that they have maintained a persistent threat for over twenty years suggests fundamental flaws in existing security measures.
Such users rarely do banking, in fact in their countries online shopping often involves collecting payment from customer directly upon delivery.
Many of them don’t even keep money in their bank, upon being paid, they go and withdraw everything.
Such users cannot be protected by anything. Banking protection will not help them.
F
ForgottenSeer 114834
The shift from standard detection to layered defense reflects the evolving threat landscape. Do you seriously believe layered modules are less capable of mitigating risks?It is 100% sales tool.
They rely on careless users that switch off their security software, download dodgy “stuff” or as our favourite @bazang likes to say “users want to use stuff” or not running any security software whatsoever. Some of them create exclusions for the aforementioned dodgy stuff.
Such users rarely do banking, in fact in their countries online shopping often involves collecting payment from customer directly upon delivery.
Many of them don’t even keep money in their bank, upon being paid, they go and withdraw everything.
Such users cannot be protected by anything. Banking protection will not help them.
Layered modules is one, useless gimmicks is another.The shift from standard detection to layered defense reflects the evolving threat landscape. Do you seriously believe layered modules are less capable of mitigating risks?
F
ForgottenSeer 114834
Based on personal opinion, means that the following statement is subjective and reflects the speaker's individual viewpoint rather than objective facts or evidence. It's a way to acknowledge that the subsequent statement is not necessarily a universally shared belief.Layered modules is one, useless gimmicks is another.
Example:
"Based on personal opinion, I believe that chocolate ice cream is the best flavor."
Arguments have already been presented in relation to these opinions. If anyone can chime in and say “I was infected with this Trojan on this day and banking protection helped me avoid financial loss”, I’ll accept I was wrong.Based on personal opinion, means that the following statement is subjective and reflects the speaker's individual viewpoint rather than objective facts or evidence. It's a way to acknowledge that the subsequent statement is not necessarily a universally shared belief.
Example:
"Based on personal opinion, I believe that chocolate ice cream is the best flavor."
Defender free on default settings + Smart App Control (Windows 11) - tested in the category "Home Users".
Microsoft promotes the above as a recommended setup for average users at home and hybrid work. It is applied automatically on many computers after the Evaluation period.
This setup is similar to Norton with Download Insight, except the user cannot bypass the alerts.
Microsoft promotes the above as a recommended setup for average users at home and hybrid work. It is applied automatically on many computers after the Evaluation period.
This setup is similar to Norton with Download Insight, except the user cannot bypass the alerts.
Last edited:
But, how much of this is really a gimmick, and how much of it is layered protection? (I'm asking in sincerity) Are all of the other components of the standard browsing protection "disabled" using banking protection, or still active including those features creating a greater layer of protection as @Lynx is suggesting?Layered modules is one, useless gimmicks is another.
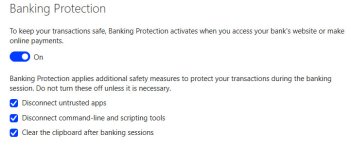
Neither untrusted apps, nor some command line tools and utilities should ever be running on users machines at any given time. It should not be waited for user to “bank/shop” and for banking protection to do all that.
The clearing of the clipboard is ok, but again, clipboard grabbers should not be running. DeepGuard should be monitoring the clipboard access and it is.
The clearing of the clipboard is ok, but again, clipboard grabbers should not be running. DeepGuard should be monitoring the clipboard access and it is.
Malwarebytes. It's somehow the most popular AV yet the least tested on any AV test platform. Why?
We do it regularly
You can track this website also: Malwarebytes » AVLab Cybersecurity Foundation
Last edited:
I really like how you distinguish between pre-launch and post-launch remediation. I know I have a personal preference towards pre-launch remediation and was never comfortable with post-launch. This is giving consumers a great overview on how each AV behaves.We do it regularlySee on Recent Results » AVLab Cybersecurity Foundation and previous months. Why? Maybe we test better than other labs, so that's why they participate in our test only?
You can track this website also: Malwarebytes » AVLab Cybersecurity Foundation
Indeed.I have a personal preference towards pre-launch remediation and was never comfortable with post-launch.
I really understand your opinion.
In theory protection at pre_execution level is better than post_execution, but in practise result is same on paper. You can choose products which are characterised by better protection at PRE level. Hovewer sometimes danger situation may occurs when malware is executed by user, so software must protect system in 100%.
That's why we want to show to community the differences between pre and post level in Advanced In-The-Wild Malware Test (a new edition for July 2024 will be published this week and we will include NordVPN Threat Protection software to check efectiveness of protection at PRE execution level and Tachyon Internet Security as well in September 2024 edition).
@Adrian Ścibor
There are some errors in the test files:
The content of the test file (Comparison Table, .csv file) for September 2022 is the same as for July 2022.
The test file for May 2024 is the same as for March 2024.
Edit.
By the way, the .csv test files with malware hashes can be very helpful.

There are some errors in the test files:
The content of the test file (Comparison Table, .csv file) for September 2022 is the same as for July 2022.
The test file for May 2024 is the same as for March 2024.
Edit.
By the way, the .csv test files with malware hashes can be very helpful.
Last edited:
Checksums are available in each CSV for every single test edition@Adrian Ścibor
There are some errors in the test files:
The content of the test file (Comparison Table, .csv file) for September 2022 is the same as for July 2022.
The test file for May 2024 is the same as for March 2024.
Edit.
By the way, the .csv test files with malware hashes can be very helpful.
Checksums are available in each CSV for every single test edition
The scorings displayed on the AVLab website differ in these two cases from the information included in the .csv files. So, someone used the correct testing information for scorings and statistics but attached the wrong .csv files.
For the May 2024, test the .csv file is named "report-summary-march-2024.csv" and binary equal to the .csv file taken from the March 2024 test.
For September 2022 the file name is OK ("september-2022.csv"), but it is simply renamed file "july-2022.csv" taken from the July test.
Edit.
I used the hashes included in the .csv files to get information from VirusTotal about the infection rate of digitally signed files (valid, fake, malformed) compared to unsigned files.
Last edited:
I am gonna to fix this soon, sorry for that. I have to do some reasearch in our database manually for the data.The scorings displayed on the AVLab website differ in these two cases from the information included in the .csv files. So, someone used the correct testing information for scorings and statistics but attached the wrong .csv files.
For the May 2024, test the .csv file is named "report-summary-march-2024.csv" and binary equal to the .csv file taken from the March 2024 test.
For September 2022 the file name is OK ("september-2022.csv"), but it is simply renamed file "july-2022.csv" taken from the July test.
Edit.
I used the hashes included in the .csv files to get information from VirusTotal about the infection rate of digitally signed files (valid, fake, malformed) compared to unsigned files.
*By the way - we are on the straight way to publish a first "Cyber Transparency Audit" soon. The project is new, so keep fingers crossed please
@Adrian Ścibor do you reach out to Emsisoft or visa versa, as you seem to be the only (or one of few) testing Emsi.
Yeap. We stay in contact with their engineers, threat analytists and CEO. Would you like to know something more or ask for details?@Adrian Ścibor do you reach out to Emsisoft or visa versa, as you seem to be the only (or one of few) testing Emsi.
*edited - vocabulary mistake :/
Last edited:
Just curious, I just started using Emsisoft (again) after seeing your test(s) & @Shadowra's. Thanks for posting your links and info here!Yeap. We stay in contact with their engineers, threat analytists and CEO. Would you like to know something more or ask for details?
*edited - vocabulary mistake :/
Deep Instinct, Checkpoint Harmony and Huorong if that's somehow possible
You may also like...
-
AVLab.pl Advanced In-The-Wild Malware Test results for March 2025
- Started by Adrian Ścibor
- Replies: 44
-
AVLab.pl AVLab joins Microsoft Virus Initiative
- Started by Gandalf_The_Grey
- Replies: 2
-
AV-Comparatives Anti-Tampering Certification Test 2025
- Started by Gandalf_The_Grey
- Replies: 1
-
AVLab.pl Advanced In-The-Wild Malware Test – January 2025
- Started by Gandalf_The_Grey
- Replies: 3
-
AVLab.pl Product Of The Year 2025 – Summary of Advanced In-The-Wild Malware Test
- Started by Adrian Ścibor
- Replies: 16



