It's just plain simple fact and sure that can be scary to some but I do hope for most in a place like MT it ain't but instead help deliver more knowledge and strength instead of trying to ignore it and sweep it under the carpet. Garbage don't magicly disappear that way even if we all wish it.The article is technically correct, but unnecessarily fear-mongering.
I really wish that was the truth, I genuine do but reports/news is telling a very different story and do anyone actually belive something that's effective and works would die out. Asking thiefs stop stealing or politicians stop lying sorry to say don't work even if we all wish it.The type of fileless drive-by attacks they are scaring us with just don't happen anymore. They died out a few years ago.
Malvertisement, exploit-kits etc. It's more then well documented and even posted about in the news sections here on MT so anyone that's curious and want to learn something, here's a few more links that hopefully will help. Enjoy!
Drive-by attack
Equifax’s Latest Security Foil: A Defunct Web Service
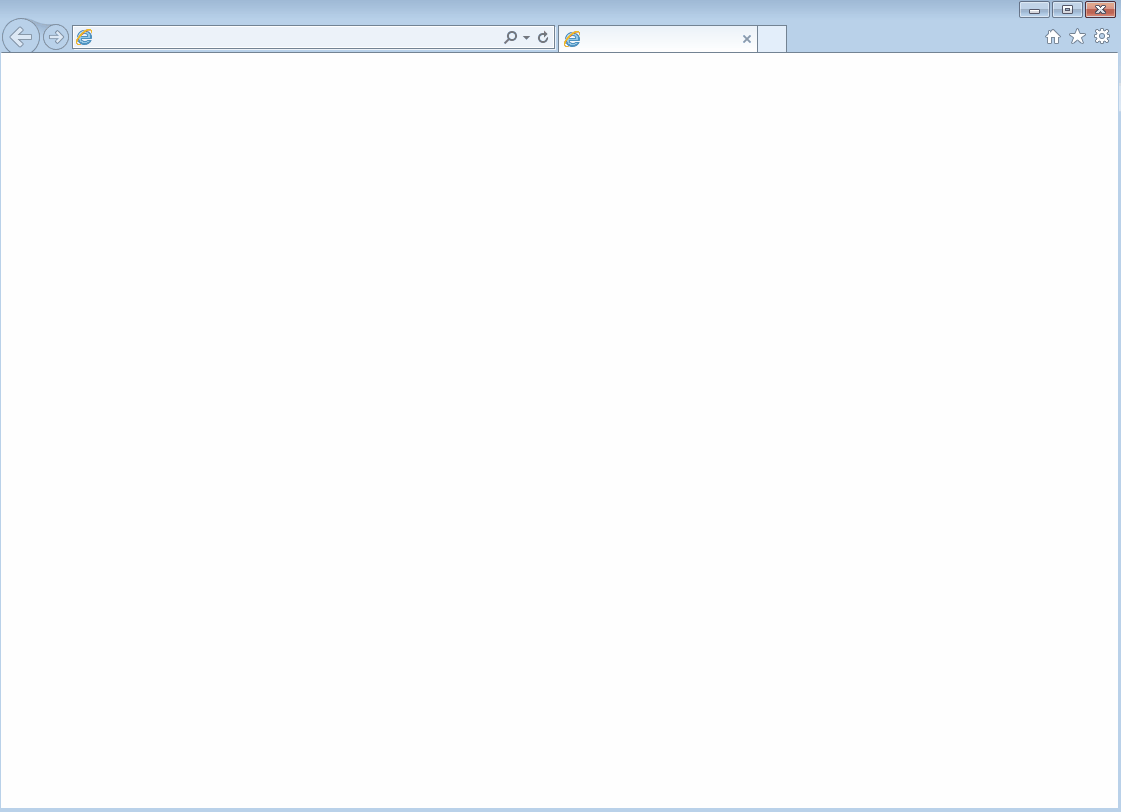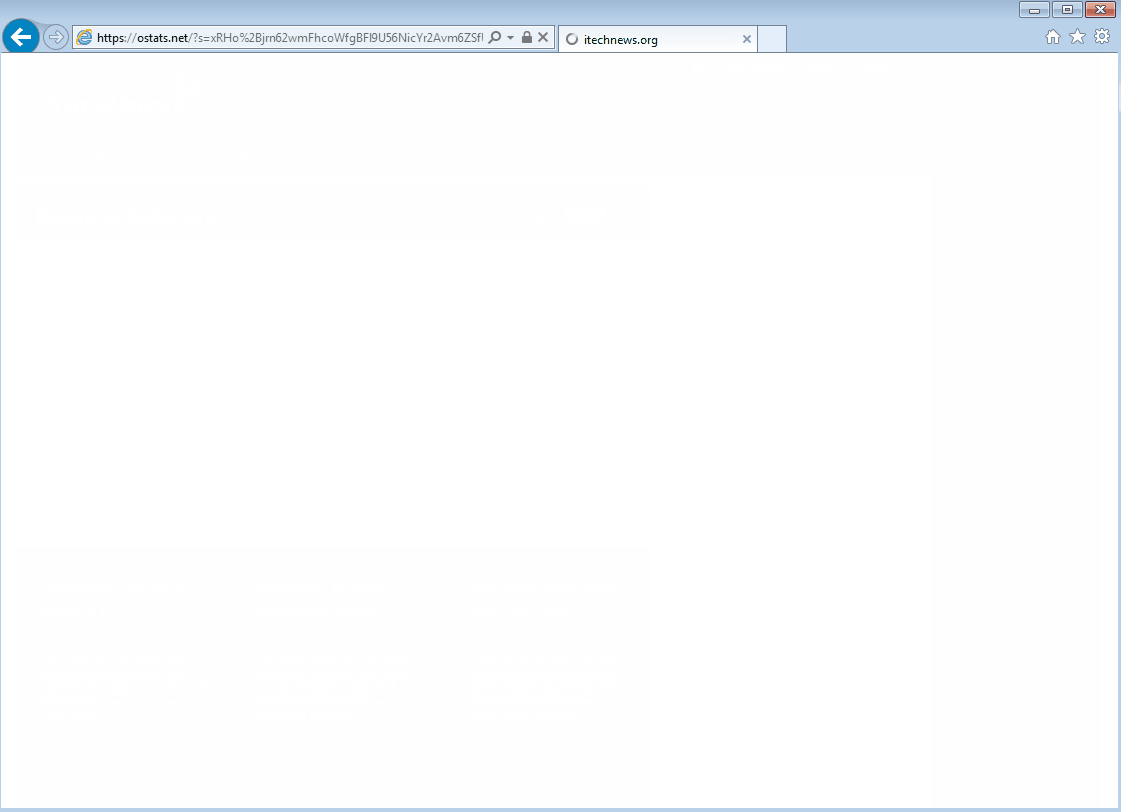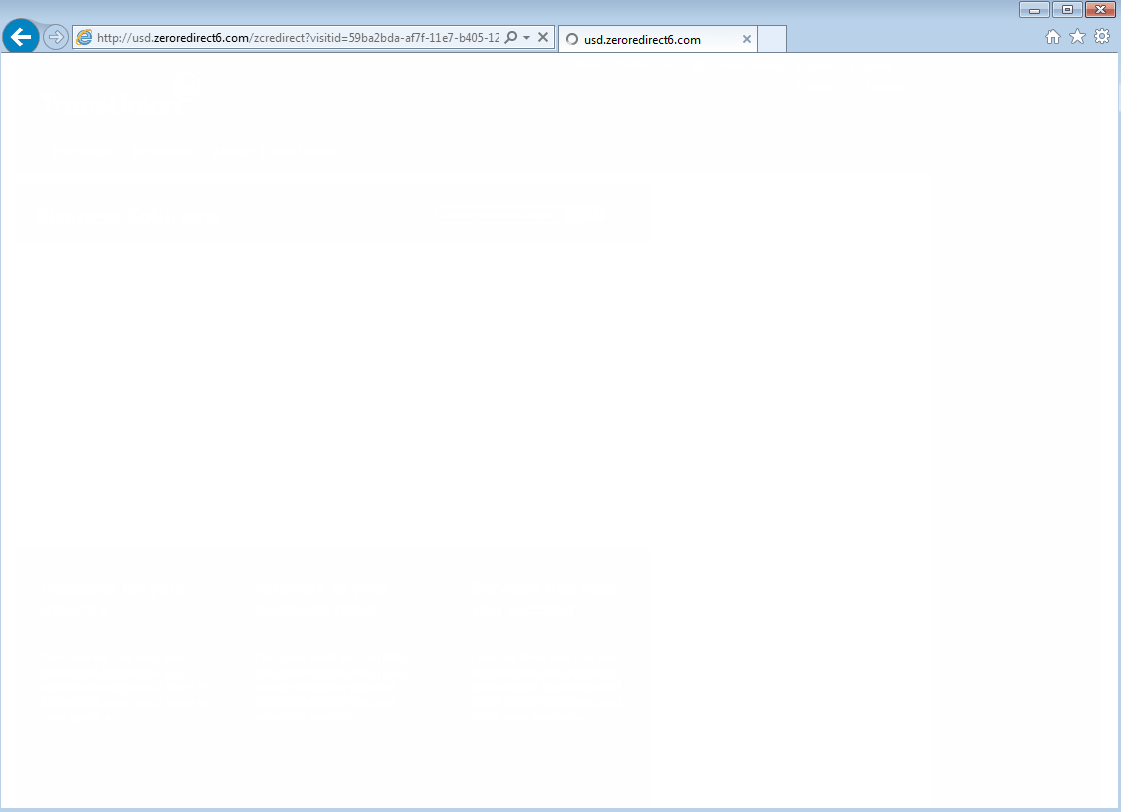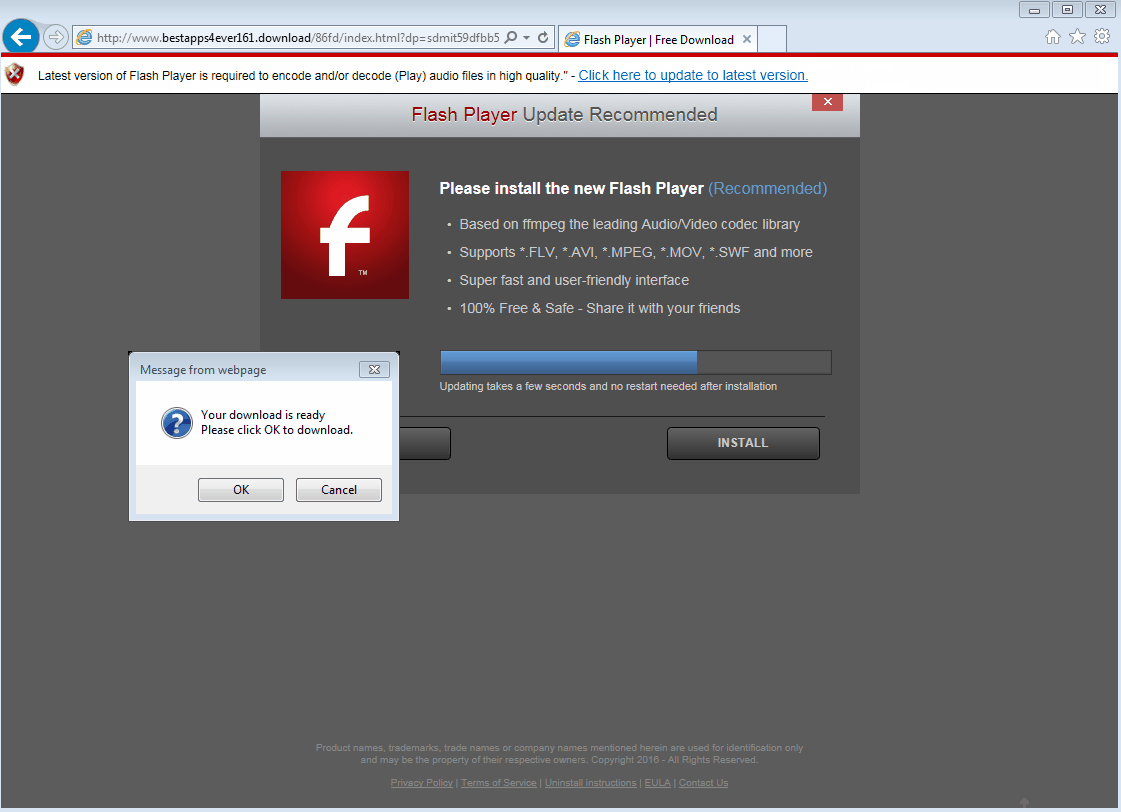
RIG Exploit Kit Infrastructure Disrupted | SecurityWeek.Com
What a script! Detecting and analyzing a Flash drive-by attack (Screenshot Demo)
Prediction of drive-by download attacks on Twitter - ScienceDirect
Last edited: