I said it in a post on another thread, friendly advice. It's not advisable to use your physical machine for malware testing or install everything you see. Do you believe that K will protect you from everything you download, install and access? no AV product is infallible. K is an excellent product, it's among the best security products on the market, even though it's banned in the USA, but that doesn't mean that K is bulletproof, surfing the internet also requires common sense. As soon as I accessed this URL with a .js ending, it was blocked right from the start with the Osprey extension. Besides the fact that I use add-ons like NoScript and uMatrix which block javascript by default in any browser I use, then comes the OSprey extension and then my browser's Secure DNS and then my router's DNS and finally the antivirus on my computer which is my last line of defense. As @harlan4096 mentioned your browser or its cache may be redirecting to this malicious .js URL or even your DNS has been changed without your consent, I suggest you take a look at your router immediately if the DNS is OK when you read this post seriously don't laugh, check there if everything is OK, your PC DNS of your computer may be poisoned. I went to the EaseUS website and everything is OK, nothing unusual and nothing suspicious from what I saw. You may have searched on google for EaseUS or EaseUS Partition Master Free and got a google ad link with a redirect URL, this could also be a hypothesis. Don't play with fire, no my friend @Parkinsond one of the things I learned the most in terms of security was here on MalwareTips, I became more paranoid after I started going to MT, I'm honest, you can call me paranoid I don't care LOL, but there was a good side to all this, I started to think more about the things I use on the internet on a daily basis. I started to have good browsing habits with that pinch of common sense, I started to observe more things when I'm browsing the web by clicking on a Link or accessing a URL. If the website is unknown or obscure, I already go in prepared, aware of the risks, because I'm in unknown lands, I have to be cautious, I'm not even talking about the DeepWeb where the environment becomes more peculiar and hostile if you walk there and don't know what you're doing. Well, that's it, I hope you think about it, remember that you use your computer, even if you say you don't have anything important on it, but remember that you might want to rethink your concepts, about your router, your home network, you could be at risk and you won't realize it until you go to use your cell phone, and start receiving notifications of suspicious activity on your email accounts, social networks and so on.Speaking about "legitimate" websites, K just flagged js in EaseUS Partition Master Free, inspite of being clean on VT.
Serious Discussion Some guy asks if Windows Defender/Microsoft Defender is enough and this is the amazing answer he got back
- Thread starter annaegorov
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
Checked DNS settings of Windows, browser, and modem router; all are just fine.I said it in a post on another thread, friendly advice. It's not advisable to use your physical machine for malware testing or install everything you see. Do you believe that K will protect you from everything you download, install and access? no AV product is infallible. K is an excellent product, it's among the best security products on the market, even though it's banned in the USA, but that doesn't mean that K is bulletproof, surfing the internet also requires common sense. As soon as I accessed this URL with a .js ending, it was blocked right from the start with the Osprey extension. Besides the fact that I use add-ons like NoScript and uMatrix which block javascript by default in any browser I use, then comes the OSprey extension and then my browser's Secure DNS and then my router's DNS and finally the antivirus on my computer which is my last line of defense. As @harlan4096 mentioned your browser or its cache may be redirecting to this malicious .js URL or even your DNS has been changed without your consent, I suggest you take a look at your router immediately if the DNS is OK when you read this post seriously don't laugh, check there if everything is OK, your PC DNS of your computer may be poisoned. I went to the EaseUS website and everything is OK, nothing unusual and nothing suspicious from what I saw. You may have searched on google for EaseUS or EaseUS Partition Master Free and got a google ad link with a redirect URL, this could also be a hypothesis. Don't play with fire, no my friend @Parkinsond one of the things I learned the most in terms of security was here on MalwareTips, I became more paranoid after I started going to MT, I'm honest, you can call me paranoid I don't care LOL, but there was a good side to all this, I started to think more about the things I use on the internet on a daily basis. I started to have good browsing habits with that pinch of common sense, I started to observe more things when I'm browsing the web by clicking on a Link or accessing a URL. If the website is unknown or obscure, I already go in prepared, aware of the risks, because I'm in unknown lands, I have to be cautious, I'm not even talking about the DeepWeb where the environment becomes more peculiar and hostile if you walk there and don't know what you're doing. Well, that's it, I hope you think about it, remember that you use your computer, even if you say you don't have anything important on it, but remember that you might want to rethink your concepts, about your router, your home network, you could be at risk and you won't realize it until you go to use your cell phone, and start receiving notifications of suspicious activity on your email accounts, social networks and so on.
Browser cache was clean before visiting easeus website; Edge is set to empty cache on exit.
I do not receive alerts about unusual acivity; the only incidence is when I created a couple of outlook email accounts, MS suspended them because of unusual activity, but old outlook email account is working just fine.
I do not visit deep web; my testing of malware does not include launching samples, only scan of untouched downloaded samples and to be permanently deleted after.
I am grateful for your sincere advice
Injection of malicious scripts into legitimate websites is not uncommon.I said it in a post on another thread, friendly advice. It's not advisable to use your physical machine for malware testing or install everything you see. Do you believe that K will protect you from everything you download, install and access? no AV product is infallible. K is an excellent product, it's among the best security products on the market, even though it's banned in the USA, but that doesn't mean that K is bulletproof, surfing the internet also requires common sense. As soon as I accessed this URL with a .js ending, it was blocked right from the start with the Osprey extension. Besides the fact that I use add-ons like NoScript and uMatrix which block javascript by default in any browser I use, then comes the OSprey extension and then my browser's Secure DNS and then my router's DNS and finally the antivirus on my computer which is my last line of defense. As @harlan4096 mentioned your browser or its cache may be redirecting to this malicious .js URL or even your DNS has been changed without your consent, I suggest you take a look at your router immediately if the DNS is OK when you read this post seriously don't laugh, check there if everything is OK, your PC DNS of your computer may be poisoned. I went to the EaseUS website and everything is OK, nothing unusual and nothing suspicious from what I saw. You may have searched on google for EaseUS or EaseUS Partition Master Free and got a google ad link with a redirect URL, this could also be a hypothesis. Don't play with fire, no my friend @Parkinsond one of the things I learned the most in terms of security was here on MalwareTips, I became more paranoid after I started going to MT, I'm honest, you can call me paranoid I don't care LOL, but there was a good side to all this, I started to think more about the things I use on the internet on a daily basis. I started to have good browsing habits with that pinch of common sense, I started to observe more things when I'm browsing the web by clicking on a Link or accessing a URL. If the website is unknown or obscure, I already go in prepared, aware of the risks, because I'm in unknown lands, I have to be cautious, I'm not even talking about the DeepWeb where the environment becomes more peculiar and hostile if you walk there and don't know what you're doing. Well, that's it, I hope you think about it, remember that you use your computer, even if you say you don't have anything important on it, but remember that you might want to rethink your concepts, about your router, your home network, you could be at risk and you won't realize it until you go to use your cell phone, and start receiving notifications of suspicious activity on your email accounts, social networks and so on.
I had a similar incidence before with a pharmcy website where K, B, and SEP detected malicious script; K and SEP completely blocked its loading, while B only blocked the script and allowed the page to load.
Persisted for weeks when rechecking, and suddenly, no detection anymore.
I discovered the page was under maintenance and development, and it seems some malicious scripts were injected and removed later when discovered.
That is why you should not exclude any website from scanning or checking, regardless of how trustworthy is the owner.
Here is one more, Norton detecting Github as malicious.
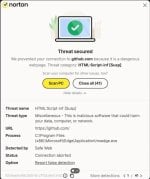
Last edited by a moderator:
Yes, it's true, it's not uncommon, you're right.Injection of malicious scripts into legitimate websites is not uncommon.
Probably hosting the malicious code in Microsoft's Github repositories (ironic) it's not even obfuscated LOL. As you have more than 1 computer, keep K, B and SEP. Symantec's products are also very good. In fact, you don't even need to run a script, or even a malware sample, which if it's already detected just by scanning, let alone run it, it's sure to be blocked.Here is one more, Norton detecting Github as malicious.
I do not run samples as I have no VM; only scan and delete to evaluate pre-exectuion protection.Yes, it's true, it's not uncommon, you're right.
Probably hosting the malicious code in Microsoft's Github repositories (ironic) it's not even obfuscated LOL. As you have more than 1 computer, keep K, B and SEP. Symantec's products are also very good. In fact, you don't even need to run a script, or even a malware sample, which if it's already detected just by scanning, let alone run it, it's sure to be blocked.
Anyway, I am not concerned with testing post-exectution protection (behavioral one) as I consider it is less reliable and any delay undermine its value; the damage already happened, what is the gain of detecting malware after execution?
Yes, that's true. In the future it could be compromised, something injected into the page, whether it's a script or something else that could infect the visitor's machine. We have to be vigilant at all times.That is why you should not exclude any website from scanning or checking, regardless of how trustworthy is the owner.
None of them really, apart from wasting your time. It's more out of curiosity and hobby.gain of detecting malware after execution?
I have scanned after K alarm with Easeus; both K and MD detected nothing.Yes, that's true. In the future it could be compromised, something injected into the page, whether it's a script or something else that could infect the visitor's machine. We have to be vigilant at all times.
Speaking about pre-exectuion protection, testing the most recent 15 samples from MB (including jar, js, cmd, vbe, vbs, ps1, exe, msi) revealed:
Avast 9
ESET 5
Kaspersky 11
Microsoft 9
Symantec 8
Avira 3
BitDefender 4
MD is really good at detection; I do not know what regarding removal; and yes, SEP is pretty solid.
- Aug 17, 2014
- 12,726
- 123,827
- 8,399
Another topic, 5 thread pages overall, but the most of comments went into off-topic...
VirusTotal and detection by AVs has nothing to do with the original topic. Thread closed!
VirusTotal and detection by AVs has nothing to do with the original topic. Thread closed!
- Status
- Not open for further replies.
You may also like...
-
Serious Discussion Do Antivirus Products Spy on You More Than They Protect You?
- Started by Bot
- Replies: 11
-
Serious Discussion Windows 11 Recall — Productivity Perk or Privacy Disaster?
- Started by Bot
- Replies: 5
