I was looking for a sample to be analyzed when I noticed this:
https://www.reverse.it/sample/7a36c...2965b69a07103a222c12d59f93425?environmentId=1
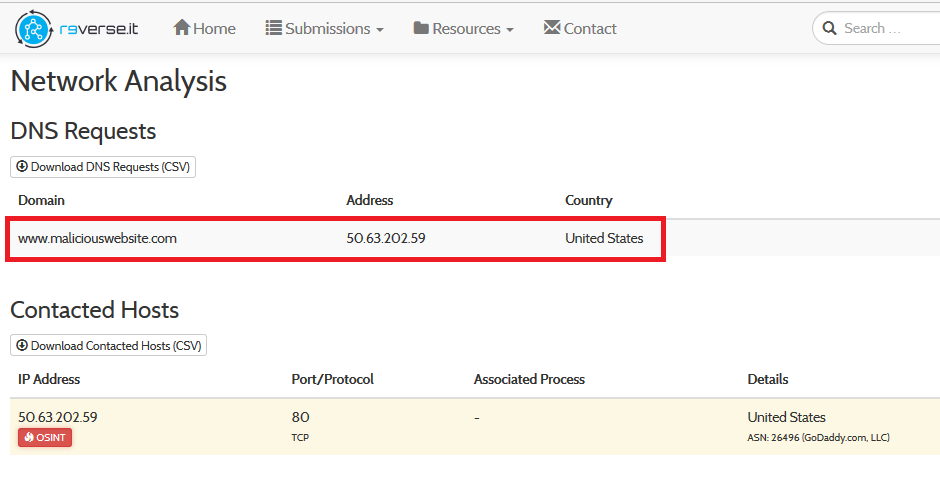
It seems to contact hxxp://w*w.maliciouswebsite.com which seems to be not active, but the strange thing it has a banal and generic name.
It doesn't seem like a real malicious site, but a non-existing site.
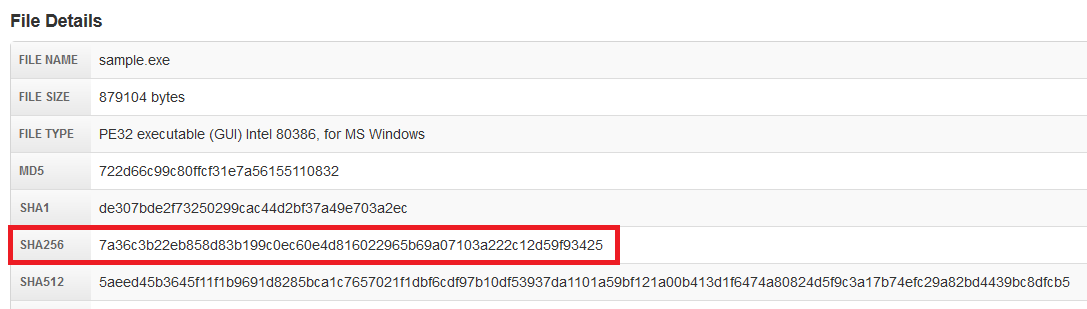
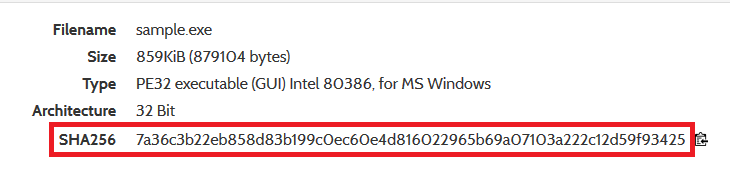
But even more strange is that I have inserted SHA256: 7a36c3b22eb858d83b199c0ec60e4d816022965b69a07103a222c12d59f93425 in the search box on Malwr, which I often use and I got:
Malwr - Malware Analysis by Cuckoo Sandbox
It seems to be the same sample
But on Malwr it doesn't generate network connection.
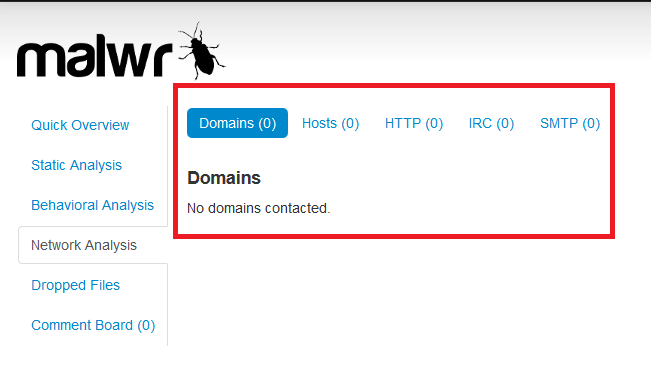
I'm a little confused, I've decided not to analyze the malware focusing myself on this strange thing: why Reverse.it online analysis confirms network connections while Malwr analysis doesn't show network connections?
The only logical explanation that I can think is: in the code of the malware probably there is a hosts comparison with Malwr indicated in the variables and if the comparison is positive, the malware cannot be fully executed inside a known online sandbox (Malwr) and it doesn't perform any network action, in fact, the report does not contain any information concerning the network activity
The same sample subjected to a not known sandbox (Reverse.it) has released a positive report about network activities.
My doubt is what is this sample, probably the malcoder was doing some test, just a hypothesis.
https://www.reverse.it/sample/7a36c...2965b69a07103a222c12d59f93425?environmentId=1
It seems to contact hxxp://w*w.maliciouswebsite.com which seems to be not active, but the strange thing it has a banal and generic name.
It doesn't seem like a real malicious site, but a non-existing site.
But even more strange is that I have inserted SHA256: 7a36c3b22eb858d83b199c0ec60e4d816022965b69a07103a222c12d59f93425 in the search box on Malwr, which I often use and I got:
Malwr - Malware Analysis by Cuckoo Sandbox
It seems to be the same sample
But on Malwr it doesn't generate network connection.
I'm a little confused, I've decided not to analyze the malware focusing myself on this strange thing: why Reverse.it online analysis confirms network connections while Malwr analysis doesn't show network connections?
The only logical explanation that I can think is: in the code of the malware probably there is a hosts comparison with Malwr indicated in the variables and if the comparison is positive, the malware cannot be fully executed inside a known online sandbox (Malwr) and it doesn't perform any network action, in fact, the report does not contain any information concerning the network activity
The same sample subjected to a not known sandbox (Reverse.it) has released a positive report about network activities.
My doubt is what is this sample, probably the malcoder was doing some test, just a hypothesis.
Last edited: