silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,729
- 123,838
- 8,399
Main description
QakBot, also known as QBot, QuackBot and Pinkslipbot, is a banking Trojan that has existed for over a decade. It was found in the wild in 2007 and since then it has been continually maintained and developed.In recent years, QakBot has become one of the leading banking Trojans around the globe. Its main purpose is to steal banking credentials (e.g., logins, passwords, etc.), though it has also acquired functionality allowing it to spy on financial operations, spread itself, and install ransomware in order to maximize revenue from compromised organizations.
To this day, QakBot continues to grow in terms of functionality, with even more capabilities and new techniques such as logging keystrokes, a backdoor functionality, and techniques to evade detection. It’s worth mentioning that the latter includes virtual environment detection, regular self-updates and cryptor/packer changes. In addition, QakBot tries to protect itself from being analyzed and debugged by experts and automated tools.
Another interesting piece of functionality is the ability to steal emails. These are later used by the attackers to send targeted emails to the victims, with the obtained information being used to lure victims into opening those emails.
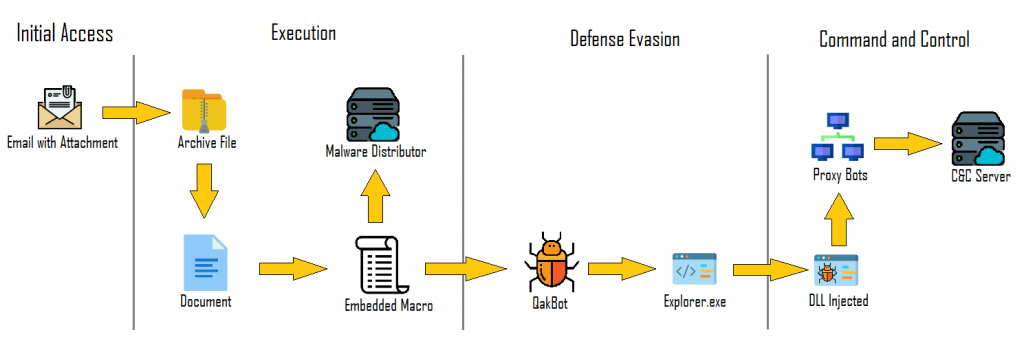
QakBot infection chain
QakBot is known to infect its victims mainly via spam campaigns. In some cases, the emails were delivered with Microsoft Office documents (Word, Excel) or password-protected archives with the documents attached. The documents contained macros and victims were prompted to open the attachments with claims that they contained important information (e.g., an invoice). In some cases, the emails contained links to web pages distributing malicious documents.However, there is another infection vector that involves a malicious QakBot payload being transferred to the victim’s machine via other malware on the compromised machine.
The initial infection vectors may vary depending on what the threat actors believe has the best chance of success for the targeted organization(s). It’s known that various threat actors perform reconnaissance (OSINT) of target organizations beforehand to decide which infection vector is most suitable.
The infection chain of recent QakBot releases (2020-2021 variants) is as follows:
- The user receives a phishing email with a ZIP attachment containing an Office document with embedded macros, the document itself or a link to download malicious document.
- The user opens the malicious attachment/link and is tricked into clicking “Enable content”.
- A malicious macro is executed. Some variants perform a ‘GET’ request to a URL requesting a ‘PNG’ However, the file is in fact a binary.
- The loaded payload (stager) includes another binary containing encrypted resource modules. One of the encrypted resources has the DLL binary (loader) which is decrypted later during runtime.
- The ‘Stager’ loads the ‘Loader’ into the memory, which decrypts and runs the payload during runtime. The configuration settings are retrieved from another resource.
- The payload communicates with the C2 server.
- Additional threats such as ProLock ransomware can now be pushed to the infected machine.
Typical QakBot functions
Typical QakBot malicious activity observed in the wild includes:- Collecting information about the compromised host;
- Creating scheduled tasks (privilege escalation and persistency);
- Credentials harvesting:
- Password brute forcing;
- Registry manipulation (persistence);
- Creating a copy of itself;
- Process injection to conceal the malicious process.
Full report by Kaspersky:

Technical analysis of the QakBot banking Trojan
This report contains technical analysis of the Trojan-Banker named QakBot (aka QBot, QuackBot or Pinkslipbot) and its information stealing, web injection and other modules.