Thanks to LabZero for making this video review (test).
Please note that this video was made only for testing, SecureMyBit doesn't provide a specific anti-ransomware feature. The test was made with a Cerber Ransomware 3 sample.
Unfortunately LabZero is now guest for personal issues
Thank you for all your efforts!
LabZero tested SecureMyBit against this type of ransomware and that's not sure that SecureMyBit works also against other types of ransomware.
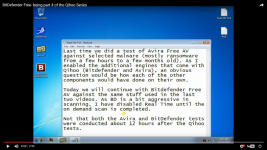
Please note that it seems Cerber 3 doesn't encrypt .txt files. Test executed under VirtualBox (Windows 7 Home x32), and on host system: Windows 10 Pro x64.
Thanks for watching!
Please note that this video was made only for testing, SecureMyBit doesn't provide a specific anti-ransomware feature. The test was made with a Cerber Ransomware 3 sample.
Unfortunately LabZero is now guest for personal issues
Thank you for all your efforts!
LabZero tested SecureMyBit against this type of ransomware and that's not sure that SecureMyBit works also against other types of ransomware.
Please note that it seems Cerber 3 doesn't encrypt .txt files. Test executed under VirtualBox (Windows 7 Home x32), and on host system: Windows 10 Pro x64.
Thanks for watching!