- Oct 23, 2012
- 12,527
Malware analysts from PhishLabs have released a decrypter for a newly spotted ransomware family called Alma Locker.
Discovered by Proofpoint researcher Darien Huss, and first analyzed by Lawrence Abrams, Alma Locker is more advanced than all the other recent ransomware variants released in the past month, who've been more like "testing" versions, and not full-on threats.
As a testament to Alma Locker's more advanced state of development, the crooks behind this malware have already moved to a mass distribution stage using the RIG exploit kit.
It is unknown how crooks are sending hijacked traffic to the RIG exploit kit landing page at the moment. This can be from hacked websites, or from malvertising on legitimate sites.
Alma Locker can be defeated via network activity logs
Alma Locker's features include a strong encryption system that has given researchers headaches for the past few days.
Fortunately, the PhishLabs crew discovered a series of weaknesses in the ransomware's mode of operation, which has allowed them to create a C-Sharp file that can allow victims to recover their files without paying the ransom.
The ransomware uses somewhat of a novel two-phase approach to locking user files. After Alma Locker starts encrypting files, it communicates with its C&C server, to which it sends AES key in cleartext via HTTP.
Discovered by Proofpoint researcher Darien Huss, and first analyzed by Lawrence Abrams, Alma Locker is more advanced than all the other recent ransomware variants released in the past month, who've been more like "testing" versions, and not full-on threats.
As a testament to Alma Locker's more advanced state of development, the crooks behind this malware have already moved to a mass distribution stage using the RIG exploit kit.
It is unknown how crooks are sending hijacked traffic to the RIG exploit kit landing page at the moment. This can be from hacked websites, or from malvertising on legitimate sites.
Alma Locker can be defeated via network activity logs
Alma Locker's features include a strong encryption system that has given researchers headaches for the past few days.
Fortunately, the PhishLabs crew discovered a series of weaknesses in the ransomware's mode of operation, which has allowed them to create a C-Sharp file that can allow victims to recover their files without paying the ransom.
The ransomware uses somewhat of a novel two-phase approach to locking user files. After Alma Locker starts encrypting files, it communicates with its C&C server, to which it sends AES key in cleartext via HTTP.
AES is a symmetric encryption algorithm, meaning the AES key can be used for both encryption and decryption. Unless the user stores network activity logs, the decryption key is unobtainable after the encryption process ends.
Alma Locker authors provide their own decrypter
After the encryption stage ends, the ransomware shows the user a ransom note, with links to a Tor-based website, where he needs to download a decrypter supplied by the crooks.
Unlike other ransomware variants that provide lots of details in the ransom note, Alma Locker only features links to the decrypter and the Tor Browser.
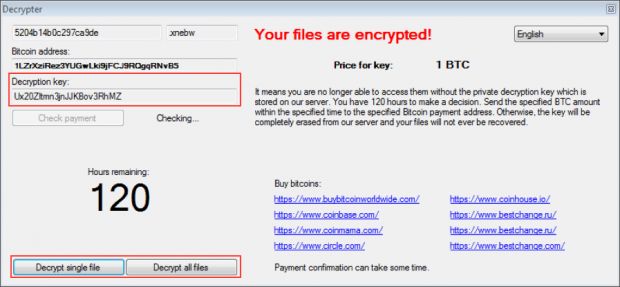
Alma Locker decrypter (provided by crooks)
After the user downloads and starts the Alma Locker decrypter, the user receives more information, such as the Bitcoin address where he needs to pay the ransom, and the total ransom fee, which is only 1 Bitcoin (~$585).
Ransomware can be tricked into unlocking files via MitM attack
PhishLabs experts said they identified weaknesses in this decrypter, which is susceptible to a basic Man-in-the-Middle technique. This allowed them to spoof communications from the crooks' C&C server and gain insight into how their decrypter operates.
This discovery was used to craft a C-Sharp file, which allows users to unlock files for free, if the user manages to discover the encryption/decryption key stored in network logs. A download link is provided on the PhishLabs blog.
"The .CS file is self-containing," King Salemno, PhishLabs malware researcher told Softpedia. "All one needs to do is compile it via a C# compiler and run it. First run will indicate the parameters needed for decryption."
