Today, a new ransomware variant has been discovered, which masquerades as Malwarebytes, a well known security company providing anti-malware security software.
In an analysis by MalwareHunter, it was found out that the program is a cryptomalware called DetoxCrypto, which was initially detected back in August.
The malware's file properties were posted on VirusTotal, and it lists the following information:
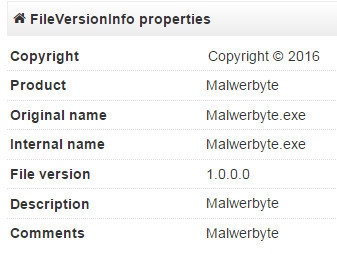
Clearly enough, the malware developer wants people to think that the program is a legitimate Malwarebytes security software. The poor imitation of the name could be a typographical error, or the developer was simply too lazy to do a quick fact check, and use the real name of the program instead.
It seems that this ransomware variant is in a trial run, as all versions detected still do not have any ability to encrypt a victim's files. Despite this, Christopher Boyd of the real Malwarebytes Labs thinks that the ransomware developer might be preparing for something big. He states:
At this point, we advise our readers to be very careful of what they download, and to make sure that the software that they are getting comes from a safe and legitimate website. Cybercriminals are always on the lookout for their next victim, so it's always a good idea to stay protected.
Source: Malwarebytes Labs via Graham Cluley
In an analysis by MalwareHunter, it was found out that the program is a cryptomalware called DetoxCrypto, which was initially detected back in August.
The malware's file properties were posted on VirusTotal, and it lists the following information:

Clearly enough, the malware developer wants people to think that the program is a legitimate Malwarebytes security software. The poor imitation of the name could be a typographical error, or the developer was simply too lazy to do a quick fact check, and use the real name of the program instead.
It seems that this ransomware variant is in a trial run, as all versions detected still do not have any ability to encrypt a victim's files. Despite this, Christopher Boyd of the real Malwarebytes Labs thinks that the ransomware developer might be preparing for something big. He states:
"What we’re seeing at the moment is what appears to be a kind of trial run for ransomware distribution. There’s a couple of Detox Ransomware files doing the rounds, and though they’re all broken in terms of functionality and / or download / dropper URLs, it’s still a possible sign of things shortly coming around the corner and worth giving a heads up on."
At this point, we advise our readers to be very careful of what they download, and to make sure that the software that they are getting comes from a safe and legitimate website. Cybercriminals are always on the lookout for their next victim, so it's always a good idea to stay protected.
Source: Malwarebytes Labs via Graham Cluley