- Jul 27, 2015
- 5,458
Over the past several months, Cisco Talos has seen attackers carrying out ongoing email-based malware distribution campaigns to distribute various malware payloads. These email campaigns feature several notable characteristics that appear designed to evade detection and maximize the effectiveness of these campaigns. The use of web-based contact forms, legitimate hosting platforms, and a specific crypter make analysis and detection more difficult. All of the malware samples associated with these campaigns feature a modified DOS header containing the string "Salfram," making them extremely easy to track over time. The crypter used in these campaigns is undergoing active development and improvements to obfuscate the contents of malware payloads. Additionally, the crypter uses several effective techniques to make the detection and analysis of the final malware payload more difficult. It obfuscates the original payload binaries in a way that results in payloads that appear completely different from each other after being packed using the same crypter. It even takes a great amount of effort to compare the packed binaries in a disassembler and determine if the same packer was used.
The email distribution campaigns associated with these malware payloads feature characteristics designed to evade detection and make analysis and tracking more difficult. In most cases, the threat actor was initiating email-based communications with potential victims using the contact forms present on the victim organization's website. This results in email communications that appear to originate from legitimate sources which may allow the adversaries to evade some email security mechanisms. In the messages, the attacker purports to be the copyright owner of images that the attacker claims they found hosted on the target organization's website without their permission. The email contents are somewhat customized, listing the target organization's domain as the website containing the infringing content and prompting them to access a hyperlink present in the email. Figure 1 is an example of one of the emails associated with one of these campaigns.
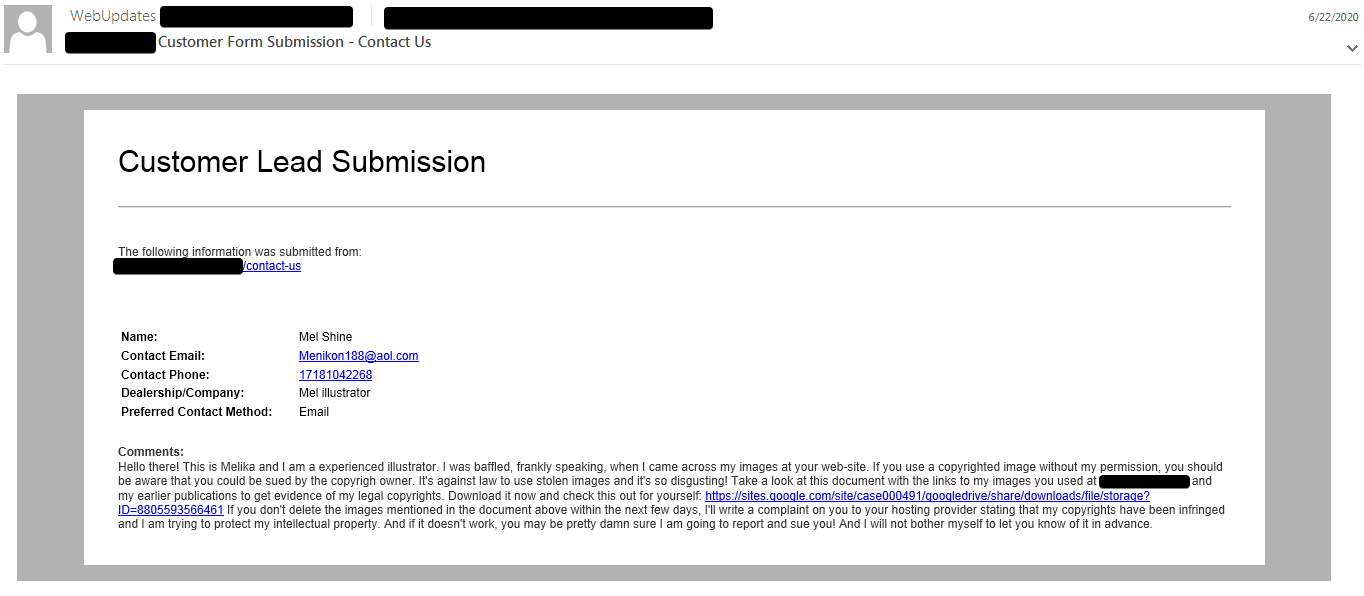
In analyzing malicious contact form submissions associated with these campaigns, we obtained information about the system used to submit the form contents. The contact form submissions were performed via proxy servers using an automated mechanism, such as scripting, to generate and submit the data.
The majority of the emails contained links to a malicious file hosted on Google Drive. The directory structure and parameter values rotate frequently across various emails. Figure 3 lists some examples of these URLs. Again, the use of a legitimate web platform for hosting the malicious content may provide another way for the attacker to evade various protections that may be deployed in environments that they are targeting. When the URL is accessed, the victim is delivered a malicious file, often a Microsoft Office document similar to the one in Figure 4.
These documents contain malicious macros that initiate the infection process and are responsible for retrieving a malicious payload and executing it to infect the system. The payloads delivered have varied over time. Over the past several months, we have observed campaigns being used to deliver various information stealers, banking trojans and other malware loaders including but not limited to Gozi ISFB, ZLoader, SmokeLoader, Oski, AveMaria and Cobalt Strike payloads, among others. We also discovered infection chains that deliver multiple payloads to a single victim as part of a multi-stage infection process. While the payload delivery features several distinct malware families, in all of the campaigns observed, the initial malware payloads used the same crypter, which obfuscates the malicious contents present in the binary executable and make analysis more difficult.
Full source :

Salfram: Robbing the place without removing your name tag
Threat summary * Cisco Talos recently uncovered a series of email campaigns utilizing links to malicious documents hosted on legitimate file-sharing platforms to spread malware. * The campaigns distributed various malware payloads including Gozi ISFB, ZLoader, SmokeLoader and AveMaria, among...
 blog.talosintelligence.com
blog.talosintelligence.com