- May 17, 2015
- 669
Sandboxie+ Release v1.0.1 / 5.55.1 Latest Pre-release
https://github.com/sandboxie-plus/Sandboxie/releases/tag/1.0.1
This build fixes bugs introduced in the last pre release build
Note:Latest Pre-release
1.0.x new feature summary:
The first major feature is Privacy Mode, here most of the PC is set to be treated like a Write[File/Key]Path meaning the sandbox locations are writable but the unsandboxed locations are not readable. The Hard disk appears empty except for C:\Windows and C:\Program Files and the registry only allows reading of the machine but not user root keys. This way sandboxed processes can work but can not access private user data.
To make this mode useful an other feature has been implemented called “Rule Specificity” it can be enabled independently but is always enabled in Privacy enhanced boxes. It allows to specify rules to override other rules, this is not based on specifying an order or priority, but instead by measuring how specific a rule is and always attributing the highest priority to the most specific rule.
Here the specificity is measures by the path length that matches the rule, except the last wildcard.
So for example, the built in privacy rules plus a custom one
OpenFilePath=%AppData%\Mozilla\Firefox\Profiles*
NormalFilePath=C:\Program Files*
NormalFilePath=C:\Windows*
WriteFilePath=C:*
Here the rules are ordered by their specificity.
Also there is a new type Normal[File/Key/Ipc]Path which defines a default sandbox behavior for a path.
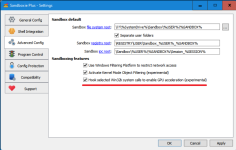
The next major feature is "App Compartment" mode "NoSecurityIsolation=y", this is a new mode of operation which disables the token based security isolation, which brings the security down to the level of other sand boxing solutions, but by doing so greatly improves compatibility. For all use cases where the goal is only compartmentalization, running multiple instances, etc, but not hard core security this mode is preferable as it should avoid many typical sandboxie issues caused by processes running with a heavily restricted token.
In this mode file system and registry accesses are still being filtered to enforce the access rules, this filtering can be disabled with "NoSecurityFiltering=y"
To ensure this “unsecure” mode is at least as secure as the sandboxing offered by other sandboxing products, a new object access filter was added that can be enabled with "EnableObjectFiltering=y" in the global settings.
If you have issues with an update installation, just uninstall the previous version keeping the sandboxie.ini and reinstall the new build.
You can support the project through donations, any help will be greatly appreciated.

 github.com
github.com
Edit: Latest changed to Pre-release
https://github.com/sandboxie-plus/Sandboxie/releases/tag/1.0.1
This build fixes bugs introduced in the last pre release build
Note:
1.0.x new feature summary:
The first major feature is Privacy Mode, here most of the PC is set to be treated like a Write[File/Key]Path meaning the sandbox locations are writable but the unsandboxed locations are not readable. The Hard disk appears empty except for C:\Windows and C:\Program Files and the registry only allows reading of the machine but not user root keys. This way sandboxed processes can work but can not access private user data.
To make this mode useful an other feature has been implemented called “Rule Specificity” it can be enabled independently but is always enabled in Privacy enhanced boxes. It allows to specify rules to override other rules, this is not based on specifying an order or priority, but instead by measuring how specific a rule is and always attributing the highest priority to the most specific rule.
Here the specificity is measures by the path length that matches the rule, except the last wildcard.
So for example, the built in privacy rules plus a custom one
OpenFilePath=%AppData%\Mozilla\Firefox\Profiles*
NormalFilePath=C:\Program Files*
NormalFilePath=C:\Windows*
WriteFilePath=C:*
Here the rules are ordered by their specificity.
Also there is a new type Normal[File/Key/Ipc]Path which defines a default sandbox behavior for a path.
The next major feature is "App Compartment" mode "NoSecurityIsolation=y", this is a new mode of operation which disables the token based security isolation, which brings the security down to the level of other sand boxing solutions, but by doing so greatly improves compatibility. For all use cases where the goal is only compartmentalization, running multiple instances, etc, but not hard core security this mode is preferable as it should avoid many typical sandboxie issues caused by processes running with a heavily restricted token.
In this mode file system and registry accesses are still being filtered to enforce the access rules, this filtering can be disabled with "NoSecurityFiltering=y"
To ensure this “unsecure” mode is at least as secure as the sandboxing offered by other sandboxing products, a new object access filter was added that can be enabled with "EnableObjectFiltering=y" in the global settings.
If you have issues with an update installation, just uninstall the previous version keeping the sandboxie.ini and reinstall the new build.
You can support the project through donations, any help will be greatly appreciated.
Release Release v1.0.1 / 5.55.1 · sandboxie-plus/Sandboxie
This build fixes bugs introduced in the last pre-release build Known Issues printing does not work, will be fixed in the next release If you have issues with an update installation, just uninstal...
Edit: Latest changed to Pre-release
Last edited: