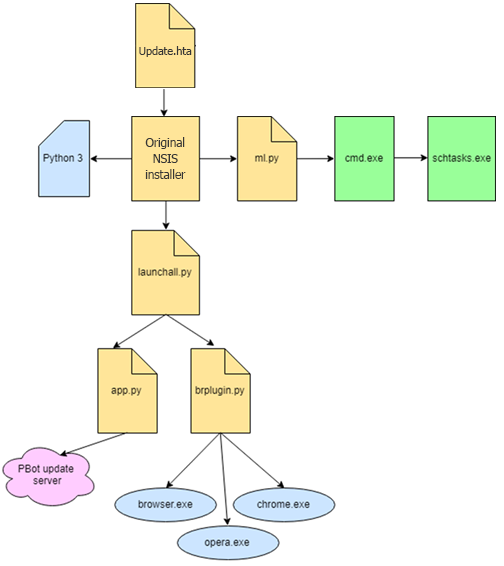
Two other versions of PBot we detected were restricted to the goal of placing unwanted advertising on web pages visited by the victim. In both versions, the adware initially attempts to inject a malicious DLL into the browser. The first version uses it to run JS scripts to display ads on web pages, the second — to install ad extensions in the browser. The latter is the more interesting of the two: developers are constantly releasing new versions of this modification, each of which complicates the script obfuscation. Another distinctive feature of this Pbot variation is the presence of a module that updates scripts and downloads fresh browser extensions. Throughout April, we registered more than 50,000 attempts to install PBot on computers of users of Kaspersky Lab products. The following month this number increased, indicating that this adware is on the rise. PBot’s target audience is mainly in Russia, Ukraine, and Kazakhstan.
PBot is generally distributed through partner sites whose pages implement scripts to redirect users to sponsored links.
Here is the standard PBot propagation scheme:
- The user visits the partner site.
- When any point on the page is clicked, a new browser window pops up that opens an intermediate link.
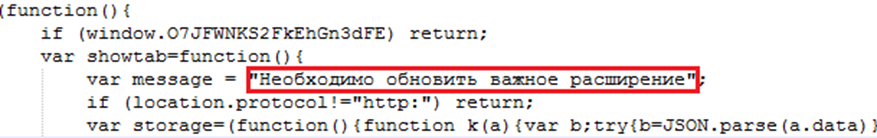
- The intermediate link redirects the user to the PBot download page, which is tasked with downloading and running the adware on the victim computer by hook or by crook. The following is a section of code from one such page:
4. An HTA file is downloaded. On startup this file downloads the PBot installer.