I had read previous thread with same kind of scareware. But don't work for me, seem I can not get into the system anyway.
scareware lock computer
- Thread starter amandamcpherson
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hi and welcome to MalwareTips! 
I'm Fiery and I would gladly assist you in removing the malware on your computer.
Before we start:
Please print these instruction out so that you know what you are doing. Do the below on another clean PC and use the bootable CD to boot your infected PC.
I'm Fiery and I would gladly assist you in removing the malware on your computer.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
Please print these instruction out so that you know what you are doing. Do the below on another clean PC and use the bootable CD to boot your infected PC.
- Download OTLPE to your desktop
- Double click OTLPEStd.exe and this will then open imgburn to burn the file to CD
- Reboot your system using the boot CD you just created.
Note : If you do not know how to set your computer to boot from CD follow the steps here - Wait for the CD to detect your hardware and load the operating system
- Your system should now display a Reatogo desktop
Note : as you are running from CD it is not exactly speedy
While in OTLPE, double click the OTLPE icon.
- Select the Windows folder of the infected drive if it asks for a location.
- When asked Do you wish to load the remote registry, select Yes.
- When asked Do you wish to load remote user profile(s) for scanning, select Yes.
- Ensure the box Automatically Load All Remaining Users is checked and press OK.
- OTL should now start
- Check the boxes beside LOP Check and Purity Check
- Press the Run Scan button
- When finished, the file will be saved in drive C:\OTL.txt
- Copy this file to a USB drive if you do not have internet connection on the system.
- Please attach the content of OTL.txt in your next reply.
Fiery said:Hi and welcome to MalwareTips!
I'm Fiery and I would gladly assist you in removing the malware on your computer.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
Please print these instruction out so that you know what you are doing. Do the below on another clean PC and use the bootable CD to boot your infected PC.
- Download OTLPE to your desktop
- Double click OTLPEStd.exe and this will then open imgburn to burn the file to CD
- Reboot your system using the boot CD you just created.
Note : If you do not know how to set your computer to boot from CD follow the steps here- Wait for the CD to detect your hardware and load the operating system
- Your system should now display a Reatogo desktop
Note : as you are running from CD it is not exactly speedy
While in OTLPE, double click the OTLPE icon.
- Select the Windows folder of the infected drive if it asks for a location.
- When asked Do you wish to load the remote registry, select Yes.
- When asked Do you wish to load remote user profile(s) for scanning, select Yes.
- Ensure the box Automatically Load All Remaining Users is checked and press OK.
- OTL should now start
- Check the boxes beside LOP Check and Purity Check
- Press the Run Scan button
- When finished, the file will be saved in drive C:\OTL.txt
- Copy this file to a USB drive if you do not have internet connection on the system.
- Please attach the content of OTL.txt in your next reply.
OTL logfile created on: 3/2/2013 11:14:49 PM - Run
OTLPE by OldTimer - Version 3.1.48.0 Folder = X:\Programs\OTLPE
Microsoft Windows XP Service Pack 3 (Version = 5.1.2600) - Type = SYSTEM
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
3.00 Gb Total Physical Memory | 3.00 Gb Available Physical Memory | 92.00% Memory free
3.00 Gb Paging File | 3.00 Gb Available in Paging File | 98.00% Paging File free
Paging file location(s): C:\pagefile.sys 2046 4092 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 149.05 Gb Total Space | 113.24 Gb Free Space | 75.98% Space Free | Partition Type: NTFS
Drive X: | 284.12 Mb Total Space | 0.00 Mb Free Space | 0.00% Space Free | Partition Type: CDFS
Computer Name: REATOGO | User Name: SYSTEM
Boot Mode: Normal | Scan Mode: All users
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days
Using ControlSet: ControlSet003
========== Win32 Services (SafeList) ==========
SRV - File not found [Disabled] -- -- (HidServ)
SRV - [2013/03/02 20:36:26 | 000,106,280 | ---- | M] (SurfRight B.V.) [Auto] -- C:\Program Files\HitmanPro\hmpsched.exe -- (HitmanProScheduler)
SRV - [2013/02/20 07:38:08 | 000,093,984 | ---- | M] (Conduit) [Auto] -- C:\Program Files\SearchProtect\bin\CltMngSvc.exe -- (CltMngSvc)
SRV - [2013/02/05 16:09:05 | 000,651,720 | ---- | M] (Macrovision Europe Ltd.) [On_Demand] -- C:\Program Files\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe -- (FLEXnet Licensing Service)
SRV - [2012/12/13 12:01:56 | 000,159,640 | ---- | M] (McAfee, Inc.) [Auto] -- C:\WINDOWS\System32\mfevtps.exe -- (mfevtp)
SRV - [2012/12/13 12:01:54 | 000,167,344 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\Common Files\McAfee\SystemCore\mcshield.exe -- (McShield)
SRV - [2012/08/21 16:06:00 | 000,132,712 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\Common Framework\FrameworkService.exe -- (McAfeeFramework)
SRV - [2012/07/03 17:14:52 | 000,163,200 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\Common Files\McAfee\SystemCore\mfefire.exe -- (mfefire)
SRV - [2012/07/03 17:14:50 | 000,489,120 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\Host Intrusion Prevention\FireSvc.exe -- (enterceptAgent)
SRV - [2011/12/02 11:55:28 | 000,161,664 | ---- | M] (Oracle Corporation) [Auto] -- C:\Program Files\Java\jre7\bin\jqs.exe -- (JavaQuickStarterService)
SRV - [2011/09/14 20:08:00 | 000,209,760 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\VirusScan Enterprise\vstskmgr.exe -- (McTaskManager)
SRV - [2011/09/09 13:17:30 | 000,245,760 | ---- | M] (Avaya Inc.) [Auto] -- C:\Program Files\Avaya\Avaya one-X Communicator\QosServM.exe -- (iClarityQoSService)
SRV - [2009/09/18 03:00:00 | 000,764,768 | ---- | M] (Microsoft Corporation) [Auto] -- C:\WINDOWS\system32\CCM\CcmExec.exe -- (CcmExec)
SRV - [2009/09/18 03:00:00 | 000,246,624 | ---- | M] (Microsoft Corporation) [On_Demand] -- C:\WINDOWS\System32\CCM\TSManager.exe -- (smstsmgr)
========== Driver Services (SafeList) ==========
DRV - File not found [Kernel | On_Demand] -- -- (WDICA)
DRV - File not found [Kernel | On_Demand] -- -- (PDRFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDRELI)
DRV - File not found [Kernel | On_Demand] -- -- (PDFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDCOMP)
DRV - File not found [Kernel | System] -- -- (PCIDump)
DRV - File not found [Kernel | On_Demand] -- -- (mfeavfk01)
DRV - File not found [Kernel | System] -- -- (lbrtfdc)
DRV - File not found [Kernel | System] -- -- (Changer)
DRV - [2013/01/31 03:19:50 | 000,181,344 | ---- | M] (DEVGURU Co., LTD.(www.devguru.co.kr)) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ssudmdm.sys -- (ssudmdm) SAMSUNG Mobile USB Modem Drivers (DEVGURU Ver.)
DRV - [2013/01/31 03:19:50 | 000,083,168 | ---- | M] (DEVGURU Co., LTD.(www.devguru.co.kr)) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ssudbus.sys -- (dg_ssudbus) SAMSUNG Mobile USB Composite Device Driver (DEVGURU Ver.)
DRV - [2012/12/13 12:01:56 | 000,090,368 | ---- | M] (McAfee, Inc.) [Kernel | System] -- C:\WINDOWS\system32\drivers\mfetdi2k.sys -- (mfetdi2k)
DRV - [2012/12/13 12:01:56 | 000,087,816 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mferkdet.sys -- (mferkdet)
DRV - [2012/12/13 12:01:55 | 000,477,584 | ---- | M] (McAfee, Inc.) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\mfehidk.sys -- (mfehidk)
DRV - [2012/12/13 12:01:55 | 000,215,024 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfeavfk.sys -- (mfeavfk)
DRV - [2012/12/13 12:01:55 | 000,121,544 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfeapfk.sys -- (mfeapfk)
DRV - [2012/12/13 12:01:55 | 000,059,616 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfebopk.sys -- (mfebopk)
DRV - [2012/07/03 17:14:52 | 000,348,880 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfefirek.sys -- (mfefirek)
DRV - [2012/07/03 17:14:52 | 000,083,920 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfendisk.sys -- (mfendiskmp)
DRV - [2012/07/03 17:14:52 | 000,083,920 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfendisk.sys -- (mfendisk)
DRV - [2012/07/03 17:14:50 | 000,147,248 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\HipShieldK.sys -- (HipShieldK)
DRV - [2012/07/03 17:14:50 | 000,042,016 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\FireNfcp.sys -- (FireNfcp)
DRV - [2010/09/21 14:13:40 | 000,156,160 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\b57xp32.sys -- (b57w2k)
DRV - [2009/09/18 03:00:00 | 000,020,848 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\CCM\PrepDrv.sys -- (prepdrvr)
DRV - [2009/08/21 18:24:26 | 000,040,320 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\nmnt.sys -- (nm)
DRV - [2008/10/20 19:08:06 | 000,012,448 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\smsmdm.sys -- (smsmdd)
DRV - [2008/05/06 16:06:00 | 000,011,520 | ---- | M] (Western Digital Technologies) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\wdcsam.sys -- (WDC_SAM)
DRV - [2007/12/14 08:21:56 | 000,290,816 | ---- | M] (Texas Instruments) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\tifm21.sys -- (tifm21)
DRV - [2007/10/31 09:23:20 | 002,236,544 | ---- | M] (Intel Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\NETw4x32.sys -- (NETw4x32) Intel(R)
DRV - [2007/08/28 14:47:36 | 000,146,560 | ---- | M] (AuthenTec, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\atswpdrv.sys -- (ATSWPDRV) AuthenTec TruePrint USB Driver (SwipeSensor)
DRV - [2007/06/18 15:12:04 | 000,016,768 | ---- | M] (Hewlett-Packard Development Company, L.P.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\HpqKbFiltr.sys -- (HpqKbFiltr)
DRV - [2007/05/09 12:27:00 | 000,097,280 | ---- | M] (Texas Instruments) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\gtipci21.sys -- (GTIPCI21)
DRV - [2007/02/01 08:29:52 | 000,024,304 | ---- | M] (PCTEL Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\PCTINDIS5.sys -- (PCTINDIS5)
DRV - [2006/08/28 13:40:48 | 001,160,320 | ---- | M] (Agere Systems) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\AGRSM.sys -- (AgereSoftModem)
DRV - [2006/08/18 12:18:08 | 000,009,400 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLADResM.SYS -- (DLADResM)
DRV - [2006/08/18 12:17:46 | 000,035,096 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLABMFSM.SYS -- (DLABMFSM)
DRV - [2006/08/18 12:17:44 | 000,097,848 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAUDF_M.SYS -- (DLAUDF_M)
DRV - [2006/08/18 12:17:44 | 000,094,648 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAUDFAM.SYS -- (DLAUDFAM)
DRV - [2006/08/18 12:17:42 | 000,026,008 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAOPIOM.SYS -- (DLAOPIOM)
DRV - [2006/08/18 12:17:40 | 000,032,472 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLABOIOM.SYS -- (DLABOIOM)
DRV - [2006/08/18 12:17:38 | 000,104,472 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAIFS_M.SYS -- (DLAIFS_M)
DRV - [2006/08/18 12:17:38 | 000,014,520 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAPoolM.SYS -- (DLAPoolM)
DRV - [2006/08/11 09:35:18 | 000,012,920 | ---- | M] (Roxio) [File_System | System] -- C:\WINDOWS\system32\drivers\DLACDBHM.SYS -- (DLACDBHM)
DRV - [2006/08/11 09:35:16 | 000,028,184 | ---- | M] (Roxio) [File_System | System] -- C:\WINDOWS\system32\drivers\DLARTL_M.SYS -- (DLARTL_M)
DRV - [2006/06/28 08:54:00 | 000,009,472 | ---- | M] (Hewlett-Packard Development Company, L.P.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\CPQBttn.sys -- (HBtnKey)
DRV - [2006/01/10 00:00:04 | 000,022,016 | ---- | M] (Hewlett-Packard Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Accelerometer.sys -- (Accelerometer)
DRV - [2006/01/10 00:00:04 | 000,017,920 | ---- | M] (Hewlett-Packard Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\hpdskflt.sys -- (hpdskflt)
DRV - [2005/11/29 15:56:28 | 000,036,768 | ---- | M] (Infineon Technologies AG) [Kernel | System] -- C:\WINDOWS\System32\drivers\psd.sys -- (PersonalSecureDrive)
DRV - [2005/10/21 10:19:34 | 000,036,352 | ---- | M] (Infineon Technologies AG) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ifxtpm.sys -- (IFXTPM)
DRV - [2001/08/17 11:10:28 | 000,035,913 | ---- | M] (SMC) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\smcirda.sys -- (SMCIRDA)
========== Standard Registry (SafeList) ==========
OTLPE by OldTimer - Version 3.1.48.0 Folder = X:\Programs\OTLPE
Microsoft Windows XP Service Pack 3 (Version = 5.1.2600) - Type = SYSTEM
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
3.00 Gb Total Physical Memory | 3.00 Gb Available Physical Memory | 92.00% Memory free
3.00 Gb Paging File | 3.00 Gb Available in Paging File | 98.00% Paging File free
Paging file location(s): C:\pagefile.sys 2046 4092 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 149.05 Gb Total Space | 113.24 Gb Free Space | 75.98% Space Free | Partition Type: NTFS
Drive X: | 284.12 Mb Total Space | 0.00 Mb Free Space | 0.00% Space Free | Partition Type: CDFS
Computer Name: REATOGO | User Name: SYSTEM
Boot Mode: Normal | Scan Mode: All users
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days
Using ControlSet: ControlSet003
========== Win32 Services (SafeList) ==========
SRV - File not found [Disabled] -- -- (HidServ)
SRV - [2013/03/02 20:36:26 | 000,106,280 | ---- | M] (SurfRight B.V.) [Auto] -- C:\Program Files\HitmanPro\hmpsched.exe -- (HitmanProScheduler)
SRV - [2013/02/20 07:38:08 | 000,093,984 | ---- | M] (Conduit) [Auto] -- C:\Program Files\SearchProtect\bin\CltMngSvc.exe -- (CltMngSvc)
SRV - [2013/02/05 16:09:05 | 000,651,720 | ---- | M] (Macrovision Europe Ltd.) [On_Demand] -- C:\Program Files\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe -- (FLEXnet Licensing Service)
SRV - [2012/12/13 12:01:56 | 000,159,640 | ---- | M] (McAfee, Inc.) [Auto] -- C:\WINDOWS\System32\mfevtps.exe -- (mfevtp)
SRV - [2012/12/13 12:01:54 | 000,167,344 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\Common Files\McAfee\SystemCore\mcshield.exe -- (McShield)
SRV - [2012/08/21 16:06:00 | 000,132,712 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\Common Framework\FrameworkService.exe -- (McAfeeFramework)
SRV - [2012/07/03 17:14:52 | 000,163,200 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\Common Files\McAfee\SystemCore\mfefire.exe -- (mfefire)
SRV - [2012/07/03 17:14:50 | 000,489,120 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\Host Intrusion Prevention\FireSvc.exe -- (enterceptAgent)
SRV - [2011/12/02 11:55:28 | 000,161,664 | ---- | M] (Oracle Corporation) [Auto] -- C:\Program Files\Java\jre7\bin\jqs.exe -- (JavaQuickStarterService)
SRV - [2011/09/14 20:08:00 | 000,209,760 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\VirusScan Enterprise\vstskmgr.exe -- (McTaskManager)
SRV - [2011/09/09 13:17:30 | 000,245,760 | ---- | M] (Avaya Inc.) [Auto] -- C:\Program Files\Avaya\Avaya one-X Communicator\QosServM.exe -- (iClarityQoSService)
SRV - [2009/09/18 03:00:00 | 000,764,768 | ---- | M] (Microsoft Corporation) [Auto] -- C:\WINDOWS\system32\CCM\CcmExec.exe -- (CcmExec)
SRV - [2009/09/18 03:00:00 | 000,246,624 | ---- | M] (Microsoft Corporation) [On_Demand] -- C:\WINDOWS\System32\CCM\TSManager.exe -- (smstsmgr)
========== Driver Services (SafeList) ==========
DRV - File not found [Kernel | On_Demand] -- -- (WDICA)
DRV - File not found [Kernel | On_Demand] -- -- (PDRFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDRELI)
DRV - File not found [Kernel | On_Demand] -- -- (PDFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDCOMP)
DRV - File not found [Kernel | System] -- -- (PCIDump)
DRV - File not found [Kernel | On_Demand] -- -- (mfeavfk01)
DRV - File not found [Kernel | System] -- -- (lbrtfdc)
DRV - File not found [Kernel | System] -- -- (Changer)
DRV - [2013/01/31 03:19:50 | 000,181,344 | ---- | M] (DEVGURU Co., LTD.(www.devguru.co.kr)) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ssudmdm.sys -- (ssudmdm) SAMSUNG Mobile USB Modem Drivers (DEVGURU Ver.)
DRV - [2013/01/31 03:19:50 | 000,083,168 | ---- | M] (DEVGURU Co., LTD.(www.devguru.co.kr)) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ssudbus.sys -- (dg_ssudbus) SAMSUNG Mobile USB Composite Device Driver (DEVGURU Ver.)
DRV - [2012/12/13 12:01:56 | 000,090,368 | ---- | M] (McAfee, Inc.) [Kernel | System] -- C:\WINDOWS\system32\drivers\mfetdi2k.sys -- (mfetdi2k)
DRV - [2012/12/13 12:01:56 | 000,087,816 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mferkdet.sys -- (mferkdet)
DRV - [2012/12/13 12:01:55 | 000,477,584 | ---- | M] (McAfee, Inc.) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\mfehidk.sys -- (mfehidk)
DRV - [2012/12/13 12:01:55 | 000,215,024 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfeavfk.sys -- (mfeavfk)
DRV - [2012/12/13 12:01:55 | 000,121,544 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfeapfk.sys -- (mfeapfk)
DRV - [2012/12/13 12:01:55 | 000,059,616 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfebopk.sys -- (mfebopk)
DRV - [2012/07/03 17:14:52 | 000,348,880 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfefirek.sys -- (mfefirek)
DRV - [2012/07/03 17:14:52 | 000,083,920 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfendisk.sys -- (mfendiskmp)
DRV - [2012/07/03 17:14:52 | 000,083,920 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfendisk.sys -- (mfendisk)
DRV - [2012/07/03 17:14:50 | 000,147,248 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\HipShieldK.sys -- (HipShieldK)
DRV - [2012/07/03 17:14:50 | 000,042,016 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\FireNfcp.sys -- (FireNfcp)
DRV - [2010/09/21 14:13:40 | 000,156,160 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\b57xp32.sys -- (b57w2k)
DRV - [2009/09/18 03:00:00 | 000,020,848 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\CCM\PrepDrv.sys -- (prepdrvr)
DRV - [2009/08/21 18:24:26 | 000,040,320 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\nmnt.sys -- (nm)
DRV - [2008/10/20 19:08:06 | 000,012,448 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\smsmdm.sys -- (smsmdd)
DRV - [2008/05/06 16:06:00 | 000,011,520 | ---- | M] (Western Digital Technologies) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\wdcsam.sys -- (WDC_SAM)
DRV - [2007/12/14 08:21:56 | 000,290,816 | ---- | M] (Texas Instruments) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\tifm21.sys -- (tifm21)
DRV - [2007/10/31 09:23:20 | 002,236,544 | ---- | M] (Intel Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\NETw4x32.sys -- (NETw4x32) Intel(R)
DRV - [2007/08/28 14:47:36 | 000,146,560 | ---- | M] (AuthenTec, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\atswpdrv.sys -- (ATSWPDRV) AuthenTec TruePrint USB Driver (SwipeSensor)
DRV - [2007/06/18 15:12:04 | 000,016,768 | ---- | M] (Hewlett-Packard Development Company, L.P.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\HpqKbFiltr.sys -- (HpqKbFiltr)
DRV - [2007/05/09 12:27:00 | 000,097,280 | ---- | M] (Texas Instruments) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\gtipci21.sys -- (GTIPCI21)
DRV - [2007/02/01 08:29:52 | 000,024,304 | ---- | M] (PCTEL Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\PCTINDIS5.sys -- (PCTINDIS5)
DRV - [2006/08/28 13:40:48 | 001,160,320 | ---- | M] (Agere Systems) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\AGRSM.sys -- (AgereSoftModem)
DRV - [2006/08/18 12:18:08 | 000,009,400 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLADResM.SYS -- (DLADResM)
DRV - [2006/08/18 12:17:46 | 000,035,096 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLABMFSM.SYS -- (DLABMFSM)
DRV - [2006/08/18 12:17:44 | 000,097,848 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAUDF_M.SYS -- (DLAUDF_M)
DRV - [2006/08/18 12:17:44 | 000,094,648 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAUDFAM.SYS -- (DLAUDFAM)
DRV - [2006/08/18 12:17:42 | 000,026,008 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAOPIOM.SYS -- (DLAOPIOM)
DRV - [2006/08/18 12:17:40 | 000,032,472 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLABOIOM.SYS -- (DLABOIOM)
DRV - [2006/08/18 12:17:38 | 000,104,472 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAIFS_M.SYS -- (DLAIFS_M)
DRV - [2006/08/18 12:17:38 | 000,014,520 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAPoolM.SYS -- (DLAPoolM)
DRV - [2006/08/11 09:35:18 | 000,012,920 | ---- | M] (Roxio) [File_System | System] -- C:\WINDOWS\system32\drivers\DLACDBHM.SYS -- (DLACDBHM)
DRV - [2006/08/11 09:35:16 | 000,028,184 | ---- | M] (Roxio) [File_System | System] -- C:\WINDOWS\system32\drivers\DLARTL_M.SYS -- (DLARTL_M)
DRV - [2006/06/28 08:54:00 | 000,009,472 | ---- | M] (Hewlett-Packard Development Company, L.P.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\CPQBttn.sys -- (HBtnKey)
DRV - [2006/01/10 00:00:04 | 000,022,016 | ---- | M] (Hewlett-Packard Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Accelerometer.sys -- (Accelerometer)
DRV - [2006/01/10 00:00:04 | 000,017,920 | ---- | M] (Hewlett-Packard Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\hpdskflt.sys -- (hpdskflt)
DRV - [2005/11/29 15:56:28 | 000,036,768 | ---- | M] (Infineon Technologies AG) [Kernel | System] -- C:\WINDOWS\System32\drivers\psd.sys -- (PersonalSecureDrive)
DRV - [2005/10/21 10:19:34 | 000,036,352 | ---- | M] (Infineon Technologies AG) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ifxtpm.sys -- (IFXTPM)
DRV - [2001/08/17 11:10:28 | 000,035,913 | ---- | M] (SMC) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\smcirda.sys -- (SMCIRDA)
========== Standard Registry (SafeList) ==========
[attachment=3837]
amandamcpherson said:OTL logfile created on: 3/2/2013 11:14:49 PM - Run
OTLPE by OldTimer - Version 3.1.48.0 Folder = X:\Programs\OTLPE
Microsoft Windows XP Service Pack 3 (Version = 5.1.2600) - Type = SYSTEM
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
3.00 Gb Total Physical Memory | 3.00 Gb Available Physical Memory | 92.00% Memory free
3.00 Gb Paging File | 3.00 Gb Available in Paging File | 98.00% Paging File free
Paging file location(s): C:\pagefile.sys 2046 4092 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 149.05 Gb Total Space | 113.24 Gb Free Space | 75.98% Space Free | Partition Type: NTFS
Drive X: | 284.12 Mb Total Space | 0.00 Mb Free Space | 0.00% Space Free | Partition Type: CDFS
Computer Name: REATOGO | User Name: SYSTEM
Boot Mode: Normal | Scan Mode: All users
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days
Using ControlSet: ControlSet003
========== Win32 Services (SafeList) ==========
SRV - File not found [Disabled] -- -- (HidServ)
SRV - [2013/03/02 20:36:26 | 000,106,280 | ---- | M] (SurfRight B.V.) [Auto] -- C:\Program Files\HitmanPro\hmpsched.exe -- (HitmanProScheduler)
SRV - [2013/02/20 07:38:08 | 000,093,984 | ---- | M] (Conduit) [Auto] -- C:\Program Files\SearchProtect\bin\CltMngSvc.exe -- (CltMngSvc)
SRV - [2013/02/05 16:09:05 | 000,651,720 | ---- | M] (Macrovision Europe Ltd.) [On_Demand] -- C:\Program Files\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe -- (FLEXnet Licensing Service)
SRV - [2012/12/13 12:01:56 | 000,159,640 | ---- | M] (McAfee, Inc.) [Auto] -- C:\WINDOWS\System32\mfevtps.exe -- (mfevtp)
SRV - [2012/12/13 12:01:54 | 000,167,344 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\Common Files\McAfee\SystemCore\mcshield.exe -- (McShield)
SRV - [2012/08/21 16:06:00 | 000,132,712 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\Common Framework\FrameworkService.exe -- (McAfeeFramework)
SRV - [2012/07/03 17:14:52 | 000,163,200 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\Common Files\McAfee\SystemCore\mfefire.exe -- (mfefire)
SRV - [2012/07/03 17:14:50 | 000,489,120 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\Host Intrusion Prevention\FireSvc.exe -- (enterceptAgent)
SRV - [2011/12/02 11:55:28 | 000,161,664 | ---- | M] (Oracle Corporation) [Auto] -- C:\Program Files\Java\jre7\bin\jqs.exe -- (JavaQuickStarterService)
SRV - [2011/09/14 20:08:00 | 000,209,760 | ---- | M] (McAfee, Inc.) [Auto] -- C:\Program Files\McAfee\VirusScan Enterprise\vstskmgr.exe -- (McTaskManager)
SRV - [2011/09/09 13:17:30 | 000,245,760 | ---- | M] (Avaya Inc.) [Auto] -- C:\Program Files\Avaya\Avaya one-X Communicator\QosServM.exe -- (iClarityQoSService)
SRV - [2009/09/18 03:00:00 | 000,764,768 | ---- | M] (Microsoft Corporation) [Auto] -- C:\WINDOWS\system32\CCM\CcmExec.exe -- (CcmExec)
SRV - [2009/09/18 03:00:00 | 000,246,624 | ---- | M] (Microsoft Corporation) [On_Demand] -- C:\WINDOWS\System32\CCM\TSManager.exe -- (smstsmgr)
========== Driver Services (SafeList) ==========
DRV - File not found [Kernel | On_Demand] -- -- (WDICA)
DRV - File not found [Kernel | On_Demand] -- -- (PDRFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDRELI)
DRV - File not found [Kernel | On_Demand] -- -- (PDFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDCOMP)
DRV - File not found [Kernel | System] -- -- (PCIDump)
DRV - File not found [Kernel | On_Demand] -- -- (mfeavfk01)
DRV - File not found [Kernel | System] -- -- (lbrtfdc)
DRV - File not found [Kernel | System] -- -- (Changer)
DRV - [2013/01/31 03:19:50 | 000,181,344 | ---- | M] (DEVGURU Co., LTD.(www.devguru.co.kr)) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ssudmdm.sys -- (ssudmdm) SAMSUNG Mobile USB Modem Drivers (DEVGURU Ver.)
DRV - [2013/01/31 03:19:50 | 000,083,168 | ---- | M] (DEVGURU Co., LTD.(www.devguru.co.kr)) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ssudbus.sys -- (dg_ssudbus) SAMSUNG Mobile USB Composite Device Driver (DEVGURU Ver.)
DRV - [2012/12/13 12:01:56 | 000,090,368 | ---- | M] (McAfee, Inc.) [Kernel | System] -- C:\WINDOWS\system32\drivers\mfetdi2k.sys -- (mfetdi2k)
DRV - [2012/12/13 12:01:56 | 000,087,816 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mferkdet.sys -- (mferkdet)
DRV - [2012/12/13 12:01:55 | 000,477,584 | ---- | M] (McAfee, Inc.) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\mfehidk.sys -- (mfehidk)
DRV - [2012/12/13 12:01:55 | 000,215,024 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfeavfk.sys -- (mfeavfk)
DRV - [2012/12/13 12:01:55 | 000,121,544 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfeapfk.sys -- (mfeapfk)
DRV - [2012/12/13 12:01:55 | 000,059,616 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfebopk.sys -- (mfebopk)
DRV - [2012/07/03 17:14:52 | 000,348,880 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfefirek.sys -- (mfefirek)
DRV - [2012/07/03 17:14:52 | 000,083,920 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfendisk.sys -- (mfendiskmp)
DRV - [2012/07/03 17:14:52 | 000,083,920 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\mfendisk.sys -- (mfendisk)
DRV - [2012/07/03 17:14:50 | 000,147,248 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\HipShieldK.sys -- (HipShieldK)
DRV - [2012/07/03 17:14:50 | 000,042,016 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\FireNfcp.sys -- (FireNfcp)
DRV - [2010/09/21 14:13:40 | 000,156,160 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\b57xp32.sys -- (b57w2k)
DRV - [2009/09/18 03:00:00 | 000,020,848 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\CCM\PrepDrv.sys -- (prepdrvr)
DRV - [2009/08/21 18:24:26 | 000,040,320 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\nmnt.sys -- (nm)
DRV - [2008/10/20 19:08:06 | 000,012,448 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\smsmdm.sys -- (smsmdd)
DRV - [2008/05/06 16:06:00 | 000,011,520 | ---- | M] (Western Digital Technologies) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\wdcsam.sys -- (WDC_SAM)
DRV - [2007/12/14 08:21:56 | 000,290,816 | ---- | M] (Texas Instruments) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\tifm21.sys -- (tifm21)
DRV - [2007/10/31 09:23:20 | 002,236,544 | ---- | M] (Intel Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\NETw4x32.sys -- (NETw4x32) Intel(R)
DRV - [2007/08/28 14:47:36 | 000,146,560 | ---- | M] (AuthenTec, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\atswpdrv.sys -- (ATSWPDRV) AuthenTec TruePrint USB Driver (SwipeSensor)
DRV - [2007/06/18 15:12:04 | 000,016,768 | ---- | M] (Hewlett-Packard Development Company, L.P.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\HpqKbFiltr.sys -- (HpqKbFiltr)
DRV - [2007/05/09 12:27:00 | 000,097,280 | ---- | M] (Texas Instruments) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\gtipci21.sys -- (GTIPCI21)
DRV - [2007/02/01 08:29:52 | 000,024,304 | ---- | M] (PCTEL Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\PCTINDIS5.sys -- (PCTINDIS5)
DRV - [2006/08/28 13:40:48 | 001,160,320 | ---- | M] (Agere Systems) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\AGRSM.sys -- (AgereSoftModem)
DRV - [2006/08/18 12:18:08 | 000,009,400 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLADResM.SYS -- (DLADResM)
DRV - [2006/08/18 12:17:46 | 000,035,096 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLABMFSM.SYS -- (DLABMFSM)
DRV - [2006/08/18 12:17:44 | 000,097,848 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAUDF_M.SYS -- (DLAUDF_M)
DRV - [2006/08/18 12:17:44 | 000,094,648 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAUDFAM.SYS -- (DLAUDFAM)
DRV - [2006/08/18 12:17:42 | 000,026,008 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAOPIOM.SYS -- (DLAOPIOM)
DRV - [2006/08/18 12:17:40 | 000,032,472 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLABOIOM.SYS -- (DLABOIOM)
DRV - [2006/08/18 12:17:38 | 000,104,472 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAIFS_M.SYS -- (DLAIFS_M)
DRV - [2006/08/18 12:17:38 | 000,014,520 | ---- | M] (Roxio) [File_System | Auto] -- C:\WINDOWS\system32\DLA\DLAPoolM.SYS -- (DLAPoolM)
DRV - [2006/08/11 09:35:18 | 000,012,920 | ---- | M] (Roxio) [File_System | System] -- C:\WINDOWS\system32\drivers\DLACDBHM.SYS -- (DLACDBHM)
DRV - [2006/08/11 09:35:16 | 000,028,184 | ---- | M] (Roxio) [File_System | System] -- C:\WINDOWS\system32\drivers\DLARTL_M.SYS -- (DLARTL_M)
DRV - [2006/06/28 08:54:00 | 000,009,472 | ---- | M] (Hewlett-Packard Development Company, L.P.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\CPQBttn.sys -- (HBtnKey)
DRV - [2006/01/10 00:00:04 | 000,022,016 | ---- | M] (Hewlett-Packard Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Accelerometer.sys -- (Accelerometer)
DRV - [2006/01/10 00:00:04 | 000,017,920 | ---- | M] (Hewlett-Packard Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\hpdskflt.sys -- (hpdskflt)
DRV - [2005/11/29 15:56:28 | 000,036,768 | ---- | M] (Infineon Technologies AG) [Kernel | System] -- C:\WINDOWS\System32\drivers\psd.sys -- (PersonalSecureDrive)
DRV - [2005/10/21 10:19:34 | 000,036,352 | ---- | M] (Infineon Technologies AG) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\ifxtpm.sys -- (IFXTPM)
DRV - [2001/08/17 11:10:28 | 000,035,913 | ---- | M] (SMC) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\smcirda.sys -- (SMCIRDA)
========== Standard Registry (SafeList) ==========
Attachments
Open OTLPE again but this time, under custom scan/fixes, copy and paste the following:
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
:OTL
O20 - AppInit_DLLs: (c:\progra~1\browse~1\sprote~1.dll) - C:\Program Files\BrowseToSave\sprotector.dll ()
[2013/03/02 10:59:31 | 000,177,284 | ---- | C] (Lurcom Ltd) -- C:\Documents and Settings\5678118.exe
[2013/03/02 22:25:48 | 000,003,634 | ---- | M] () -- C:\WINDOWS\ooezph.zus
[2013/03/02 22:12:18 | 000,017,808 | ---- | M] () -- C:\WINDOWS\xrjaun.dgf
[2013/03/02 21:29:19 | 000,083,643 | ---- | M] () -- C:\WINDOWS\vnpuif.qtl
[2013/03/02 11:02:10 | 000,093,635 | ---- | M] () -- C:\WINDOWS\pubfqb.wpk
[2013/03/02 11:02:03 | 000,177,665 | ---- | M] () -- C:\WINDOWS\jlayf.qsx
[2013/03/02 11:01:21 | 000,245,744 | ---- | M] () -- C:\WINDOWS\vjrz.lfd
:Files
C:\Documents and Settings\xx\5678118.exe
ipconfig /flushdns /c
:Commands
[EMPTYTEMP]
[RESETHOSTS]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
where the file go? what's the file name? I saw the message file deleted success and close the window.
reboot the PC from my computer in normal mode look fine but once I connected to the internet that window come up right away.
The virus window popped up again? Don't connect your PC to the internet for now, your PC is still infected.
Are you able to run programs in normal mode? If so, download and transfer the programs below to your infected PC.
Please download AdwCleaner by Xplode onto your desktop.
Download & SAVE to your Desktop RogueKiller or from here
Are you able to run programs in normal mode? If so, download and transfer the programs below to your infected PC.
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
# AdwCleaner v2.113 - Logfile created 03/03/2013 at 00:52:16
# Updated 23/02/2013 by Xplode
# Operating system : Microsoft Windows XP Service Pack 3 (32 bits)
# User : xx - xx
# Boot Mode : Normal
# Running from : F:\AdwCleaner.exe
# Option [Delete]
***** [Services] *****
Stopped & Deleted : CltMngSvc
***** [Files / Folders] *****
File Deleted : C:\END
File Deleted : C:\WINDOWS\Tasks\AmiUpdXp.job
Folder Deleted : C:\Documents and Settings\All Users\Application Data\InstallMate
Folder Deleted : C:\Documents and Settings\xx\Application Data\PriceGong
Folder Deleted : C:\Documents and Settings\xx\Application Data\SearchProtect
Folder Deleted : C:\Documents and Settings\xx\Application Data\SwvUpdater
Folder Deleted : C:\Documents and Settings\xx\Local Settings\Application Data\Conduit
Folder Deleted : C:\Documents and Settings\xx\Local Settings\Application Data\WhiteSmoke_B
Folder Deleted : C:\Program Files\Conduit
Folder Deleted : C:\Program Files\SearchProtect
Folder Deleted : C:\Program Files\WhiteSmoke_B
***** [Registry] *****
Key Deleted : HKCU\Software\AppDataLow\SProtector
Key Deleted : HKCU\Software\Conduit
Key Deleted : HKCU\Software\ConduitSearchScopes
Key Deleted : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{AFDBDDAA-5D3F-42EE-B79C-185A7020515B}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Settings\{F0E59437-6148-4A98-B0A6-60D557EF57F4}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{97A5591D-4C09-4E06-9228-AC433B73650C}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{F0E59437-6148-4A98-B0A6-60D557EF57F4}
Key Deleted : HKCU\Software\PriceGong
Key Deleted : HKCU\Software\SearchProtect
Key Deleted : HKCU\Software\SmartBar
Key Deleted : HKCU\Software\WhiteSmoke_B
Key Deleted : HKCU\Toolbar
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{3C471948-F874-49F5-B338-4F214A2EE0B1}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{66EEF543-A9AC-4A9D-AA3C-1ED148AC8EEE}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{67BD9EEB-AA06-4329-A940-D250019300C9}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{826D7151-8D99-434B-8540-082B8C2AE556}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{97A5591D-4C09-4E06-9228-AC433B73650C}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{F0E59437-6148-4A98-B0A6-60D557EF57F4}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{66EEF543-A9AC-4A9D-AA3C-1ED148AC8EEE}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{9EDC0C90-2B5B-4512-953E-35767BAD5C67}
Key Deleted : HKLM\SOFTWARE\Classes\Toolbar.CT3279141
Key Deleted : HKLM\SOFTWARE\Classes\TypeLib\{11549FE4-7C5A-4C17-9FC3-56FC5162A994}
Key Deleted : HKLM\SOFTWARE\Classes\TypeLib\{A0EE0278-2986-4E5A-884E-A3BF0357E476}
Key Deleted : HKLM\SOFTWARE\Classes\TypeLib\{E2343056-CC08-46AC-B898-BFC7ACF4E755}
Key Deleted : HKLM\SOFTWARE\Classes\Updater.AmiUpd
Key Deleted : HKLM\SOFTWARE\Classes\Updater.AmiUpd.1
Key Deleted : HKLM\Software\Conduit
Key Deleted : HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{979CFC01-1AF2-4DEF-81E8-4240BD8BD460}
Key Deleted : HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{B0CBF600-1281-42E6-B7D2-F29DCDDAD4D1}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Management\ARPCache\{99C91FC5-DB5B-4AA0-BB70-5D89C5A4DF96}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Management\ARPCache\SearchProtect
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Management\ARPCache\WhiteSmoke_B Toolbar
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{F0E59437-6148-4A98-B0A6-60D557EF57F4}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\{97A5591D-4C09-4E06-9228-AC433B73650C}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{99C91FC5-DB5B-4AA0-BB70-5D89C5A4DF96}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SearchProtect
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WhiteSmoke_B Toolbar
Key Deleted : HKLM\Software\SearchProtect
Key Deleted : HKLM\Software\SP Global
Key Deleted : HKLM\Software\SProtector
Key Deleted : HKLM\Software\WhiteSmoke_B
Value Deleted : HKCU\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser [{F0E59437-6148-4A98-B0A6-60D557EF57F4}]
Value Deleted : HKCU\Software\Microsoft\Internet Explorer\URLSearchHooks [{F0E59437-6148-4A98-B0A6-60D557EF57F4}]
Value Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Run [searchprotect]
Value Deleted : HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel [Homepage]
Value Deleted : HKLM\SOFTWARE\Microsoft\Internet Explorer\Toolbar [{F0E59437-6148-4A98-B0A6-60D557EF57F4}]
Value Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run [SearchProtectAll]
***** [Internet Browsers] *****
-\\ Internet Explorer v8.0.6001.18702
[OK] Registry is clean.
-\\ Google Chrome v [Unable to get version]
File : C:\Documents and Settings\xx\Local Settings\Application Data\Google\Chrome\User Data\Default\Preferences
[OK] File is clean.
*************************
AdwCleaner[R1].txt - [5379 octets] - [03/03/2013 00:51:24]
AdwCleaner[S1].txt - [5284 octets] - [03/03/2013 00:52:16]
########## EOF - C:\AdwCleaner[S1].txt - [5344 octets] ##########
# Updated 23/02/2013 by Xplode
# Operating system : Microsoft Windows XP Service Pack 3 (32 bits)
# User : xx - xx
# Boot Mode : Normal
# Running from : F:\AdwCleaner.exe
# Option [Delete]
***** [Services] *****
Stopped & Deleted : CltMngSvc
***** [Files / Folders] *****
File Deleted : C:\END
File Deleted : C:\WINDOWS\Tasks\AmiUpdXp.job
Folder Deleted : C:\Documents and Settings\All Users\Application Data\InstallMate
Folder Deleted : C:\Documents and Settings\xx\Application Data\PriceGong
Folder Deleted : C:\Documents and Settings\xx\Application Data\SearchProtect
Folder Deleted : C:\Documents and Settings\xx\Application Data\SwvUpdater
Folder Deleted : C:\Documents and Settings\xx\Local Settings\Application Data\Conduit
Folder Deleted : C:\Documents and Settings\xx\Local Settings\Application Data\WhiteSmoke_B
Folder Deleted : C:\Program Files\Conduit
Folder Deleted : C:\Program Files\SearchProtect
Folder Deleted : C:\Program Files\WhiteSmoke_B
***** [Registry] *****
Key Deleted : HKCU\Software\AppDataLow\SProtector
Key Deleted : HKCU\Software\Conduit
Key Deleted : HKCU\Software\ConduitSearchScopes
Key Deleted : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{AFDBDDAA-5D3F-42EE-B79C-185A7020515B}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Settings\{F0E59437-6148-4A98-B0A6-60D557EF57F4}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{97A5591D-4C09-4E06-9228-AC433B73650C}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{F0E59437-6148-4A98-B0A6-60D557EF57F4}
Key Deleted : HKCU\Software\PriceGong
Key Deleted : HKCU\Software\SearchProtect
Key Deleted : HKCU\Software\SmartBar
Key Deleted : HKCU\Software\WhiteSmoke_B
Key Deleted : HKCU\Toolbar
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{3C471948-F874-49F5-B338-4F214A2EE0B1}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{66EEF543-A9AC-4A9D-AA3C-1ED148AC8EEE}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{67BD9EEB-AA06-4329-A940-D250019300C9}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{826D7151-8D99-434B-8540-082B8C2AE556}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{97A5591D-4C09-4E06-9228-AC433B73650C}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{F0E59437-6148-4A98-B0A6-60D557EF57F4}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{66EEF543-A9AC-4A9D-AA3C-1ED148AC8EEE}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{9EDC0C90-2B5B-4512-953E-35767BAD5C67}
Key Deleted : HKLM\SOFTWARE\Classes\Toolbar.CT3279141
Key Deleted : HKLM\SOFTWARE\Classes\TypeLib\{11549FE4-7C5A-4C17-9FC3-56FC5162A994}
Key Deleted : HKLM\SOFTWARE\Classes\TypeLib\{A0EE0278-2986-4E5A-884E-A3BF0357E476}
Key Deleted : HKLM\SOFTWARE\Classes\TypeLib\{E2343056-CC08-46AC-B898-BFC7ACF4E755}
Key Deleted : HKLM\SOFTWARE\Classes\Updater.AmiUpd
Key Deleted : HKLM\SOFTWARE\Classes\Updater.AmiUpd.1
Key Deleted : HKLM\Software\Conduit
Key Deleted : HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{979CFC01-1AF2-4DEF-81E8-4240BD8BD460}
Key Deleted : HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{B0CBF600-1281-42E6-B7D2-F29DCDDAD4D1}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Management\ARPCache\{99C91FC5-DB5B-4AA0-BB70-5D89C5A4DF96}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Management\ARPCache\SearchProtect
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Management\ARPCache\WhiteSmoke_B Toolbar
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{F0E59437-6148-4A98-B0A6-60D557EF57F4}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\{97A5591D-4C09-4E06-9228-AC433B73650C}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{99C91FC5-DB5B-4AA0-BB70-5D89C5A4DF96}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SearchProtect
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WhiteSmoke_B Toolbar
Key Deleted : HKLM\Software\SearchProtect
Key Deleted : HKLM\Software\SP Global
Key Deleted : HKLM\Software\SProtector
Key Deleted : HKLM\Software\WhiteSmoke_B
Value Deleted : HKCU\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser [{F0E59437-6148-4A98-B0A6-60D557EF57F4}]
Value Deleted : HKCU\Software\Microsoft\Internet Explorer\URLSearchHooks [{F0E59437-6148-4A98-B0A6-60D557EF57F4}]
Value Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Run [searchprotect]
Value Deleted : HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel [Homepage]
Value Deleted : HKLM\SOFTWARE\Microsoft\Internet Explorer\Toolbar [{F0E59437-6148-4A98-B0A6-60D557EF57F4}]
Value Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run [SearchProtectAll]
***** [Internet Browsers] *****
-\\ Internet Explorer v8.0.6001.18702
[OK] Registry is clean.
-\\ Google Chrome v [Unable to get version]
File : C:\Documents and Settings\xx\Local Settings\Application Data\Google\Chrome\User Data\Default\Preferences
[OK] File is clean.
*************************
AdwCleaner[R1].txt - [5379 octets] - [03/03/2013 00:51:24]
AdwCleaner[S1].txt - [5284 octets] - [03/03/2013 00:52:16]
########## EOF - C:\AdwCleaner[S1].txt - [5344 octets] ##########
RogueKiller V8.5.2 [Feb 23 2013] by Tigzy
mail : tigzyRK<at>gmail<dot>com
Feedback : http://www.geekstogo.com/forum/files/file/413-roguekiller/
Website : http://tigzy.geekstogo.com/roguekiller.php
Blog : http://tigzyrk.blogspot.com/
Operating System : Windows XP (5.1.2600 Service Pack 3) 32 bits version
Started in : Normal mode
User : xx [Admin rights]
Mode : Remove -- Date : 03/03/2013 01:00:14
| ARK || FAK || MBR |
¤¤¤ Bad processes : 0 ¤¤¤
¤¤¤ Registry Entries : 6 ¤¤¤
[HJPOL] HKLM\[...]\System : DisableTaskMgr (0) -> DELETED
[HJPOL] HKLM\[...]\System : DisableRegistryTools (0) -> DELETED
[HJ] HKLM\[...]\SystemRestore : DisableSR (1) -> REPLACED (0)
[HJ] HKLM\[...]\Security Center : FirewallDisableNotify (1) -> REPLACED (0)
[HJ] HKLM\[...]\Security Center : UpdatesDisableNotify (1) -> REPLACED (0)
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver : [LOADED] ¤¤¤
_INLINE_ : NtAllocateVirtualMemory -> HOOKED (\??\C:\WINDOWS\system32\drivers\hitmanpro37.sys @ 0xA7CF8566)
¤¤¤ HOSTS File: ¤¤¤
--> C:\WINDOWS\system32\drivers\etc\hosts
ÿþ1
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: ST9160310AS +++++
--- User ---
[MBR] f4f27e28aca2815c3bc2f7b37802b1e4
[BSP] 76ce7946793d0e78ee67a4bc4009902d : Windows 7/8 MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 2048 | Size: 152625 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[2]_D_03032013_02d0100.txt >>
RKreport[1]_S_03032013_02d0059.txt ; RKreport[2]_D_03032013_02d0100.txt
mail : tigzyRK<at>gmail<dot>com
Feedback : http://www.geekstogo.com/forum/files/file/413-roguekiller/
Website : http://tigzy.geekstogo.com/roguekiller.php
Blog : http://tigzyrk.blogspot.com/
Operating System : Windows XP (5.1.2600 Service Pack 3) 32 bits version
Started in : Normal mode
User : xx [Admin rights]
Mode : Remove -- Date : 03/03/2013 01:00:14
| ARK || FAK || MBR |
¤¤¤ Bad processes : 0 ¤¤¤
¤¤¤ Registry Entries : 6 ¤¤¤
[HJPOL] HKLM\[...]\System : DisableTaskMgr (0) -> DELETED
[HJPOL] HKLM\[...]\System : DisableRegistryTools (0) -> DELETED
[HJ] HKLM\[...]\SystemRestore : DisableSR (1) -> REPLACED (0)
[HJ] HKLM\[...]\Security Center : FirewallDisableNotify (1) -> REPLACED (0)
[HJ] HKLM\[...]\Security Center : UpdatesDisableNotify (1) -> REPLACED (0)
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver : [LOADED] ¤¤¤
_INLINE_ : NtAllocateVirtualMemory -> HOOKED (\??\C:\WINDOWS\system32\drivers\hitmanpro37.sys @ 0xA7CF8566)
¤¤¤ HOSTS File: ¤¤¤
--> C:\WINDOWS\system32\drivers\etc\hosts
ÿþ1
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: ST9160310AS +++++
--- User ---
[MBR] f4f27e28aca2815c3bc2f7b37802b1e4
[BSP] 76ce7946793d0e78ee67a4bc4009902d : Windows 7/8 MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 2048 | Size: 152625 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[2]_D_03032013_02d0100.txt >>
RKreport[1]_S_03032013_02d0059.txt ; RKreport[2]_D_03032013_02d0100.txt
Run TDSSkiller and Junkware removal tool first before connecting to the internet. Afterwards, connect to the internet so you can update Malwarebytes and download OTL. Please attach all the logs that are produced since they are extremely long and can't fit in one post. Let me know how your PC is running after the 4 scans below.
Download TDSSkiller from here
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Please download Junkware Removal Tool to your desktop from here
Please download Malwarebytes' Anti-Malware from here to your desktop.
Download OTL by Old Timer from here and save it to your Desktop.
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.
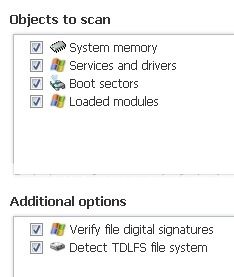
- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Please download Junkware Removal Tool to your desktop from here
- Turn off your antivirus software now to avoid potential conflicts
- Double-click to run the tool. For Windows Vista or 7 users, right-click the file and select Run as Administrator
- The tool will open and start scanning your system
- Please be patient as this can take a while to complete depending on your system's specifications
- On completion, a log (JRT.txt) will be saved to your desktop and will automatically open
- Post the contents of JRT.txt into your next reply
Please download Malwarebytes' Anti-Malware from here to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to
- Update Malwarebytes' Anti-Malware
- and Launch Malwarebytes' Anti-Malware
- then click Finish.
- If an update is found, it will download and install the latest version.
- When it prompts you to try their 30-day trail, click decline
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is Checked (ticked) except items in the C:\System Volume Information folder and click on Remove Selected.
- When completed, a log will open in Notepad. please copy and paste the log into your next reply
- If you accidently close it, the log file is saved here and will be named like this:
- C:\Documents and Settings\Username\Application Data\Malwarebytes\Malwarebytes' Anti-Malware\Logs\mbam-log-date (time).txt
Download OTL by Old Timer from here and save it to your Desktop.
- Double click on OTL.exe to run it.
- Click the Scan All Users checkbox.
- Check the boxes beside LOP Check and Purity Check
- Click on Run Scan at the top left hand corner.
- When done, two Notepad files will open.
- OTL.txt <-- Will be opened
- Extra.txt <-- Will be minimized
- Please attach the contents of these 2 Notepad files in your next reply.
TDSSkiller , OTL logs attached.
JRT log:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Junkware Removal Tool (JRT) by Thisisu
Version: 4.6.6 (02.27.2013:1)
OS: Microsoft Windows XP x86
Ran by xx on Sun 03/03/2013 at 10:33:42.73
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
~~~ Services
~~~ Registry Values
Successfully repaired: [Registry Value] hkey_local_machine\software\microsoft\internet explorer\searchscopes\{0633ee93-d776-472f-a0ff-e1416b8b2e3a}\\DisplayName
Successfully repaired: [Registry Value] hkey_local_machine\software\microsoft\internet explorer\searchscopes\{0633ee93-d776-472f-a0ff-e1416b8b2e3a}\\URL
~~~ Registry Keys
Successfully deleted: [Registry Key] hkey_current_user\software\microsoft\internet explorer\searchscopes\{6a1806cd-94d4-4689-ba73-e35ea1ea9990}
~~~ Files
~~~ Folders
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Scan was completed on Sun 03/03/2013 at 10:41:06.75
End of JRT log
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Malwarebytes log:
Malwarebytes Anti-Malware (Trial) 1.70.0.1100
www.malwarebytes.org
Database version: v2013.03.03.07
Windows XP Service Pack 3 x86 NTFS
Internet Explorer 8.0.6001.18702
xx :: xx [administrator]
Protection: Enabled
3/3/2013 10:49:30 AM
mbam-log-2013-03-03 (10-49-30).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 267512
Time elapsed: 7 minute(s), 38 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 1
HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon|shell (Hijack.Shell.Gen) -> Data: C:\Documents and Settings\xx\Application Data\ldr.mcb,explorer.exe -> Quarantined and deleted successfully.
Registry Data Items Detected: 1
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|StartMenuLogoff (PUM.Hijack.StartMenu) -> Bad: (1) Good: (0) -> Quarantined and repaired successfully.
Folders Detected: 0
(No malicious items detected)
Files Detected: 2
C:\RECYCLER\S-1-5-18\Dc1.exe (Trojan.Medfos) -> Quarantined and deleted successfully.
C:\RECYCLER\S-1-5-21-790525478-1343024091-1801674531-414923\Dc2.exe (PUP.Offerware) -> Quarantined and deleted successfully.
(end)
Am I all look good now?
JRT log:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Junkware Removal Tool (JRT) by Thisisu
Version: 4.6.6 (02.27.2013:1)
OS: Microsoft Windows XP x86
Ran by xx on Sun 03/03/2013 at 10:33:42.73
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
~~~ Services
~~~ Registry Values
Successfully repaired: [Registry Value] hkey_local_machine\software\microsoft\internet explorer\searchscopes\{0633ee93-d776-472f-a0ff-e1416b8b2e3a}\\DisplayName
Successfully repaired: [Registry Value] hkey_local_machine\software\microsoft\internet explorer\searchscopes\{0633ee93-d776-472f-a0ff-e1416b8b2e3a}\\URL
~~~ Registry Keys
Successfully deleted: [Registry Key] hkey_current_user\software\microsoft\internet explorer\searchscopes\{6a1806cd-94d4-4689-ba73-e35ea1ea9990}
~~~ Files
~~~ Folders
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Scan was completed on Sun 03/03/2013 at 10:41:06.75
End of JRT log
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Malwarebytes log:
Malwarebytes Anti-Malware (Trial) 1.70.0.1100
www.malwarebytes.org
Database version: v2013.03.03.07
Windows XP Service Pack 3 x86 NTFS
Internet Explorer 8.0.6001.18702
xx :: xx [administrator]
Protection: Enabled
3/3/2013 10:49:30 AM
mbam-log-2013-03-03 (10-49-30).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 267512
Time elapsed: 7 minute(s), 38 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 1
HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon|shell (Hijack.Shell.Gen) -> Data: C:\Documents and Settings\xx\Application Data\ldr.mcb,explorer.exe -> Quarantined and deleted successfully.
Registry Data Items Detected: 1
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|StartMenuLogoff (PUM.Hijack.StartMenu) -> Bad: (1) Good: (0) -> Quarantined and repaired successfully.
Folders Detected: 0
(No malicious items detected)
Files Detected: 2
C:\RECYCLER\S-1-5-18\Dc1.exe (Trojan.Medfos) -> Quarantined and deleted successfully.
C:\RECYCLER\S-1-5-21-790525478-1343024091-1801674531-414923\Dc2.exe (PUP.Offerware) -> Quarantined and deleted successfully.
(end)
Am I all look good now?
Attachments
Not quite.. there are still some malware left.
Re-run TDSSKiller and for this entry:
10:31:32.0890 2476 \Device\Harddisk1\DR2 ( Rootkit.Win32.BackBoot.gen ) - skipped by user
Select Delete. The rest you can skip like you did before. Then,
Open OTL. Under custom scan/fixes, copy and paste the following:
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Run Eset NOD32 Online AntiVirus
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
Re-run TDSSKiller and for this entry:
10:31:32.0890 2476 \Device\Harddisk1\DR2 ( Rootkit.Win32.BackBoot.gen ) - skipped by user
Select Delete. The rest you can skip like you did before. Then,
Open OTL. Under custom scan/fixes, copy and paste the following:
:Files
C:\WINDOWS\ppmmc.lea
C:\WINDOWS\System32\name.exe
:Commands
[reboot]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Run Eset NOD32 Online AntiVirus
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
- Tick the box next to YES, I accept the Terms of Use.
- Click Start
- When asked, allow the activex control to install
- Disable your current antivirus software. You can usually do this with its Notfication Tray icon near the clock.
- Click Start
- Make sure that the option "Remove found threats" is Un-checked, and the following Advance Settings are Checked
- Scan unwanted applications
- Scan for potentially unsafe applications
- Enable Anti-Stealth Technology
- Click Scan
- Wait for the scan to finish
- When the scan is done, if it shows a screen that says "Threats found!", then click "List of found threats", and then click "Export to text file..."
- Save that text file on your desktop. Copy and paste the contents of that log in your next reply to this topic.
- The log can also be found in logfile located at C:\Program Files\ESET\Eset Online Scanner\log.txt
10:31:32.0890 2476 \Device\Harddisk1\DR2 ( Rootkit.Win32.BackBoot.gen ) - skipped by user
I couldn't delete this one, I only have skip/copy to quarantine/restore can be selected?
I couldn't delete this one, I only have skip/copy to quarantine/restore can be selected?
no new file generated after OTL reboot, OTL.txt still the old file.
here is the eset scan:
C:\Documents and Settings\All Users\Application Data\Browsee2saave\512d6b4b642b1.dll a variant of Win32/Adware.MultiPlug.I application
C:\Documents and Settings\xx\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\ibghjpbjkjfaphkoimdachhdkobdphfo\1\512d6b4b640780.89073516.js Win32/Adware.MultiPlug.H application
C:\_OTL\MovedFiles\03032013_001934\C_Program Files\BrowseToSave\sprotector.dll a variant of Win32/SProtector.A application
here is the eset scan:
C:\Documents and Settings\All Users\Application Data\Browsee2saave\512d6b4b642b1.dll a variant of Win32/Adware.MultiPlug.I application
C:\Documents and Settings\xx\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\ibghjpbjkjfaphkoimdachhdkobdphfo\1\512d6b4b640780.89073516.js Win32/Adware.MultiPlug.H application
C:\_OTL\MovedFiles\03032013_001934\C_Program Files\BrowseToSave\sprotector.dll a variant of Win32/SProtector.A application
Open OTL. Under custom scan/fixes, copy and paste the following:
Then click Run Fix. Post the log if it generates one.
Update Malwarebytes and do another quick scan.
Download Security Check by screen317 from here or here.
Let me know how your PC is running afterwards.
:OTL
CHR - Extension: Browsee2saave = C:\Documents and Settings\xx\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\ibghjpbjkjfaphkoimdachhdkobdphfo\1\
:Files
C:\Documents and Settings\All Users\Application Data\Browsee2saave
C:\Documents and Settings\xx\Application Data\ldr.mcb
Then click Run Fix. Post the log if it generates one.
Update Malwarebytes and do another quick scan.
Download Security Check by screen317 from here or here.
- Save it to your Desktop.
- Double click SecurityCheck.exe and follow the onscreen instructions inside of the black box.
- A notepad document should open automatically called checkup.txt.
- Please post the contents of that document in your next reply. Please do not attach it!
Let me know how your PC is running afterwards.
You may also like...
-
-
-
Advice Request HELP! My device is locked by ESET Mobile Security
- Started by restwrst
- Replies: 20
-
Advice Request Help: Comodo 2025 - cmdguard.sys - boot fail with newer Nvidia drivers
- Started by Something-x2
- Replies: 33