- Apr 9, 2018
- 182
Dear MalwareTips Users,
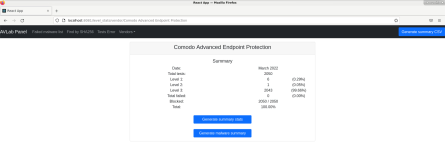
In March 2022 took place already 17th edition of the Advanced In The Wild Malware Test in which we regularly verify software to protect devices. This time we have used 2050 unique malware samples to check the effectiveness of detection and blocking malicious software. This malware number is always different as testing brings up what is rejected and what is not. Hovewer started from this month we have made more changes:
1. Improved - primary website / redesigned "AVLab Foundation :: CyberSecurity In Poland" to better compatibility with mobile devices and user experience.
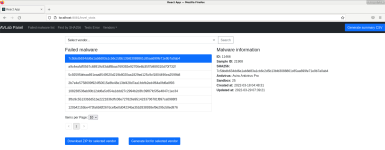
2. Added (attached file) - more detailed percentage results due to the React.js application on the backend. The results for March 2022 are available here Recent Results - AVLab Cybersecurity Foundation
3. Improved - Award website "https://avlab.pl/en/awards/" / redesigned as well,to better reward vendors who participate in testing. We added additional marketing information like "Product of the year".
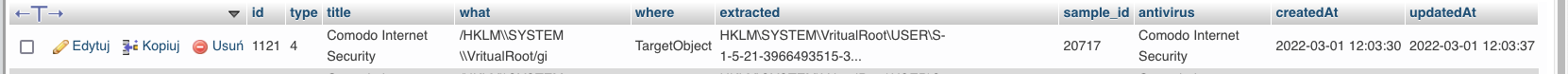
4. Improved methodology started from May 2022 we add MOTW file mark (thanks @Andy Ful)
The latest results can be found in the URL above and in the coming months we have to work on better Yara rules.
In March 2022 took place already 17th edition of the Advanced In The Wild Malware Test in which we regularly verify software to protect devices. This time we have used 2050 unique malware samples to check the effectiveness of detection and blocking malicious software. This malware number is always different as testing brings up what is rejected and what is not. Hovewer started from this month we have made more changes:
1. Improved - primary website / redesigned "AVLab Foundation :: CyberSecurity In Poland" to better compatibility with mobile devices and user experience.
2. Added (attached file) - more detailed percentage results due to the React.js application on the backend. The results for March 2022 are available here Recent Results - AVLab Cybersecurity Foundation
3. Improved - Award website "https://avlab.pl/en/awards/" / redesigned as well,to better reward vendors who participate in testing. We added additional marketing information like "Product of the year".
4. Improved methodology started from May 2022 we add MOTW file mark (thanks @Andy Ful)
The latest results can be found in the URL above and in the coming months we have to work on better Yara rules.
Attachments
Last edited: