silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,746
- 123,926
- 8,399
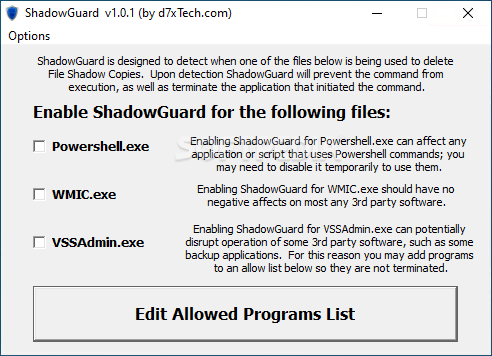
Read more: New ransomware vaccine kills programs wiping Windows shadow volumesA new ransomware vaccine program has been created that terminates processes that try to delete volume shadow copies using Microsoft's vssadmin.exe program,
This weekend, security researcher Florian Roth released the 'Raccine' ransomware vaccine that will monitor for the deletion of shadow volume copies using the vssadmin.exe command. "We see ransomware delete all shadow copies using vssadmin pretty often. What if we could just intercept that request and kill the invoking process? Let's try to create a simple vaccine," Raccine's GitHub page explains.
Raccine works by registering the raccine.exe executable as a debugger for vssadmin.exe using the Image File Execution Options Windows registry key.
Once raccine.exe is registered as a debugger, every time vssadmin.exe is executed, it will also launch Raccine, which will check to see if vssadmin is trying to delete shadow copies. If it detects a process is using 'vssadmin delete,' it will automatically terminate the process, which is usually done before ransomware begins encrypting files on a computer.