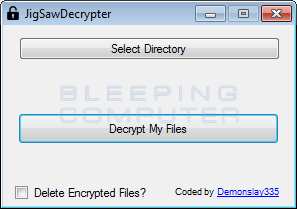
Point of this thread is posting every ransomware decryption tool you can find online. Of course from a trusted source.

Requirements
Code:
Product Name :
What ransomware the tool is made for :
Version Number (if possible) :
Screenshot of the program (if available) :
Download link (from developer site if possible) :Please do not post anti-ransomware tools and software that protects users from these malwares. Post tools that are made to decrypt already encrypted files on the victim's computer. Also, check if the tool is already posted, don't duplicate.
Let us help people in trouble! Stop the ransom!