A new ransomware is being spread called Rapid Ransomware that stays active after initially encrypting a computer and encrypts any new files that are created. While this behavior is not unique to Rapid, it is not a common behavior we see too often.
While it is not known how the Rapid Ransomware is being distributed, it has been infecting numerous people starting in January. According to statistics from
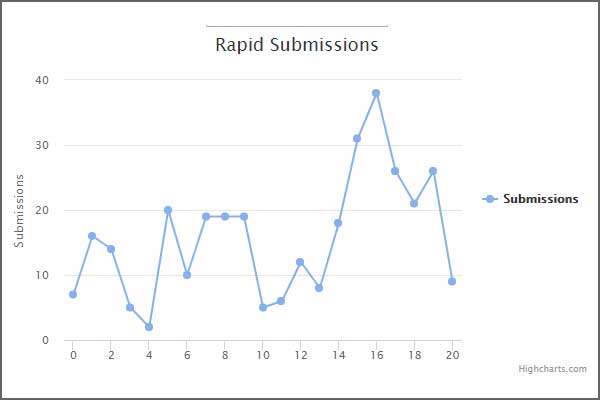
ID-Ransomware, the first submitted case was on January 3rd and since then there have been over 300 submissions. This is probably a small portion of the total victims, are there many who most likely did not utilize ID-Ransomware to identify the infection.
Rapid Ransomware Submissions to ID-Ransomware
How Rapid Ransomware encrypts a computer
When the ransomware runs, it will clear the Windows shadow volume copies, terminate database processes, and disables automatic repair. The processes that are terminated are sql.exe, sqlite.exe, and oracle.com and the commands that are executed are:
..
.....
..
........