AMD has fixed, but not yet released BIOS/UEFI/firmware updates for the general public for a security flaw affecting the AMD Secure Processor.
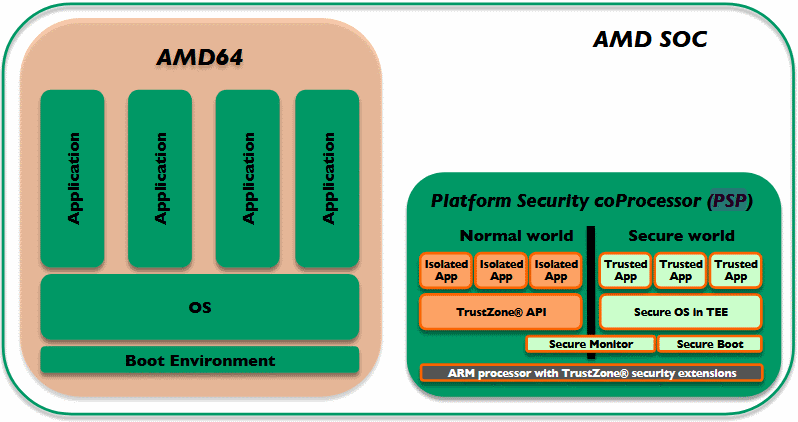
This component, formerly known as AMD PSP (Platform Security Processor), is a chip-on-chip security system, similar to Intel's much-hated Management Engine (ME).
Just like Intel ME, the AMD Secure Processor is an integrated coprocessor that sits next to the real AMD64 x86 CPU cores and runs a separate operating system tasked with handling various security-related operations.
RCE found in AMD PSP TPM module
Cfir Cohen, a security researcher with the Google Cloud Security Team, says he discovered a vulnerability in the Trusted Platform Module (TPM) of the AMD Secure Processor.
The TPM is a component to store critical system data such as passwords, certificates, and encryption keys, in a secure environment and outside of the more easily accessible AMD cores.
"Through manual static analysis, we’ve found a stack-based overflow in the function EkCheckCurrentCert," Cohen says. The researcher claims that an attacker could use specially-crafted EK certificates to get remote code execution rights on the AMD Secure Processor, allowing him to compromise its security.
Cohen said that some basic mitigation techniques such as "stack cookies, NX stack, ASLR" were not implemented in AMD's Secure Processor, making exploitation trivial.
Intel ME uses a similar TPM module, but Cohen did not say if it was affected.
Vulnerability reported to AMD
The Google researcher reported the flaw to AMD in September, and AMD told the researcher in December that they've developed a patch and were preparing to roll it out.
Coincidentally, on Reddit [1, 2], some users reported seeing a new option to disable AMD PSP support, but it's unclear if this new option is related to the patches AMD was preparing to roll out for Cohen's findings.
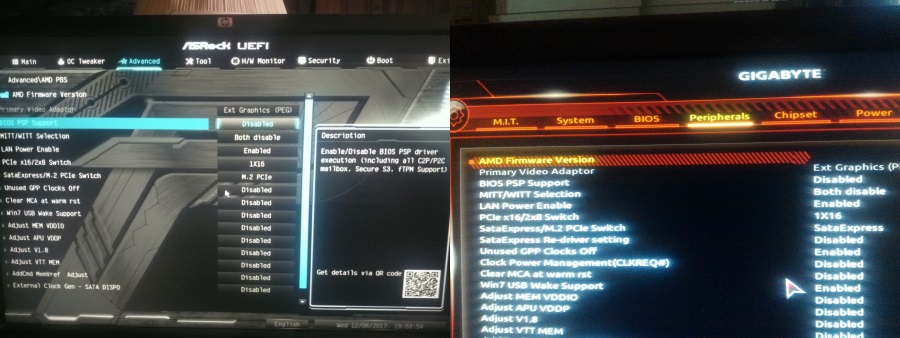
Image credit: repo_code, 1that_guy1
Bleeping Computer has reached out to AMD for more information on these patches, if they're already out, when were they rolled out, and what they consist of.