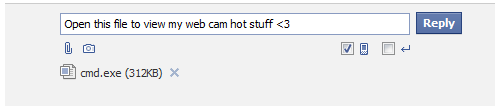
A security researcher has discovered a major security hole affecting the most popular social networking site, Facebook.
Basically, the researcher found a way to upload executable files — such as those most commonly used by malicious software — on the social network site for potential sharing. Needless to say that the potential for abuse by malicious attackers is pretty evident.
More details:
When using the Facebook ‘Messages’ tab, there is a feature to attach a file. Using this feature normally, the site won’t allow a user to attach an executable file. A bug was discovered to subvert this security mechanisms. Note, you do NOT have to be friends with the user to send them a message with an attachment.
Is the ultimate distribution of executable files the cornerstone for distributing malware across the social networking sites? Not at all. Cybercriminals often rely on innocent-looking links that redirect to client-side exploits serving domains for achieving their objectives.
The researcher notified Facebook on 09/30/2011 and received a confirmation of his findings on 10/26/2011.
Facebook’s Security Manager Ryan McGeehan had this to say:
This finding will only allow one user to send an obfuscated renamed file to another Facebook user. The proof of concept, as is, would not execute on a recipients machine without an additional layer of social engineering.Beyond that, we are not going to rely solely on string matching as a protective measure, since zip files and other things could also have unpredictable behaviors when sent as an attachment.
We are AV scanning everything that comes through as a secondary measure, so we have defense in depth for this sort of vector. This puts us at a similar level of protection as most webmail providers who deal with the similar risk, and this finding is a very small part of how we protect against this threat overall.At the end of the day, it is more practical for a bad guy to hide an .exe on a convincing landing page behind a URL shortener, which is something we’ve been dealing with for a while.
via
ZDnet