A new research undertaken by a group of academics from the University of California San Diego has revealed for the first time that Bluetooth signals can be fingerprinted to track smartphones (and therefore, individuals).
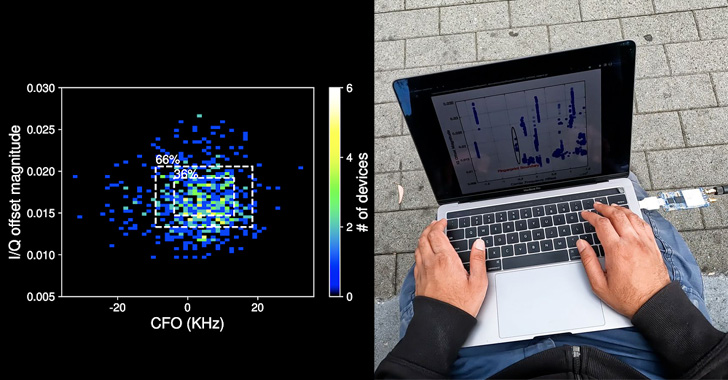
The identification, at its core, hinges on imperfections in the Bluetooth chipset hardware introduced during the manufacturing process, resulting in a "unique physical-layer fingerprint."
"To perform a physical-layer fingerprinting attack, the attacker must be equipped with a Software Defined Radio sniffer: a radio receiver capable of recording raw IQ radio signals," the researchers
said in a
new paper titled "Evaluating Physical-Layer BLE Location Tracking Attacks on Mobile Devices."
The
attack is made possible due to the ubiquitous nature of Bluetooth Low Energy (BLE) beacons that are continuously transmitted by modern devices to enable crucial functions such as
contact tracing during public health emergencies.
The hardware defects, on the other hand, stem from the fact that both Wi-Fi and BLE components are often integrated together into a specialized "
combo chip," effectively subjecting Bluetooth to the same set of metrics that can be used to uniquely fingerprint.......


