- Apr 6, 2016
- 441
Doctor Web — the developer of Dr.Web information security solutions — reports the detection of a spear phishing campaign with social engineering, aimed at several Russian fuel and energy companies.
The scouting
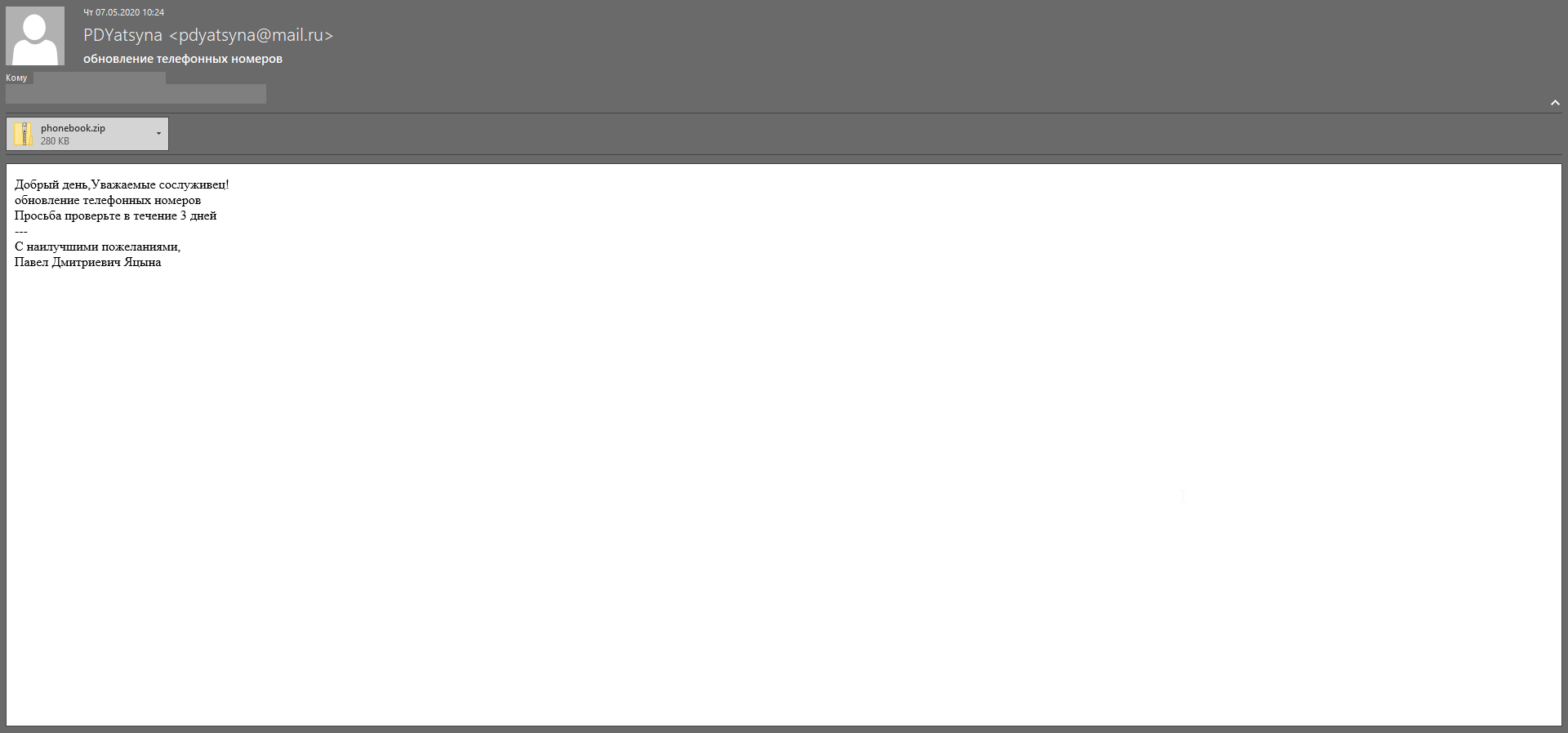
At the end of April 2020, Doctor Web virus analysts detected a spear phishing campaign where employees of Russian fuel and energy companies were receiving emails with bogus attachments. These emails contained .docx files that were distributed under the guise of an updated telephone book and downloaded two images from remote resources.
One of the images was uploaded to a user’s PC from news[.]zannews[.]com. It is noteworthy that this domain name is similar to the domain of the anti-corruption media center of Kazakhstan — zannews[.]kz On the other hand, this domain instantly recalled another well-known campaign from 2015, known as TOPNEWS, where the ICEFOG backdoor was used, and trojan C&C domains had the “news” substring in their names. Another interesting feature was the use of different request parameters or unique image names in download requests in those cases when emails were sent to different recipients. We believe this was done to collect information and identify a "reliable" recipient who is guaranteed to open an email in subsequent attacks. The SMB protocol was used to download the image from the second server, which could be done to collect NetNTLM hashes from the employees’ computers who opened the received document....
In June 2020, the attackers started to use a new domain name — sports[.]manhajnews[.]com. Our analysis revealed that manhajnews[.]com subdomains have been used in spear phishing campaigns since at least September 2019. Thus, one of the targets of this campaign was a large Russian university.
In addition, another campaign was launched in June. This time, the attached document contained information about industry development. The text in the email clearly indicated the author was not a native Russian speaker. With that, the remote server was changed to download[.]inklingpaper[.]com.
As an attempt to avoid the anti-virus detection of malicious documents, in July, hackers began using Microsoft Word documents encrypted with a password. At the same time, they have slightly modified the content of the email.
Read the Full Article
The scouting
At the end of April 2020, Doctor Web virus analysts detected a spear phishing campaign where employees of Russian fuel and energy companies were receiving emails with bogus attachments. These emails contained .docx files that were distributed under the guise of an updated telephone book and downloaded two images from remote resources.
One of the images was uploaded to a user’s PC from news[.]zannews[.]com. It is noteworthy that this domain name is similar to the domain of the anti-corruption media center of Kazakhstan — zannews[.]kz On the other hand, this domain instantly recalled another well-known campaign from 2015, known as TOPNEWS, where the ICEFOG backdoor was used, and trojan C&C domains had the “news” substring in their names. Another interesting feature was the use of different request parameters or unique image names in download requests in those cases when emails were sent to different recipients. We believe this was done to collect information and identify a "reliable" recipient who is guaranteed to open an email in subsequent attacks. The SMB protocol was used to download the image from the second server, which could be done to collect NetNTLM hashes from the employees’ computers who opened the received document....

In June 2020, the attackers started to use a new domain name — sports[.]manhajnews[.]com. Our analysis revealed that manhajnews[.]com subdomains have been used in spear phishing campaigns since at least September 2019. Thus, one of the targets of this campaign was a large Russian university.
In addition, another campaign was launched in June. This time, the attached document contained information about industry development. The text in the email clearly indicated the author was not a native Russian speaker. With that, the remote server was changed to download[.]inklingpaper[.]com.
As an attempt to avoid the anti-virus detection of malicious documents, in July, hackers began using Microsoft Word documents encrypted with a password. At the same time, they have slightly modified the content of the email.
Read the Full Article
