- Jan 24, 2011
- 9,378
A real-time phishing campaign is targeting Brazil. This tactic is designed to emulate a banking Trojan by extracting critical data from its victims in real time via a live, interactive phishing attack.
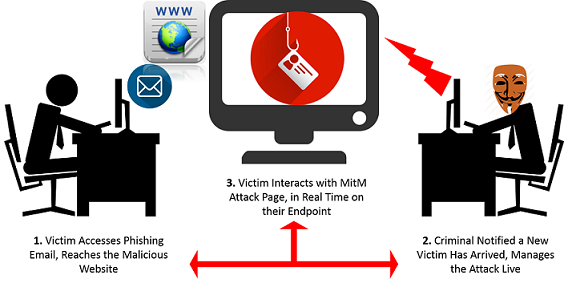
According to IBM X-Force, the phishing scheme takes place over a web session between the attacker and the victim. It is able to mimic a target website’s look and feel, more so than just an idle phishing page. From afar and behind the scenes, cyber-criminals impersonate the victim’s bank and ask for all kinds of account details. Data stolen through interactive phishing can be commercialized on underground boards.
“Most likely, the criminal will access the compromised account from the bank’s website to make a transaction in real time, all the while milking more authentication details from the unsuspecting victim,” they said, in a blog post. “The emergence of this new method will likely contribute to rises in fraud in Brazil over the coming months.”
Typical tactics include sending emails impersonating a bank, redirecting users to fake sites, deploying pharming attacks, inducing malicious proxy changes, or launching fake windows or images on the victim’s desktop to rob access credentials, account information, card data and personally identifiable information (PII). But all of these have one downside: Most banks require users to provide personal details in real time to authenticate customers during digital transactions.
“This usually foils fraud attacks,” the researchers noted. “These details are called out-of-band authentication because they happen away from the user’s browser, via a smartphone, card reader or numeric code chart.”
Interactive phishing takes place via a real-time web session that dupes users with a seamless flow of changing screens and messages controlled by the attacker from a remote server. And it can give cyber-criminals real-time access to a time-based code issued by the bank for a given transaction.
Read more: http://www.infosecurity-magazine.com/news/realtime-phishing-emerges-in-brazil/
According to IBM X-Force, the phishing scheme takes place over a web session between the attacker and the victim. It is able to mimic a target website’s look and feel, more so than just an idle phishing page. From afar and behind the scenes, cyber-criminals impersonate the victim’s bank and ask for all kinds of account details. Data stolen through interactive phishing can be commercialized on underground boards.
“Most likely, the criminal will access the compromised account from the bank’s website to make a transaction in real time, all the while milking more authentication details from the unsuspecting victim,” they said, in a blog post. “The emergence of this new method will likely contribute to rises in fraud in Brazil over the coming months.”
Typical tactics include sending emails impersonating a bank, redirecting users to fake sites, deploying pharming attacks, inducing malicious proxy changes, or launching fake windows or images on the victim’s desktop to rob access credentials, account information, card data and personally identifiable information (PII). But all of these have one downside: Most banks require users to provide personal details in real time to authenticate customers during digital transactions.
“This usually foils fraud attacks,” the researchers noted. “These details are called out-of-band authentication because they happen away from the user’s browser, via a smartphone, card reader or numeric code chart.”
Interactive phishing takes place via a real-time web session that dupes users with a seamless flow of changing screens and messages controlled by the attacker from a remote server. And it can give cyber-criminals real-time access to a time-based code issued by the bank for a given transaction.
Read more: http://www.infosecurity-magazine.com/news/realtime-phishing-emerges-in-brazil/
