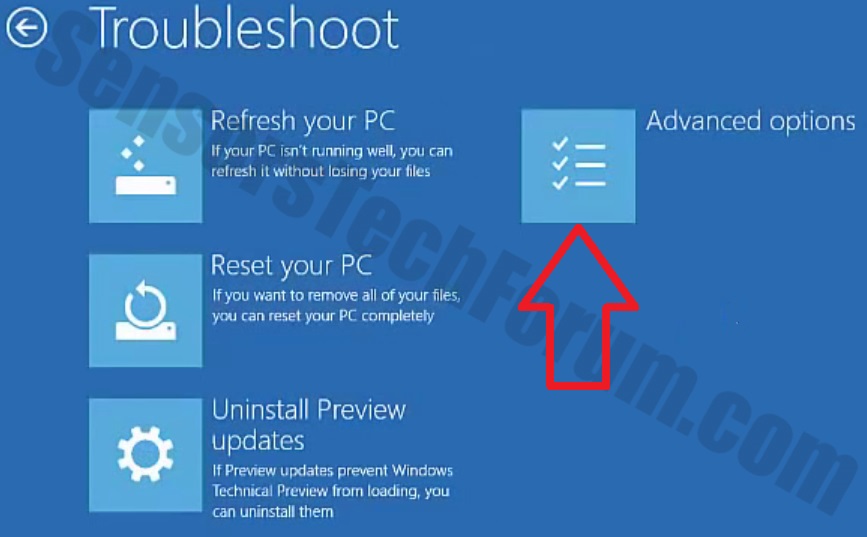
Tried downloading buildbox game maker and ended up being filled with trojans. got most cleaned off but some remnants remain. some questionable EXE's running are:
upmebwxsvc.exe
cgakwsz.exe
svrtizo.exe
igfxmtc.exe
Attached are Mbar, FRST, Addition, and below is GMER basic scan log:
GMER 2.2.19882 - GMER - Rootkit Detector and Remover
Rootkit scan 2017-12-29 00:58:11
Windows 6.1.7601 Service Pack 1 x64 \Device\Harddisk0\DR0 -> \Device\00000082 ATA_____ rev.CB6Q 465.76GB
Running: w1y60ggf.exe; Driver: C:\Users\Amen\AppData\Local\Temp\kwtdrpog.sys
---- Threads - GMER 2.2 ----
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:6892] 000007fef9a02be0
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:5456] 000007fede328a28
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:6492] 000007fede28d668
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:6476] 000007fede328a28
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:6624] 000007fef4b55124
---- Processes - GMER 2.2 ----
Library C:\Users\Amen\AppData\Local\cgakwsz\cgakwsz.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\cgakwsz.exe [3552] 00000000012e0000
Library C:\Users\Amen\AppData\Local\igfxmtc\igfxmtc.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\igfxmtc\igfxmtc.exe [4528] 0000000000ac0000
Library C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe [2196] 0000000000200000
Library C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe [3620] 0000000000200000
Library C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe [1168] 0000000000200000
Library C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe [848] 0000000000200000
---- Services - GMER 2.2 ----
Service C:\Windows\system32\drivers\5515452A.sys (*** hidden *** ) [DISABLED] 5515452A <-- ROOTKIT !!!
Service system32\drivers\coeosvyb.sys (*** hidden *** ) [BOOT] bkduogv <-- ROOTKIT !!!
Service C:\Windows\system32\drivers\mbamchameleon.sys (*** hidden *** ) [SYSTEM] mbamchameleon <-- ROOTKIT !!!
---- EOF - GMER 2.2 ----
upmebwxsvc.exe
cgakwsz.exe
svrtizo.exe
igfxmtc.exe
Attached are Mbar, FRST, Addition, and below is GMER basic scan log:
GMER 2.2.19882 - GMER - Rootkit Detector and Remover
Rootkit scan 2017-12-29 00:58:11
Windows 6.1.7601 Service Pack 1 x64 \Device\Harddisk0\DR0 -> \Device\00000082 ATA_____ rev.CB6Q 465.76GB
Running: w1y60ggf.exe; Driver: C:\Users\Amen\AppData\Local\Temp\kwtdrpog.sys
---- Threads - GMER 2.2 ----
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:6892] 000007fef9a02be0
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:5456] 000007fede328a28
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:6492] 000007fede28d668
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:6476] 000007fede328a28
Thread C:\Program Files\Windows Media Player\wmpnetwk.exe [6148:6624] 000007fef4b55124
---- Processes - GMER 2.2 ----
Library C:\Users\Amen\AppData\Local\cgakwsz\cgakwsz.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\cgakwsz.exe [3552] 00000000012e0000
Library C:\Users\Amen\AppData\Local\igfxmtc\igfxmtc.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\igfxmtc\igfxmtc.exe [4528] 0000000000ac0000
Library C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe [2196] 0000000000200000
Library C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe [3620] 0000000000200000
Library C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe [1168] 0000000000200000
Library C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe (*** suspicious ***) @ C:\Users\Amen\AppData\Local\cgakwsz\svrtizo.exe [848] 0000000000200000
---- Services - GMER 2.2 ----
Service C:\Windows\system32\drivers\5515452A.sys (*** hidden *** ) [DISABLED] 5515452A <-- ROOTKIT !!!
Service system32\drivers\coeosvyb.sys (*** hidden *** ) [BOOT] bkduogv <-- ROOTKIT !!!
Service C:\Windows\system32\drivers\mbamchameleon.sys (*** hidden *** ) [SYSTEM] mbamchameleon <-- ROOTKIT !!!
---- EOF - GMER 2.2 ----