- May 17, 2015
- 730
Sandboxie+ Release v1.0.16 / 5.55.16
https://github.com/sandboxie-plus/Sandboxie/releases/tag/1.0.16
Note: Pre-release
This build fixes a couple of issues, but also introduces a major change in how sandboxie controls access to process memory.
Before this build sandboxie allowed sandboxed programs to read the memory of any unsandboxed program belonging to the current user, this is obviously a bad idea if your goals is not only infection prevention but also data protection. Hence with 1.0.16 onwards sandboxie will not allow for PROCESS_VM_READ on unsandboxed processes or processes belonging to other boxes.
To facilitate compatibility this build introduces a IPC options, with ReadIpcPath=$program.exe any unboxed process can be configured to allow for PROCESS_VM_READ, it is also possible to restore the old behavior entirely by specifying ReadIpcPath=$:*
By default the only process whos memory can be read is explorer.exe many processes want that and explorer should not keep any secrets normally anyways. To block this you can use ClosedIpcPath=$:explorer.exe
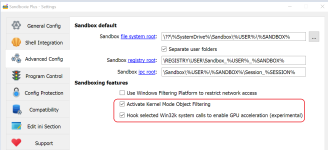
To facilitate optimal process isoaltion the EnableObjectFiltering option is now on by default, although this only applies for new installations, hence its recommend for existing installation to go to settings->advanced and enable it explicitly.
Other changes in this build include a simple resource access monitor mode and a change how process paths are resolved for sandboxed processes, this should fix a couple of issues.
Given that this build changes a couple of core mechanics it is possible that in some special cases this can lead to an incompatibility.
If you have issues with an update installation, just uninstall the previous version keeping the sandboxie.ini and reinstall the new build.
You can support the project through donations, any help will be greatly appreciated.

 github.com
github.com
https://github.com/sandboxie-plus/Sandboxie/releases/tag/1.0.16
Note: Pre-release
This build fixes a couple of issues, but also introduces a major change in how sandboxie controls access to process memory.
Before this build sandboxie allowed sandboxed programs to read the memory of any unsandboxed program belonging to the current user, this is obviously a bad idea if your goals is not only infection prevention but also data protection. Hence with 1.0.16 onwards sandboxie will not allow for PROCESS_VM_READ on unsandboxed processes or processes belonging to other boxes.
To facilitate compatibility this build introduces a IPC options, with ReadIpcPath=$program.exe any unboxed process can be configured to allow for PROCESS_VM_READ, it is also possible to restore the old behavior entirely by specifying ReadIpcPath=$:*
By default the only process whos memory can be read is explorer.exe many processes want that and explorer should not keep any secrets normally anyways. To block this you can use ClosedIpcPath=$:explorer.exe
To facilitate optimal process isoaltion the EnableObjectFiltering option is now on by default, although this only applies for new installations, hence its recommend for existing installation to go to settings->advanced and enable it explicitly.
Other changes in this build include a simple resource access monitor mode and a change how process paths are resolved for sandboxed processes, this should fix a couple of issues.
Given that this build changes a couple of core mechanics it is possible that in some special cases this can lead to an incompatibility.
If you have issues with an update installation, just uninstall the previous version keeping the sandboxie.ini and reinstall the new build.
You can support the project through donations, any help will be greatly appreciated.
Release Release v1.0.16 / 5.55.16 · sandboxie-plus/Sandboxie
This build fixes a couple of issues, but also introduces a major change in how sandboxie controls access to process memory. Before this build sandboxie allowed sandboxed programs to read the memory...
Last edited: