This folder with the DLL inside was created well before uninstalling Kaspersky Free, the folder was created before 2024 but this DLL was only detected by Defender, so before Defender detected this DLL with malware was it active in the system performing hidden operations at the time you used Kaspersky Free and kaspersky free not detected dll in scan?
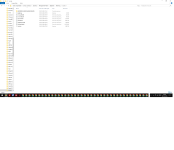
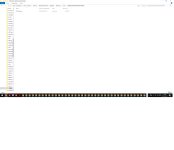
My guess is in the folder with the randomly generated name (at the very top), there was a suspicious executable.
The suspicious executable was deleted (because the folder is blank) but the module QTWebkit wasn’t.
If you look at the “Date Last Modified”, everything else was created at 7:59, this module was created later at 8:10, most likely fetched from a C&C website.
This module is the original module with the digital signatures but it has been maliciously modified by attackers. The malicious functions are called by the executable that was in the randomly generated name folder. Attackers are targeting solutions that don’t properly validate digital signatures and for them, the module will look like it is signed (though honestly not sure which solution this will be).
There are also 2 archives, in these archives most probably is the exfiltrated data.
The fact that the archives are old (no new archives created) and they are also not deleted means that the attack was suspended in its roots (by whatever AV you used December last year).
When infostealers are active, they exfiltrate data constantly, it’s not one-time affair.
The malware remained on disk dormant (latent/inactive). It wasn’t actively operating.