Hey guys, just to introduce you the new version of RunPE Detector.
What is RunPE Detector:

Changelog:
GENERAL
Download link : Download - Phrozen
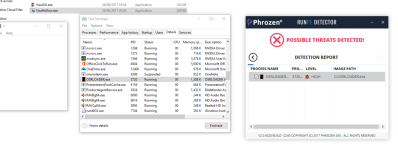
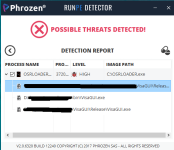
Some Pictures :


What is RunPE Detector:

RunPE Detector is a new concept we invented for near-100% detection of malware mounted in your system’s memory. Hackers use the RunPE process to evade firewalls antivirus detection by hijacking legit processes. With RunPE Detector, you can uncover the malicious code and prevent it from further infecting your system.
Changelog:
GENERAL
- Project recoded from scratch
- Better Pe File / Memory analysis
- Faster analysis
- Stability and memory usage improved
- More efficient code to unlock and remove threats
- Phrozen Material Support Added
Download link : Download - Phrozen
Some Pictures :